Varonis DatAdvantage is a specialist software solution designed to aggregate information associated with users, permissions, access events, and data. It gives you visibility into your file system permissions, recommendations, audit information, and modeling, and serves as a base for products that enhance its capabilities.
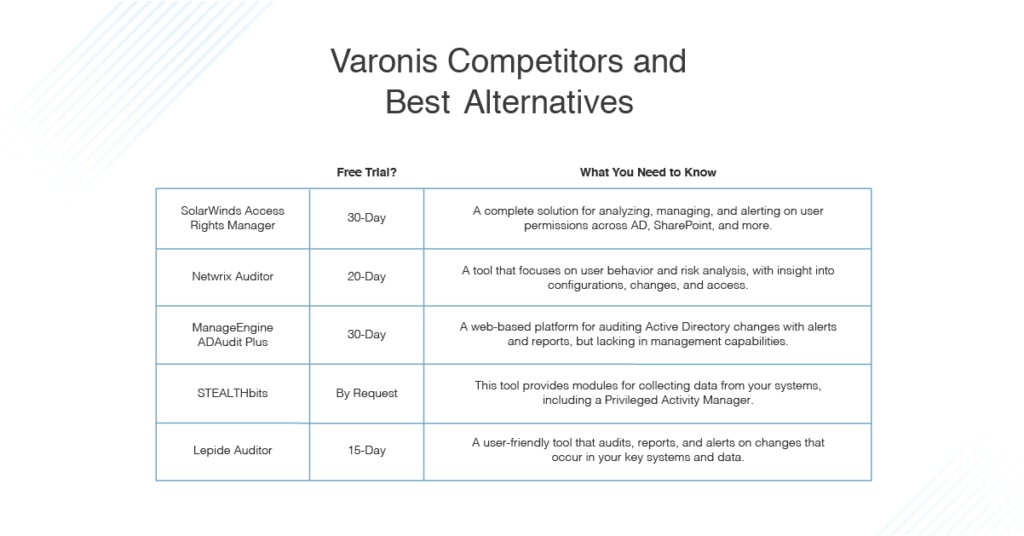
This guide will consider why you might choose an alternative to Varonis, considering Varonis disadvantages and the most notable benefits of certain Varonis competitors. SolarWinds® Access Rights Manager tops my list of best Varonis alternatives. It provides an impressive range of functionalities—all of which are sophisticatedly executed and genuinely useful—delivered in a user-friendly package.
Feel free to jump ahead to the specific product review:
- SolarWinds Access Rights Manager
- Netwrix Auditor
- ManageEngine ADAudit Plus
- STEALTHbits
- Lepide Auditor
Top Varonis Competitors
1. SolarWinds Access Rights Manager
SolarWinds has been around for two decades and is a well-known name among network administrators. It has a long-standing reputation for making some of the best network administration solutions available. The company’s product range is varied, covering network management, security, application management, and everything in between. SolarWinds even offers free tools, including a subnet calculator and TFTP server. It’s unsurprising, then, that it offers a quality tool for access rights management.
SolarWinds Access Rights Manager (ARM) is easy to use, highly advanced, and scalable. This tool was created to help network administrators manage access permissions and user authorizations in an effective and economical way, with a focus on taking the hassle out of user provisioning and deprovisioning, monitoring, and tracking.
ARM’s range of functionality is seriously impressive and certainly rivals Varonis. Like Varonis, it includes Active Directory monitoring, which lets you track and identify any changes to the Group Policy and AD. With visibility into any settings alterations and immediate flagging of unauthorized behavior, it’s easy to spot malicious activity. ARM goes beyond Varonis, though, by providing Windows Server change monitoring, which lets you view who has what level of access to each component.
One of the tool’s best—and more differentiating—features is its permissions analysis. This feature takes data security to the next level, allowing you to combine user management with analysis of which users have accessed file servers and services. This is invaluable when it comes to helping prevent insider breaches. Though Varonis can give you great visibility into your access permissions, the analysis is up to you, which means it might take longer for you to detect these insider breaches.
One of the ways ARM exceeds Varonis is in the delivery and design of its user interface. The user management dashboard is intuitive and gives you maximum control. You can create, edit, delete, activate, and deactivate a user’s access to folders and files, in addition to accessing role-specific templates for rapidly assigning access to specific network resources. You can delete and add users in a matter of clicks, all from within the user management dashboard. Though Varonis is working to improve its user interface, it still has a long way to go before it can compete with ARM’s.
One of the disadvantages of Varonis is its pricing. Figuring out how much you can expect to pay for the service can be surprisingly tricky. There are no baseline or average prices available on the Varonis website. Instead, you need to fill out a detailed form to get any sense of what you may have to pay. That quote may not even include the extra modules you will need to purchase for added functionality. ARM, on the other hand, clearly states its baseline price on the product page. If you are looking to find out your exact cost, you can get an online quote.
ARM allows you to create organizational categories, with multiple folders and groups, which can then be assigned to data owners. Varonis doesn’t offer this functionality. Moreover, ARM facilitates permissions management and monitoring for Microsoft SharePoint, Microsoft Exchange, Microsoft OneDrive, file share permissions, and SAP R/3. Varonis offers these services for Microsoft Exchange, OneDrive, and SharePoint, and then only if a separate module is purchased.
In terms of support, ARM once again takes the lead: in addition to free 24/7 technical telephone support for one year with a purchase of a license, SolarWinds licensed products also come with a year of free upgrades for that product with the ability to renew maintenance after this time (which is less expense than purchasing a new license after maintenance has expired). Varonis also offers 24/7 support, but as a paid service, which also includes paid software updates.
Overall, SolarWinds provides a more intuitive and cost-effective experience, with a wider range of functionalities than Varonis. A 30-day free trial of SolarWinds ARM is available.
2. Netwrix Auditor
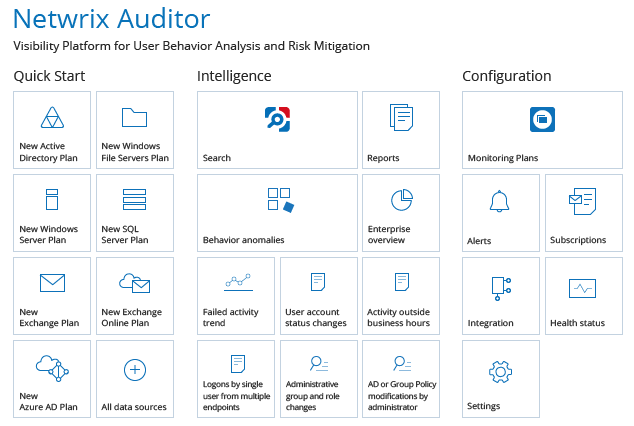
Netwrix Auditor is one of the best Varonis competitors on the market. This tool focuses on user behavior and risk analysis while providing you with insight into configurations, changes, and access. Netwrix Auditor features applications for Office 365, Windows file servers, EMC storage devices, Azure AD, Exchange, SharePoint, SQL Server, Oracle Database, VMware, NetApp, Nutanix Files, and more. This range not only exceeds that offered by Varonis (which does not integrate with VMware, for instance), but it also places Netwrix Auditor among the most versatile Varonis competitors.
Netwrix Auditor is a cleverly designed tool with notable features. These include change, access, and configuration reports, which allow you to rapidly acquire the necessary information, so you can keep auditors, stakeholders, and senior team members informed. This saves you loads of time otherwise spent toiling over spreadsheets, log files, and scripts. While Varonis does offer some reporting capabilities, it doesn’t include change reports.
The alerts system is another major benefit of Netwrix Auditor. Though most access management solutions offer some form of alerting, the Netwrix offering is more sophisticated than the alerting systems in many other products, though similar to the Varonis system. With Netwrix Auditor, as soon as suspicious activity is identified, you will receive an immediate alert. There are two types of alerts—threshold-based alerts and those based on interactive search. Threshold-based alerts will inform you if thresholds specified by you have been breached. Interactive search alerts, on the other hand, are based on searches you’ve made in the past.
For example, if you used interactive search to identify an administrator granting permissions directly instead of doing so through group membership, you can establish an alert for the future based on this search. If such an event occurs again, you’ll be notified.
This interactive search capability is one of Netwrix Auditor’s best features and one that helps it stand out from Varonis. Because it was designed to resemble the Google search engine’s functionality, it’s familiar and easy to use. You can use the search capability to complete a range of tasks, including investigating the activity of a rogue admin, tracking down the root cause of an issue or service failure, and monitoring contractors. Though Varonis does have an intelligent enterprise search engine, it is less easy-to-use and less sophisticated than the Netwrix engine.
Like Varonis, Netwrix Auditor excels at behavior anomaly discovery, which is easily configured. This functionality assists with detecting data theft and tampering, identifying acts of cyber sabotage, and uncovering potential privilege abuse.
Unlike Varonis, Netwrix Auditor has a straightforward deployment and configuration process. Most users agree the program can be up and running in just a few hours. The core functionalities are either ready to use on an out-of-the-box basis or able to be quickly configured during the installation process. You won’t need any professional assistance to do this, which gives Netwrix Auditor a clear advantage over Varonis.
The Netwrix Auditor pricing model gives you the choice between a subscription or a perpetual license. Most applications are licensed per enabled AD user. However, you’ll need to contact Netwrix Auditor directly for a quote. A 20-day free trial is available; you can also request a personal demo.
3. ManageEngine ADAudit Plus
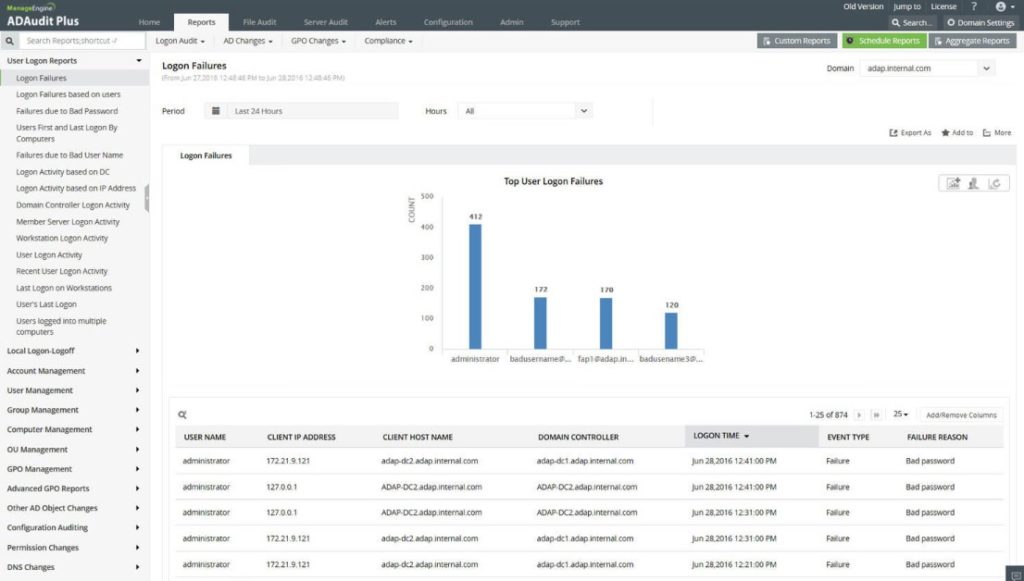
ManageEngine ADAudit Plus is a web-based platform for auditing Active Directory changes. It helps you ensure your critical network resources, such as domain controllers, are appropriately audited, tracked, and reported on. ADAudit Plus provides a high level of detail, including information on AD objects, groups, users, OU, GPO, computer, DNS, AD schema, and configuration alterations.
This is a feature-rich program with more than 200 event-specific email alerts and GUI reports. The customizability of reports—which allows you to create and set profile-based reports, as well as report from archived data—gives ADAudit Plus an advantage over Varonis, which offers limited report customizability. Varonis also falls behind when it comes to GUI reports, which it doesn’t offer.
The ability to report from archived data makes ADAudit Plus stand out from Varonis and its competitors. This functionality was designed to make archived audit data easily understood by common systems. ADAudit Plus recognizes the importance of archiving to forensic reporting and analysis, resource capacity planning, and isolation of any suspicious users while corroborating their involvement in previous security attacks. The tool attempts to rectify the issues associated with typical archiving, including data storage issues by storing AD change data in the domain controller’s security log, up to a maximum of 4GB. The software also allows you to archive management options, such as “do not overwrite” and “overwrite as needed.” Though Varonis also highlights the importance of archiving data through its products, its archiving is less sophisticated, and the tool follows more standard archiving practices than those offered by ADAudit Plus.
The ADAudit Plus consolidated audit trail reporting feature is especially useful, providing you with a search utility that consolidates three different audit summaries—actions by account, login history of the account, and object history. These summaries can be generated for any user account over a given period. Each summary element serves as a link, which when clicked shows an in-depth and elaborate report providing further details. Consolidated audit summaries can also be generated for any computer object or group, to improve the investigation and analysis of incidents. While Varonis offers unified audit trails that you can sort and search through, it doesn’t offer these summaries, meaning that it requires more manual efforts to achieve the same level of insight that you can get with ADAudit Plus audit trail reporting.
The ADAudit Plus alerts system is sophisticated, notifying you of security events across the entire Windows Server environment in real time, so you’re not out of the loop. Alerts can be created in a few clicks and can be configured to notify you via email, text, or both—an advantage as compared to Varonis and some of its competitors who do not offer text alerts. The ADAudit Plus alerts system is built to detect brute-force attacks, identify suspicious behavior or logins, detect ransomware, and safeguard your system by notifying you when a user is added to a security group. Alerts can be fine-tuned, defined by granular thresholds, and tweaked to suppress redundancy. This helps reduce false positives and alert fatigue.
Like Varonis, ADAudit Plus doesn’t offer management capabilities for Active Directory permissions or file server permissions. It also doesn’t support assigning data ownership to organizational categories or the submission of permissions requests by employees, the second of which Varonis does support. However, in terms of reporting functionalities, ADAudit Plus is an impressive Varonis alternative. You can download a 30-day free trial here.
4. STEALTHbits
STEALTHbits is another popular alternative to Varonis. Unlike Varonis and many of its competitors that offer one comprehensive solution, STEALTHbits offers five main productsthat are combined to form a full, sophisticated data security solution. These are StealthAUDIT, StealthDEFEND, Privileged Activity Manager, StealthINTERCEPT, and StealthRECOVER.
The STEALTHbits data governance solution encompasses StealthAUDIT, StealthDEFEND, and Privileged Activity Manager. The solution is delivered in five stages: Discover, Collect and Analyze, Monitor, Restructure, and Govern. The functionalities are designed to contribute to the achievement of each of these stages, giving the program a logical and strategic quality and making the user experience feel highly purposeful and driven.
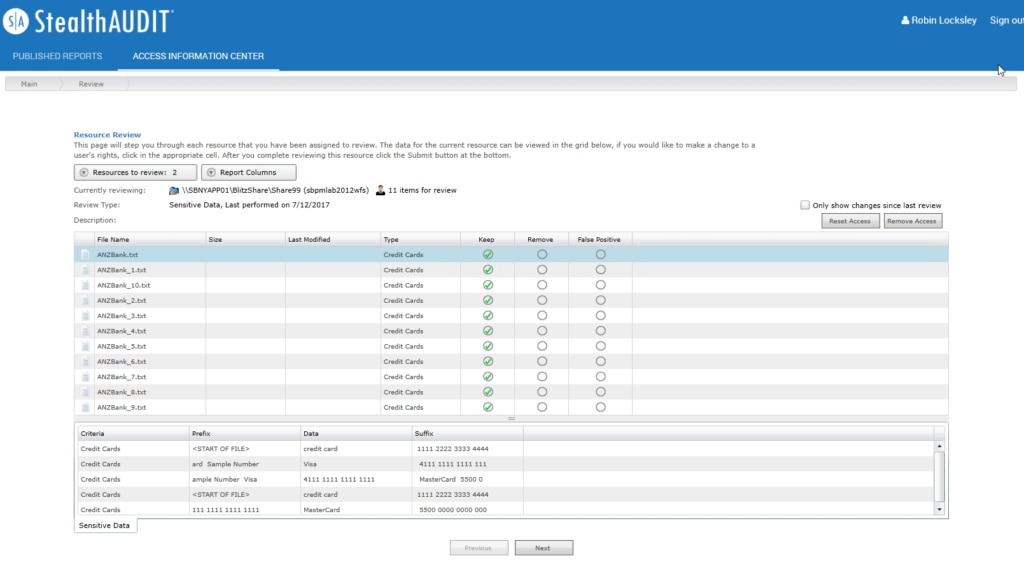
StealthAUDIT, the reporting and governance component of the STEALTHbits range of data security tools, automates the process of collecting and analyzing important data, so you can resolve critical issues and answer difficult questions relating to the security of your IT assets. This includes directories, data, and systems. StealthAUDIT has more than 40 built-in modules for collecting data, supporting both cloud-based and on-premises platforms, like Varonis, and covering everything from Office 365 to operating systems. Unlike Varonis, the software uses agentless architecture, with data collectors delivering a wizard-driven interface to assist with configuration. This facilitates rapid and accurate data collection from numerous sources.
One of the areas where StealthAUDIT more closely aligns with Varonis is when it comes to correlating data and automatically fixing any potential security risks that are detected. Specifically, StealthAUDIT includes analysis modules, which facilitate the correlation of existing and alternative data sources and enable users to inject business logic and rules, undertake historical trending and exportation, and much more. Further, the StealthAUDIT action module framework allows you to automatically remediate conditions across your entire organization and environment. This means you can fix access issues and tie processes together effortlessly. The Varonis Automation Engine offers a similar functionality, automatically fixing any security gaps it detects, repairing permissions, and more.
StealthDEFEND accelerates the speed of threat detection as compared to Varonis, delivering threat detection and response capabilities for file systems and Active Directory in real time. With advanced attack detection, you can identify and respond to specific techniques, procedures, and tactics being leveraged by attackers. Like Varonis and StealthAUDIT, StealthDEFEND is also highly automated, with the ability to respond to threats automatically according to a catalog of customizable and preconfigured responses. The program also supports automatic context injection, letting you tag privileged users, data, resources, and groups.
Finally, we have the STEALTHbits Privileged Activity Manager. This highly versatile tool goes far beyond Varonis, letting you grant specific activity-based permissions to accounts and auto-provision temporary accounts when necessary. The program benefits from preconfigured activities for common tasks, saving you time otherwise spent configuring them during the initial setup. To keep this capability from compromising your systems, multi-tiered approvals let you certify access is limited and appropriate.
One of the most notable features of Privileged Activity Manager is the ability to enforce accountability by having sessions recorded and played back. This can be especially useful when giving evidence during investigations or audits. Unfortunately, Varonis doesn’t offer this functionality, making it more difficult to enforce accountability.
STEALTHbits is well known as a Varonis alternative because it delivers a similar solution. The key difference between it and Varonis is STEALTHbits prioritizes the protection of credentials and sensitive data. A free trial can be requested here.
5. Lepide Auditor
Lepide Auditor is a user-friendly Varonis competitor that audits, reports, and alerts on changes in your key systems and data. The purpose of this software is to streamline your systems management processes, boost security, and help you demonstrate compliance.
This tool offers a range of functionalities. Although its capabilities are not as sophisticated as those of other Varonis competitors, Lepide Auditor compensates by being highly suitable for users with little to no experience, or those who prefer simplicity over sophistication.
Like Varonis, Lepide Auditor delivers auditing functionalities for both on-premises and cloud-based platforms, allowing you to audit changes across Active Directory, file servers, Group Policy, Exchange, SharePoint, Office 365, SQL, Dropbox, Amazon S3, and G Suite. It offers real-time alerts based on threshold conditions or individual events and more than 300 predefined reports. As with Varonis, alerts can be sent to your inbox, syslog server, SIEM, and more, keeping you up to date no matter where you are.
One of the ways that Lepide Auditor really simplifies threat detection compared to Varonis is that while Varonis only has around 100 predefined threat models, Lepide Auditor provides hundreds of predefined threat models. That means you don’t have to spend hours writing complicated scripts, rules, and queries to report on your data security. Deploying one of the predefined models is easy and delivers instant value.
As with Varonis, Lepide Auditor is designed to help you demonstrate compliance with industry standards. It goes beyond Varonis in simplifying the process by featuring pre-packaged reports. These include CCPA, GDPR, SOX, HIPAA, PCI, GLBA, and FISMA, among others.
The Lepide Auditor user interface gives it an advantage over Varonis, because it’s dynamic and easy to use. Data is graphically represented where appropriate, making data interpretation quick and simple, and navigation feels intuitive. Given that Lepide Auditor is largely a tool for people who are interested in a simplified product, this interface is a major asset for the tool.
If you’re considering a Lepide solution, then I recommend scheduling a personalized data risk analysis with one of Lepide’s dedicated engineers. This free service reports on your at-risk data, highlights access control problems, and quantifies risk. By taking advantage of this offer and the 15-day free trial, you’ll be well positioned to determine whether this data security system is right for you.
What Is Varonis?
Varonis is a data security solution created to safeguard your data and systems from breaches and internal threats. The purpose of Varonis is to identify and examine abnormal behavior, such as unauthorized access to Active Directory, email systems, and file servers. The solution also investigates privilege escalations.
When Varonis discovers a risk, vulnerability, or breach—such as global access to confidential data or inconsistent permissions—it will fix them automatically whenever possible. Varonis can also assist with compliance audit preparations, which contributes to its popularity as a data security solution.
With actionable alerts, data ownership determination, intelligent filtering and sorting, and full audit trail functionalities, Varonis remains one of the most widely used data security solutions. However, some Varonis competitors may be even more suited to your needs. Every business will have unique requirements, so it’s important to consider Varonis alternatives, instead of basing your decision solely on the platform’s popularity.
Why Choose a Varonis Alternative?
Although Varonis is in widespread use, and has been for many years, I’ve found what I consider to be some disadvantages in the platform. The web interface, for example, is often described as having limited functionality, and could certainly be improved by providing more in-depth alerts analysis. Though Varonis is taking steps to improve its interface, I still think it lags behind some of the other solutions on the market.
While this may seem like a minor complaint, most IT administrators and professionals will agree with me in saying the user interface is one of the most important components of a tool. This is especially true of tools designed to support and improve data security, because detailed analytics are crucial to this aspect of IT management.
Implementation is another key area where Varonis could be improved. The implementation experience could be a lot smoother and simpler, although Varonis does offer quickstart services to help you jump-start your deployment. The quickstart service includes installation, configuration, and team training. A dedicated project manager will help you customize your deployment, map out risk reduction, and demonstrate value. Although this is a generous service offering, many Varonis alternatives are so easy to implement that additional support is rarely required. If you are interested in an easy implementation process, Varonis may not be the tool for you.
Additionally, Varonis is on the expensive side of the market, and price transparency can be an issue—you have to contact the vendor directly for a quote. In addition, it seems the more you grow, the less cost-effective the platform becomes, with additional features requiring extra licenses. This can substantially increase the implementation cost. Whenever you’re looking to invest in a new product, I recommend thinking about the future of your business and how this solution will be able to grow with you. That’s definitely true if you’re considering investing in Varonis.
Varonis is also a resource-intensive platform, with potentially high data storage requirements if you have a lot of modules and data being collected. Though this is to be expected of such a high-functioning tool, certain Varonis competitors can deliver the same level of advanced functionality in a less resource-intensive way.
Lastly, I think Varonis has a few more minor issues that, while not make-or-break, can add up to make it a less ideal option. These include a lack of customized reporting capabilities, unintuitive third-party system integration, and difficulty navigating built-in Varonis rules and patterns. Every tool will have its pros and cons, but certainly some popular Varonis competitors provide a more intuitive and effective approach to these data security elements.
Best Alternative to Varonis
Although all of the Varonis alternatives listed here have their strengths, I don’t think any of them provide the same combination of user-friendliness and range of functionality as SolarWinds Access Rights Manager. This software delivers a streamlined solution built for growth, being both suitable for a data security beginner and capable of managing enterprise-grade requirements. No matter your background, I think that ARM can fit your needs.
ARM requires zero experience or training to get started. Pricing is transparent, and I’ve found that implementation is significantly easier and faster than the Varonis implementation. Furthermore, the availability of 24/7 phone support with SolarWinds technicians means if you do run into trouble, help is always on hand. To give ARM a try, access the 30-day free trial.
