In the last decade, IT infrastructure has evolved significantly. From small startups to established enterprises, everyone has gradually shifted their systems, data, and applications to the cloud. However, this transition is far from over; the tools and technologies for application delivery via containers, microservices, serverless, and other cloud-native technologies are still going through a refinement phase.
Amidst this change, it’s important for IT teams to continue having complete visibility of every component related to their applications and the underlying infrastructure. This is where real-time log monitoring and analysis come in. In this article, we’ll discuss how you can make the most of your logs to keep your infrastructure and applications shipshape. We’ll briefly define common logging concepts, explain what log monitoring is, explore best practices for log management and analysis, and list the top log monitoring tools currently on the market.
Logging Concepts: A Brief Introduction
What Are Logs?
All applications, networking devices, workstations, and servers create logs—or records of events—which are written to files on local disks by default. These logs contain crucial information. For example, an event log from a web server can contain information like a user’s IP address, date, time, request type, and more. Logs provide administrators with an audit trail to find the root cause of problems and troubleshoot errors. Because there’s a wide range of logs, they often vary in format. To avoid complexity, you should consider using a standard structured format like JavaScript Object Notation (JSON) across your IT environment.
What Is Centralized Logging?
Most applications are now hosted in hybrid environments. This means teams have to keep track of logs from multiple hosts and services. Traditional manual methods of using SSH to connect to servers, search, and analyze individual log files have become impractical as infrastructure complexity has risen. This is where centralized logging provides a way forward.
A centralized logging application involves the following:
- Log collection and transport — Log replication is one of the most common approaches to collecting logs in a central repository. This involves setting up a cron job to replicate your log files on a Linux server to your central server. However, this approach is only useful for batch processing log files. For real-time visibility into logs, you need to transport logs using an API or configure applications to write log events directly to the centralized log management system. Furthermore, you should use a TCP or a RELP to transmit logs instead of a UDP, which often creates packet loss issues.
- Log storage — The centralized storage for logs should be scalable to meet your organization’s growing needs and occasional spikes in log volumes. You need to consider the duration (or log retention period) for which you’ll store different types of logs in this centralized repository. The storage will depend on the types of applications you’re logging; some applications produce highly verbose logs by default, which will take up space. Sometimes, you’ll also need to store logs for months for compliance purposes. In these cases, you can maintain log archives on a cloud service like Amazon S3.
- Log analysis — Log analysis involves parsing logs into different fields, analyzing the data to define baselines, visualizing the data using different graphs, and understanding regular patterns and anomalies. Centralized logging gives you a chance to correlate logs from different infrastructures and application sources to get a holistic view of your environment. Modern tools support machine learning-based analyses, which can help you process a large volume of logs, extract hidden insights, and predict future trends based on historical log data.
- Alerting — You can configure and integrate your centralized logging solution with common tools like Slack, HipChat, and PagerDuty to receive alerts for critical events or when certain thresholds are breached. These alerts help you address critical priority issues.
What Is Log Monitoring?
Log monitoring refers to the set of practices involved in log management and analysis to help IT teams manage their infrastructure and operations. Monitoring can be classified into different categories depending on the scope and methods used. Modern cloud-native applications built using microservices may require distributed tracing to track the flow of a request. However, monitoring logs, events, and metrics are still crucial for all other purposes.
Web Server Monitoring
Whether you’re using Apache, NGINX, Microsoft IIS, or another web server for your business website or application, log monitoring is critical to ensure a better user experience. You can track traffic volume, server errors, failed services, and more with server logs. Monitoring web server logs can help you optimize your web applications, identify surges in traffic, and troubleshoot issues faster.
Network Monitoring
Devices like routers, firewalls, and load balancers form the backbone of enterprise networks. Network error logging and monitoring can help you ensure these devices are functioning properly. It’s also useful for establishing secure communications, auditing, and resolving network errors.
Application Monitoring
A lot of organizations now rely on instrumentation (metrics) and distributed tracing to monitor their applications. While metrics give aggregated information about the health of different services over time, it’s important to note they hold little information and are useful only for detecting issues. To troubleshoot or debug applications, logs are still the best source for connecting the dots across an application stack.
Database Monitoring
Database logs from MongoDB, MySQL, PostgreSQL, etc., can help in proactive monitoring and troubleshooting database errors. You can monitor slow-running queries and take remedial actions. Additionally, you can maintain logs for scheduled tasks, backups, and other routine maintenance jobs for compliance or internal audits.
Cloud Monitoring
Monitoring cloud logs can help you make the most of your cloud-based resources. Most modern log monitoring solutions support AWS log monitoring and can aggregate different logs and metrics from Docker, Heroku, and more. A cloud-based log monitoring solution is often better equipped for the centralized monitoring of your hybrid environment.
7 Best Practices for Log Monitoring and Analysis
- Leverage Logging Levels
- Use Structured Log Formats
- Normalize Your Logs
- Add Tags or Unique Identifiers
- Enable Real-Time Monitoring
- Set Up Alerts
- Integrate Logging With Your CI/CD Pipeline
Once you’ve aggregated all your logs, there are many ways to gather information from them. However, some basic steps and best practices help make log monitoring and analysis simple.
1. Leverage Logging Levels
Some systems create logs continuously, while others produce data only when an unusual event occurs. It’s important for teams to continuously optimize their systems to only collect useful information from logs. Logging levels (warn, fatal, error, etc.) can help you not only filter and extract useful information but avoid information overload. With logging levels, you can monitor some critical events and ignore others.
2. Use Structured Log Formats
Because most log files contain unstructured text data, analyzing them can be painful. Though modern tools can help you analyze all types of structured and unstructured logs, doing so can take time and is often error prone. It’s easier for log analyzers to process or parse logs when they’re formatted in a familiar and standard manner. Therefore, you should consider converting your unstructured data into a structured log format such as JSON. When written in a common format, logs help you get faster results for search queries during troubleshooting.
3. Normalize Your Logs
Because every log contains multiple bits of information, a log parser can make this information more organized and readable, so you can extract actionable insights using search queries. This enables you to monitor specific fields from the event logs. For instance, you can track who’s accessing a server by monitoring the “user” and “source IP” fields. Most log analyzers now support automated parsing for common log formats.
4. Add Tags or Unique Identifiers
Tagging logs is extremely useful when troubleshooting or debugging applications, as it allows you to segment and filter the logs easily. The alphanumeric strings act as unique identifiers, helping you narrow down search results, track specific user sessions, and more. Tags become even more important when you’re analyzing logs in container environments. Applications in Docker Swarm can have multiple containers, which makes tracking all the logs more complex. In situations like this, you can customize your tags and assign different container attributes to make your tags more descriptive.
5. Enable Real-Time Monitoring
Any performance bottlenecks or lingering issues in your live environment can affect application performance, user experience, compliance lapses, and even financial and reputational losses.
That’s why real-time monitoring of production environments is crucial. Teams often rely on real-time log viewers, which usually support live tail features like the tail -f command used in Linux. Live monitoring will help you detect issues as they happen and resolve them before they get out of hand.
6. Set Up Alerts
Because IT teams often share multiple responsibilities, it’s not always possible to monitor everything on a continuous basis. To stay on top of your environment, you should define baselines for your different monitoring parameters and configure alerts for deviations from these baselines. Most modern logging tools provide easy integration with notification services like Slack, HipChat, and PagerDuty. Keep in mind such threshold-based alerts may need frequent reviews to keep signal-to-noise ratios in check.
7. Integrate Logging With Your CI/CD Pipeline
As DevOps goes mainstream, the teams responsible for continually improving their automation pipelines should aim to make the most of logs. They can integrate logging with their source code management systems to keep an audit trail of application performance and availability between different environments. Logging integration can help them track the success rates of their code integrations and facilitate error detection and troubleshooting.
8 Best Log Monitoring Tools
- SolarWinds Papertrail
- LogDNA
- Graylog
- ManageEngine EventLog Analyzer
- LogFusion
- Netwrix Event Log Manager
- XpoLog
- Sumo Logic
1. SolarWinds Papertrail
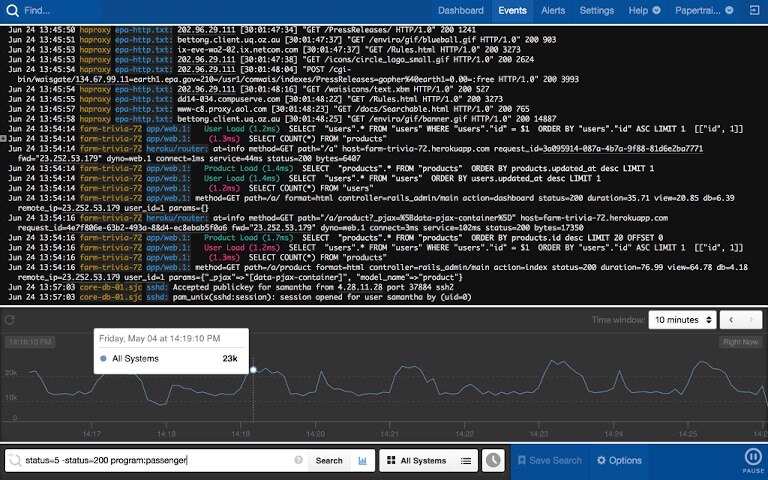
SolarWinds® Papertrail™ is a hosted log management tool designed to help you collect and monitor logs from your servers, applications, databases, networking devices, syslog, cloud, and more. The Papertrail event viewer offers a real-time stream of events where you can pause and resume the feed at any time and scroll to events of interest. You can also skip to a specific time in a couple of clicks. This tool is preferred by teams working in different time zones, as it offers notifications and event summaries in a common time zone. This ensures everyone is on the same page. In the event viewer, you can use the tail command to search through numerous logs in real time. You can also save important searches for faster log analysis. The Papertrail command-line interface makes it highly efficient in searching and account management activities.
While the tool might lack advanced visualization, its fast setup, clean interface, and powerful log tail and search features make it popular among developers. Furthermore, it integrates with SolarWinds AppOptics™, which can help you in the distributed tracing of applications in a complex stack. This integration can enhance your application monitoring with AppOptics, as you can click a trace and drill down to associated logs for troubleshooting. Furthermore, you can integrate Papertrail with common collaboration tools like Slack and PagerDuty to receive real-time alerts. The tool offers several plans suited for different data usage needs.
2. LogDNA
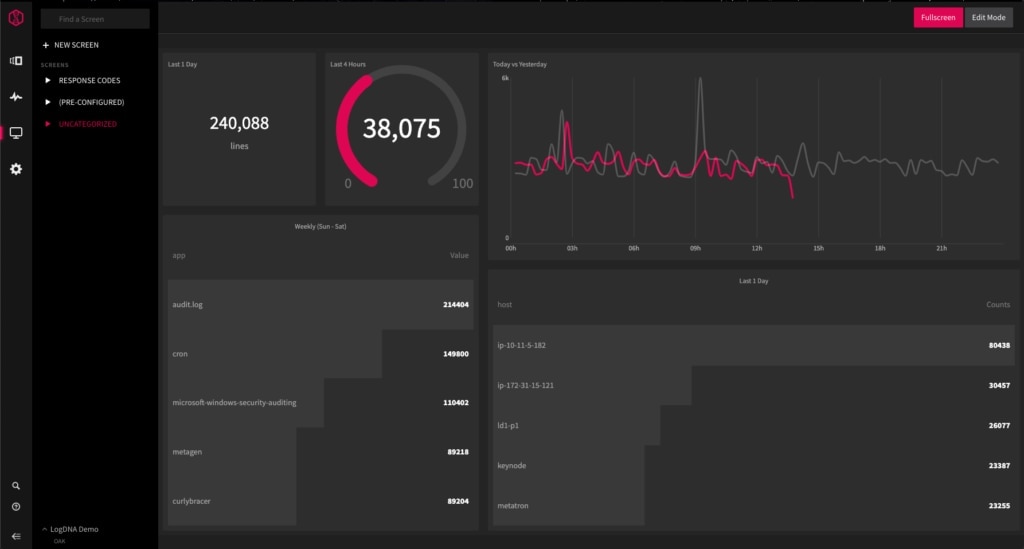
LogDNA is a highly scalable log management and analytics solution designed to help you get quick results for your search queries even when handling massive log volumes. It can auto-parse your incoming logs and offers intelligent alert features. You can use its live tail feature to get real-time situational awareness and mitigate issues quickly. LogDNA allows you to create and save specific “views” based on important search and filters. You can easily switch between views without typing multiple queries and applying filters, which can significantly expedite troubleshooting. Easy configuration, an intuitive user interface, developer-friendly search and filtering features, and advanced visualization are some of the product’s other major highlights. Furthermore, you can deploy it anywhere, as the solution supports hybrid cloud environments. This log monitoring solution also meets HIPAA, PCI DSS, GDPR, and other major compliance and regulatory requirements.
3. Graylog
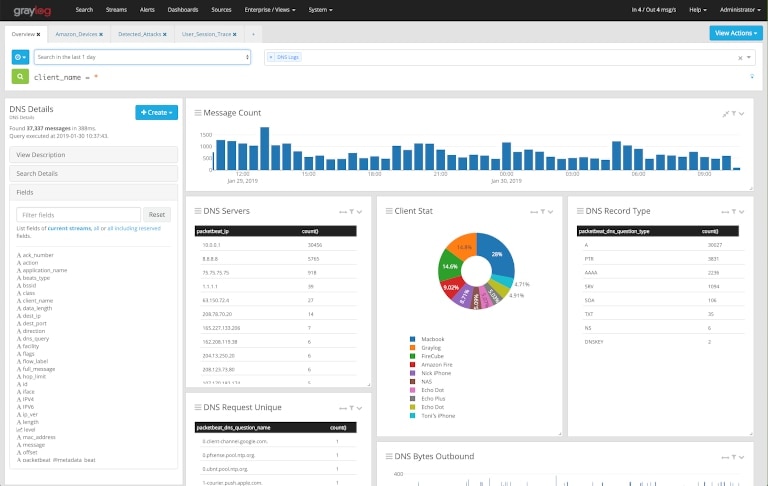
Graylog offers free (open-source) and paid (enterprise) versions of its log monitoring software with advanced log analytics features. This powerful tool makes it possible to monitor large and complex IT environments with logs. It simplifies configuration with the “content packs” you can download from the Graylog marketplace just like any other software package. These content packs help you use community-backed configurations for parsing, alerts, dashboards, and more. With the enterprise version, you can unlock the correlation engine, which can help detect anomalies and send alerts to mitigate security threats. The tool uses Elasticsearch to search and analyze events. The latest version of Graylog offers several advanced visualization features to help you collect and correlate events and metrics from different sources. Additionally, it offers several customizable reports and auto-scheduling support. You can use these reports to meet several internal auditing and reporting requirements.
4. ManageEngine EventLog Analyzer
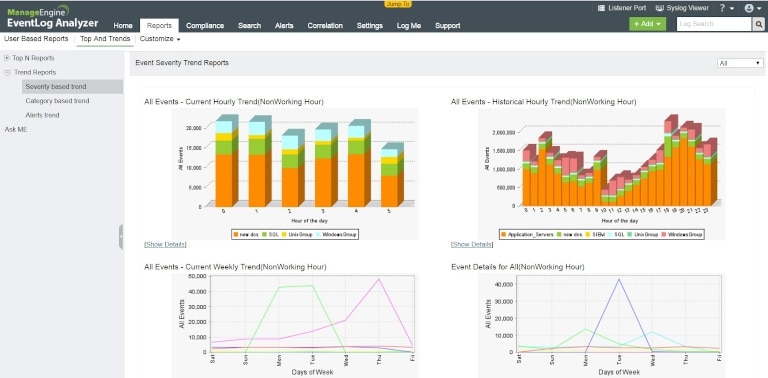
ManageEngine EventLog Analyzer offers comprehensive event log management and monitoring capabilities, covering a wide range of networking devices, file and web servers, databases, and applications. It’s a popular solution supporting end-to-end audits and real-time event correlation in enterprise environments. This solution allows you to keep track of user access permissions and activities within a network, and its built-in file integrity monitoring feature allows you to stay on top of your critical registry files and folders. You can also use several out-of-the-box templates for compliance reporting. ManageEngine offers a lifetime free edition of Event Log Analyzer supporting five log sources, which can help small organizations meet log monitoring requirements. While the tool is highly intuitive and offers dedicated support, a wide range of security information and event management (SIEM) capabilities might be redundant if you’re looking for a simple log monitoring tool.
5. LogFusion
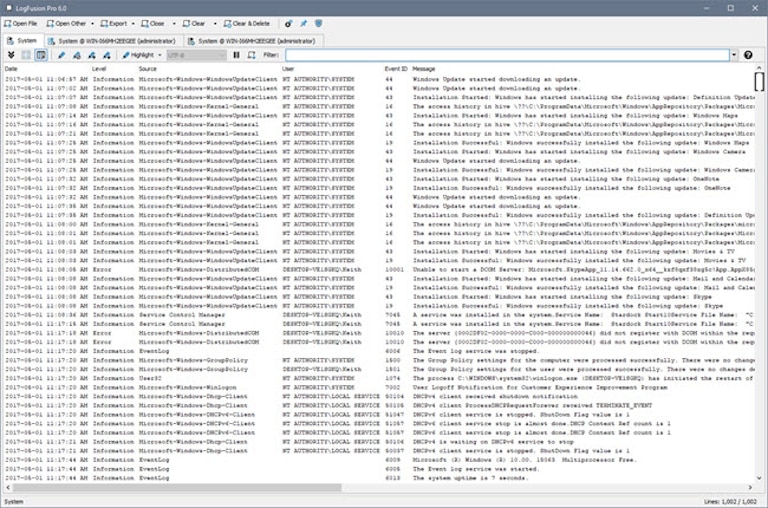
LogFusion is another real-time log monitoring tool popular among IT and software development teams. It allows you to tail logs for a view of your live environment. This tool can read text log files from a wide range of supported log formats, covering all common server and application debug logs. It also allows local and remote event log monitoring from Windows. The tool has a simple interface with easy navigation, streamlining troubleshooting. You can filter and highlight events of interest to get to the root cause of issues. In addition to simple search operators, you can use complex queries to drill down and search through numerous logs.
6. Netwrix Event Log Manager
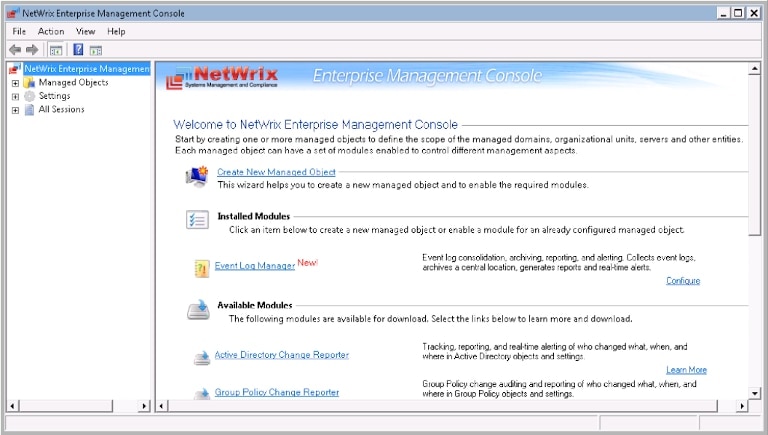
If you need a tool to monitor Windows event logs in an enterprise network, the native event viewer might not be able to serve your purpose because it shows logs on the computer where it’s installed. This is where Netwrix Event Log Manager can help. It’s a free tool for monitoring Windows server logs in enterprise networks. With this tool, you can capture and view various security logs, application logs, and application services logs from workstations across your network. The tool also offers real-time alerts for important events. You can set up the severity of alerts based on your requirements.
7. XpoLog
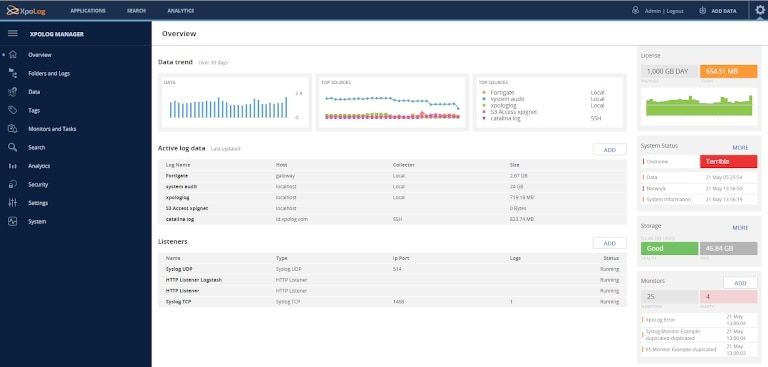
XpoLog is an advanced log monitoring tool designed to collect log data in your distributed IT environment from a wide range of servers, applications, and services. Its automated log parsing and tagging, its smart indexing, and its faster search can help you quickly pinpoint issues and bottlenecks. The tool can also automatically process data to offer real-time security- and performance-related insights. It makes analyzing complex and high-volume log data easier with its advanced machine learning algorithms. Its log viewer offers a highly intuitive tree-type navigation structure to analyze the trail of events across multiple systems and applications. You can also use several out-of-the-box monitoring templates for cross-system visibility. Some of XpoLog’s major highlights include its advanced visualization, faster correlation, and high degree of automation. It offers multiple plans according to your data usage, and you can get a dedicated account manager with its premium version. You can also get a free trial to evaluate its features and capabilities.
8. Sumo Logic
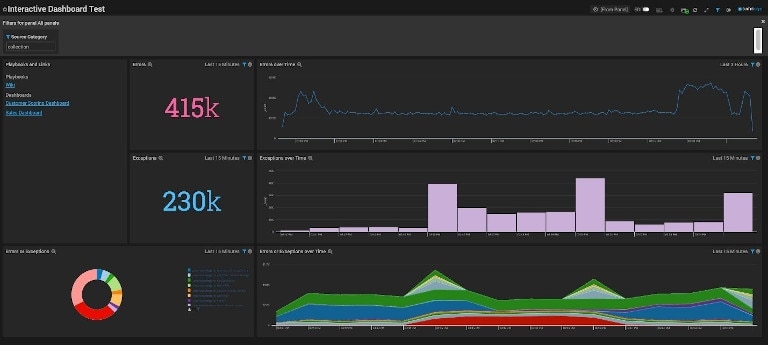
Sumo Logic is a cloud-based solution offering a comprehensive set of log monitoring and analytics features. It’s built for organizations with a significant footprint in the cloud. The solution can facilitate application and infrastructure monitoring in multi-cloud setups, and it offers numerous integrations, enabling quick decision-making and proactive resolution of issues in CI/CD pipelines. The solution leverages LogReduce pattern analysis to analyze and correlate events and data spread across numerous logs in real time. Sumo Logic also offers several preconfigured dashboards and visual reports for business intelligence. However, if you’re looking for a simple log analyzer for a small team, you might find this solution a bit overwhelming. It takes a while to set up and to get used to its features and workflows.
How to Select a Log Monitoring Tool
From the above coverage of tools, you can see there are several available options for log management and monitoring. All these tools offer basic sets of features, including centralized log management, log tail and search features for real-time monitoring, and integration with notification services. However, some of them also offer comprehensive SIEM and application performance monitoring features, including support for distributed tracing and metrics. Therefore, you have to prioritize and understand your organization’s baseline monitoring needs to short-list possible solutions.
Performing proof of concept (PoC) will give you a better understanding of a tool’s capabilities and shortfalls. The trial runs will give you an idea of the tool’s ease of configuration, speed, and suitability for your IT environment. Many of the free, open-source solutions lack dedicated support. This can be an issue, as installation, integration, and upgrades are often error prone. Unless your team is confident in dealing with these operational challenges and has enough time to seek community support, you should use a commercial tool like Papertrail. Papertrail is the best solution because its coverage of smart features effectively serves crucial log management needs. As we discussed, this tool is simple to set up and offers powerful search and real-time live tail features with a clean interface and no configuration hassles. It’s also a good choice because it offers better integration and scalability for your future needs. Getting started with Papertrail is simple; you can customize your plan or get a free version here.


