Even when we have the best of intentions and work hard to keep our systems protected, human beings are fallible. Hackers know this, which can lead to the creation of elaborate and convincing ploys used to trick your end users into divulging credentials, allowing hackers access to your systems.
For this reason, it’s essential for any organizations using networks to send and store sensitive data to have at least one form of protection (if not more) in place—especially since no system is 100% invulnerable.
Intrusion detection software is one important piece of this security puzzle. Check out this ultimate guide on host-based intrusion detection systems (HIDS), such as the differences between HIDS and network intrusion detection systems (NIDS), define crucial security terms you might run across in your research, and provide eight featured-focused reviews of leading detection solutions on the market today (including reasons why SolarWinds® Security Event Manager is my top pick for best intrusion detection system).
What Is HIDS?
HIDS vs. NIDS: What’s the Difference?
Common HIDS and NIDS Detection Methods
How Does a Host-Based Intrusion Detection System Work?
8 Best HIDS and NIDS Tools
SolarWinds Security Event Manager (my pick)
OSSEC
SolarWinds Papertrail
ManageEngine EventLog Analyzer
Splunk
Sagan
Snort
Samhains
But Wait—What Is an Intrusion Prevention System?
How Are HIDS and SIEM Related?
Additional Definitions to Know: APT, ATP, and Threat Intelligence
Big Picture: Why Do Log Files Matter?
How Do You Maintain the Security of Your Log Files?
Which Threat Detection Tool Is Right for Me?
What Is HIDS?
HIDS stands for “host-based intrusion detection system,” an application monitoring a computer or network for suspicious activity, which can include intrusions by external actors as well as misuse of resources or data by internal ones.
How Does a Host-Based Intrusion Detection System Work?
Much like a home security system, HIDS software logs the suspicious activity and reports it to the administrators managing the devices or networks.
Most applications running on devices and networks create log messages of the activities and functions performed while a session is active. If you’re collecting and organizing all the various log files from all the various applications yourself, this can quickly become unwieldy and a drain on your resources—it’s a large amount of data to keep track of. That’s where host-based intrusion detection systems come into the picture.
HIDS tools monitor the log files generated by your applications, creating a historical record of activities and functions allowing you to quickly search them for anomalies and signs an intrusion may have occurred. They also compile your log files and let you keep them organized in ways aligning with the directory structure of your log file server, making it easy to search or sort the files by application, date, or other metrics.
The key function of HIDS tools is automated detection, which saves you the need to sort through the log files for unusual behavior once they’re organized and compiled. HIDSs use rules and policies—some of which are preset but can usually be modified and updated to suit your organization’s specific needs—to search your log files, flagging those with events or activity the rules have determined could be indicative of potentially malicious behavior.
While IT administrators will always be the ones most familiar with their systems operations and can, therefore, tailor the rules their HIDSs use when scanning the log files, I recommend also making the most of the preset policies included with your HIDS, as these have often been written by security experts to help identify common signs of intrusion. Keeping your HIDS policies up to date is incredibly important. The entire purpose of HIDS software is to make the detection process easier for administrators, freeing up your team’s resources to deal with other day-to-day responsibilities.
HIDS vs. NIDS: What’s the Difference?
While host-based intrusion detection systems are integral to keeping a strong line of defense against hacking threats, they’re not the only means of protecting your log files. Network-based intrusion detection systems, or NIDSs, are another option.
Let’s dive into the differences. First, what does a host-based IDS monitor? As you can tell from the name, HIDSs monitor the traffic and suspicious activity on the specific computer infrastructure they’re installed on. NIDSs, on the other hand, monitor network-based traffic and activity. Both systems work by surveying log and event messages the system generates, but NIDSs also examine packet data as information moves across a network. Another way the two forms of intrusion detection system differ is: NIDSs work more in real time, tracking live data for signs of tampering, while HIDSs check logged files for evidence of malicious activity.
A solid security regimen will include both a HIDS and a NIDS, as they work together in a way meant to be complementary. NIDSs allow for faster response times to potential security threats, as real-time packet data monitoring can trigger alerts if something suspicious occurs. HIDSs allow you to examine historical data for patterns of activity, which is useful for savvy hackers who often vary their methods of intrusion to be more unpredictable and therefore less easily traced. Having the historical record of activity allows you to examine potentially malicious behavior from a big-picture, bird’s-eye view, giving you the ability to identify patterns that might not trigger alerts in granular, real-time detection systems. Implementing both types of intrusion detection system jointly helps to keep your data secure from several different angles.
Common HIDS and NIDS Detection Methods
There are two means by which HIDSs and NIDSs do the actual intrusion detection on your systems: anomalies and signatures. Each type of IDS can employ either strategy, which gives each option certain advantages.
Anomaly-based detection looks for unusual or irregular activity caused by users or processes. For instance, if your network was accessed with the same login credentials from several different cities around the globe all in the same day, it could be a sign of anomalous behavior. A HIDS using anomaly-based detection surveys log files for indications of unexpected behavior, while a NIDS monitors for the anomalies in real time.
The signature-based form of detection monitors data for patterns. HIDSs running signature-based detection work somewhat similarly to antivirus applications—which search for bit patterns or keywords in program files—by performing similar scans on log files. Signature-based NIDSs, on the other hand, function more like firewalls, except where firewalls run checks on keywords, packet types, and protocol activity entering or exiting the network,
NIDSs run similar checks on traffic moving within the network. Much like choosing between a host-based IDS and a network-based IDS, anomaly- and signature-based detection strategies aren’t mutually exclusive. Each system complements the other, creating a more comprehensive intrusion detection system.
8 Best HIDS and NIDS Tools
Even smaller networks can create a substantial amount of log data every day, which means you’ll need a HIDS capable of sorting and searching through large amounts of data quickly. A slow HIDS tool won’t do you a whole lot of good, as it might not be able to keep up with the volumes of information your log server accrues each day. While a slick interface or dashboard can be tempting, it’s not worth the hassle of laggy search functions. The best HIDS tools will bring you the best of both worlds—speedy monitoring and intuitive interfaces to make your job easier. 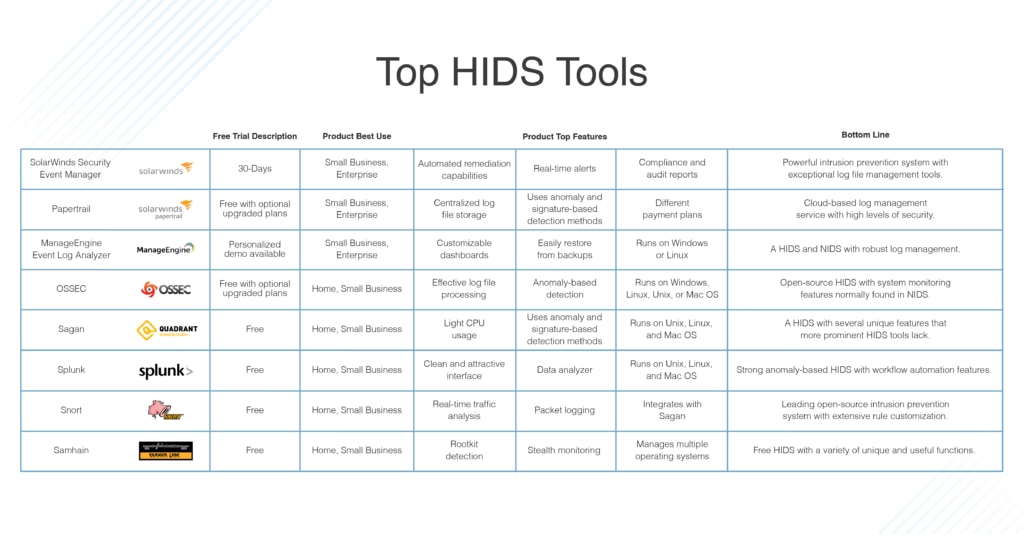 I created this list of what I think are some of the best HIDS software options, with a few NIDS tools thrown in for good measure. Some of the tools listed here are free, which means they might not have the same features the paid options have. However, I included them because of how exceptionally fast they work. Some of the tools are also much more comprehensive, while others are designed solely to comply with certain data security standards. Your specific needs — and the size of the systems you are looking to monitor — will help determine which tools are the best fit for your company.
I created this list of what I think are some of the best HIDS software options, with a few NIDS tools thrown in for good measure. Some of the tools listed here are free, which means they might not have the same features the paid options have. However, I included them because of how exceptionally fast they work. Some of the tools are also much more comprehensive, while others are designed solely to comply with certain data security standards. Your specific needs — and the size of the systems you are looking to monitor — will help determine which tools are the best fit for your company.
1. SolarWinds Security Event Manager (Free Trial)
SolarWinds Security Event Manager (SEM) is a HIDS with a robust lineup of automated threat remediation tools—which, if you’ve been paying attention to the acronyms, technically makes this option an IPS. It also comes with a toolset of useful log management features. Security Event Manager makes it easy to constantly monitor, forward, back up, or archive log files, and includes built-in transit and storage encryption.
© 2023 SolarWinds Worldwide, LLC. All rights reserved.
I really like SolarWinds products for their automated alerting systems, which are not only effective but also customizable, meaning you don’t have to perform checks by hand—unless you want to: in addition to the automated features, this tool includes the option for running manual checks on data integrity. It also uses a centralized log analysis system to detect potential APT activity. Pulling and analyzing data from systems across the network, the software creates a cohesive monitoring environment to track down the signs of APT cyberattacks to root them out.
Another useful feature is the ability to run audit reports to check how closely aligned you are with a wide range of data security and integrity standards, including PCI DSS, SOX, HIPAA, ISO, NCUA, FISMA, FERPA, GLBA, NERC CIP, GPG13, and DISA STIG. SolarWinds SEM can collect log data from most operating systems, including Linux and Unix, though it can only be installed on Windows servers. It will, however, collect log data from other operating systems, including Linux and Unix.
All in all, SEM is an incredibly comprehensive intrusion detection system for functionality and customization with powerful security tools. You can also download a 30-day free trial to test it out before purchasing.
2. OSSEC
© COPYRIGHT © 2023 OSSEC PROJECT TEAM
This free application is, in my opinion, one of the best open-source options available. While technically a HIDS, it also offers a few system monitoring tools you’d be more likely to find in a NIDS. When it comes to log data, OSSEC is an incredibly efficient processor, but it doesn’t have a user interface. You can get around this by running an open-source dashboard like Kibana or Graylog.
OSSEC organizes and sorts your log files and uses anomaly-based detection strategies and policies. Because it’s an open-source application, you can also download predefined threat intelligence rule sets from the community of other users who have OSSEC installed. If you need technical support, help from the active user community is free to access, and Trend Micro—which produces OSSEC—also offers a professional support package for a cost.
OSSEC can be installed on a wide variety of operating systems, including Windows, Linux, Unix, and Mac OS. The tool monitors event logs and the registry for Windows systems, and on the other operating systems, it’ll guard the root account. OSSEC offers compliance reporting functions as well, and its log file detection methods scan for unusual behavior or unauthorized changes that could specifically cause compliance issues.
3. SolarWinds Papertrail
©2023 SolarWinds Worldwide, LLC. All rights reserved.
Papertrail™ is another SolarWinds product, and it’s a little different than your typical HIDS or NIDS. This cloud-based management service aggregates your log files and stores them, so you don’t have to worry about volumes of log data eating up storage on your systems. By centralizing log file storage, Papertrail provides easy access and rapid search functions for your entire data archive.
The tool uses both anomaly- and signature-based detection strategies can manage a variety of file types (including Windows event logs, firewall notifications, and more), and sends out threat intelligence policy updates with new information learned from cyberattacks attempted on other users.
Like other SolarWinds products, Papertrail allows you to create and modify your own rules and policies. Papertrail encrypts log data whether in transit or in storage, and requires authentication to access the files, so if any intrusive attempts are made, you’ll be provided with a report detailing whose credentials were used. There are several subscription tiers for Papertrail storage, including a free option, so you can tailor pricing plans to suit the size of your company.
4. ManageEngine EventLog Analyzer
© 2023 Zoho Corporation Pvt. Ltd. All rights reserved.
ManageEngine EventLog Analyzer is a comprehensive security application with both HIDS and NIDS capabilities. It also centralizes your log files and metadata in one location, and if it detects log files have been altered inappropriately, you can automatically restore your log files from backups. Similar to Papertrail, EventLog Analyzer protects log files with encryption and compression protocols and requires user authentication to access the data.
Another perk of this product is the customizable dashboard, which allows you to create different screens and adjust which features are assigned to different user groups, thereby tailoring your data collection to align with what’s most relevant or important for maintaining your business’s security standards. EventLog provides reporting capabilities as well and lets you create compliance reports for a number of data security standards, including PCI DSS, FISMA, GLBA, SOX, HIPAA, and others. The compliance reports are also customizable, so you can adjust existing reports to meet the requirements of new or upcoming regulatory acts.
EventLog Analyzer can be installed on Windows or Linux and easily integrates with ManageEngine infrastructure management tools, which give you greater control and monitoring over your network’s performance and functionality. As far as pricing goes, your first five devices are free to monitor—a nice advantage if you’re running a network at home or for a very small business. Those managing larger networks can request a quote on the ManageEngine website.
5. Splunk
© 2005 – 2023 Splunk Inc. All rights reserved.
There are several versions of Splunk available, ranging from the free baseline application—which is an excellent anomaly-based HIDS—to paid options with a variety of NIDS features. The paid versions of Splunk, which include cloud-based options, offer automated features to respond immediately to detected threats, giving them IPS capabilities. Splunk also boasts an excellent user interface and dashboard with useful visualizations.
All versions of Splunk can be installed on Windows, Linux, and Mac operating systems, and each includes a strong data analyzer for easy sorting and searching through your log data. Different free trial periods are available for the different tiers of Splunk, allowing you to try before you buy.
6. Sagan
© Copyright 2009-2023 Quadrant Information Security, et al.
Sagan is another free option using both anomaly- and signature-based detection strategies. Sagan is customizable and allows you to define automatic actions for the application to take when an intrusion contingency is triggered. It has a number of tools other HIDSs don’t offer, including an IP geolocation feature to create alerts if activity from multiple IP addresses appears to be stemming from the same geographical location. Sagan also allows for script execution, which means it can function more like an IPS.
Sagan was written to easily integrate with Snort, a NIDS (see below), and when paired together, they create a powerful, open-source HIDS and NIDS combo.
While Sagan can only be installed on Linux, Unix, and Mac operating systems, it can still collect Windows event log messages, and it’s a relatively lightweight option and won’t be too taxing on your server’s CPU.
7. Snort
©2023 Cisco and/or its affiliates. Snort, the Snort and Pig logo are registered trademarks of Cisco. All rights reserved.
Snort is an excellent open-source NIDS application chock-full of features. Not only does it work as a robust intrusion detection tool, but it also includes packet sniffing and logging functionality.
Similar to how OSSEC allows you to download rules and policies from the user community, predefined rules for Snort are available on the website, with options to sign up for subscriptions to make sure your threat intelligence policies are kept up to date. Snort’s rules can also be customized to suit your specifications, but the basic set of policies is a good place to start. The events these policies detect include buffer overflow attacks, CGI attacks, OS fingerprinting, and stealth port scans. The rule set includes both anomaly- and signature-based policies, making the application’s scope fairly broad and inclusive. And, as mentioned above, Snort can be seamlessly combined with Sagan for a more comprehensive open-source monitoring solution.
8. Samhain
© Ourselves. All rights reserved.
Another free HIDS option, Samhain offers file security functions like integrity checks, monitoring, and analysis. Perhaps its most unique feature is its stealth mode monitoring, which essentially allows it to run without a hacker noticing. In many cases of cyberattacks, the intruders can identify and stop detection processes, but their proprietary cryptographic function prevents hackers from noticing it’s active and performing sweeps. The tool uses a PGP key to protect central log files and backups, as well.
Other features include the ability to perform rootkit detection and port monitoring and to detect hidden processes running on your devices. It can manage multiple systems—even if they’re running different operating systems—from a centralized interface. Samhain can be installed on Linux, Unix, and Mac operating systems, and on Windows through Cygwin.
But Wait—What Is an Intrusion Prevention System?
While I’ve explained how HIDSs and NIDSs play essential roles in keeping your network protected, they’re both only detection systems. Once they’ve identified suspicious or malicious activity, it’s up to you to address the issue, keep your data secure, and prevent or mitigate potential damage.
While you can manually work to prevent and mitigate these threats, doing so can be both time consuming and inefficient use of resources. In my opinion, the better option is to invest in network management tools to make it easier to block and remove intruders from your systems. Combining an intrusion detection system with threat remediation countermeasures creates a fully rounded package called an intrusion prevention system (IPS)—a bit of a misleading name, as IPSs technically work to seal off detected breaches rather than staving off breaches before they start. Learn more about the differences between IDS and IPS in my other article.
It can be extremely hard, if not outright impossible, to keep the boundaries of your network airtight and completely secure, as so many variables fall outside of your control. Even the best efforts to create a secure network environment won’t prevent user errors, whether committed intentionally or not. Unfortunately, no protection system—be it a firewall or an antivirus application—is guaranteed to be 100% safe all the time, so IT administrators must be vigilant and leverage the right intrusion detection tools to support their efforts.
How Are HIDS and SIEM Related?
SIEM is a fairly common acronym in computing, one you’re bound to come across in the world of network security tools. It’s short for “security information and event management.” In basic terms, SIEM technology uses a combination of security information management (SIM) and security event management (SEM) tools.
The difference between the two aligns with the difference between HIDS and NIDS: SIM tools track log files for patterns over time, and SEM tools examine data in real time. When you use both in tandem to monitor your data, you’re technically using a SIEM system. By using IDS and SIEM tools together, you’re also taking a variety of strategic measures to maintain data safety.
Additional Definitions to Know: APT, ATP, and Threat Intelligence
One particularly malicious security issue you may come across when researching HIDS solutions is called an advanced persistent threat (APT), which involves a hacker who can access an organization’s systems or networks over an extended time without detection. An advantage of host-based intrusion detection tools is their design to locate and stop APTs.
An APT is counteracted through what’s called an ATP, or “advanced threat protection,” system (all the acronyms are fun, I know!). ATP systems are essentially the same thing as intrusion detection systems, but with more emphasis on what’s called threat intelligence.
One advantage of ATP systems is the “central threat awareness services” providers offer. These services—which can be included as an ongoing subscription or with an additional up-front purchase price—will periodically send out updates to keep ATP systems current with information about positively identified attack vectors culled from aggregated data logs and reports from other subscribers. The centralized database of attack vectors allows all subscribers to benefit, so even if your systems haven’t experienced a certain form of intrusion, they can still be prepared to identify it. Some HIDS providers include similar services, while others operate along more community-driven models, but by and large, ATP providers tend to offer more robust threat intelligence features.
So, what’s threat intelligence? Threat intelligence in intrusion detection systems refers to the process of checking data search terms and system tests against a series of rules to detect the presence of network activity that should be investigated. While artificial intelligence can be used to create coded checks or modifiable rules set as policies, the efficacy of policies created by automated systems depends entirely on the interference rules built into the actual AI. AI systems can be super-helpful, but you’ll want to make sure the groundwork is solid before relying too heavily on them.
Big Picture: Why Do Log Files Matter?
The stakes of keeping data protected and secure are higher than ever. The sheer amount of log files generated across a network can be intimidating, but that’s why using a HIDS, NIDS, or other intrusion detection system is so important. If you don’t properly monitor and maintain your log files, your company could be at risk.
You only need to look at some of the recent data breaches and the millions of dollars organizations have been forced to pay out as a result of litigation to get a sense of how inadequate security can affect your company’s bottom line and reputation. In light of the privacy concerns brought up by these leaks, data protection issues are often incorporated into contracts. Several industries have also instituted data and security standards, which not only helps stakeholders feel more secure but is better for your business. Data integrity standards include requirements regarding log file maintenance companies must follow to be in regulatory compliance. Certain standards require log files be securely kept and archived for years.
How Do You Maintain the Security of Your Log Files?
Since log files can create event messages showing indications of intrusion, hackers often alter them to remove signs of malicious activity. HIDSs are an integral part of a comprehensive security lineup because they can back up files to a log server running checks for unauthorized modifications. Using a log server is also key for managing compliance with data security standards.
Using a HIDS as part of your security lineup won’t do you much good if the data it’s monitoring has been tampered with. To adequately protect your log files, you also need to take measures to ensure you have a proper authentication system in place. If your HIDS tools are simply monitoring the log files, the automated system has no way to tell what constitutes authorized or unauthorized access unless it’s also tracking the permissions associated with user accounts. By tracking permissions, you can tell who should and should not have the ability to access the files on the server and whether changes to user provisioning is needed.
Which Threat Detection Tool Is Right for Me?
This host intrusion detection system comparison is meant to equip you with the information you need to determine which HIDS tools are most suited to the systems you manage. The size of your network and your choice of operating system on your log servers, along with how hands-on you want to be in managing every detail of your intrusion detection security solutions, are all factors that will play a part in deciding which program—or combination of programs—is the best fit for your business.
If you would like or benefit from a premium intrusion detection product, I strongly recommend you consider Security Event Manager. Or if you’re interested in running cloud-based services, then I suggest you look into Papertrail or Splunk Cloud. The other IDS solutions I reviewed here will appeal to admins who like open-source applications that allow them to tinker. And if you’re not entirely sure which tool to try, you can always download the free trials.


