Businesses, organizations, and individuals rely on networks to communicate and exchange data. The rapid growth of technology and increasing reliance on networked systems have made robust network performance and security critical. However, maintaining optimal network performance and security is a difficult task. Network failures, security breaches, and performance bottlenecks can result in substantial financial losses and reputational damage.
What Is Network Device Monitoring?
How Network Device Monitoring Works
Key Metrics Monitored in a Network Device
Importance of Network Device Monitoring
What Types of Network Devices Can Be Monitored?
5 Top Network Monitoring Tools
1. SolarWinds Observability Self-Hosted (Free Trial)
Most Important Capabilities of Device Monitoring Solutions
Choosing the Right Network Monitoring Tool for Your Company
Network Device Monitoring Best Practices
Here’s where network device monitoring comes into play. Organizations that implement robust network device monitoring tools and software can proactively identify and address possible issues, helping ensureg uninterrupted network operations and protecting sensitive data.
In this post, we’ll look at network device monitoring, what it is, and five network device monitoring tools we recommend.
What Is Network Device Monitoring?
Network device monitoring is the continuous tracking and analysis of network components such as routers, switches, firewalls, and servers to maintain their peak performance and security. Specialized software and tools are used to collect and assess data on device health, resource utilization, and general network behavior.
The primary objectives of network device monitoring include:
- Proactive issue detection—By closely monitoring network devices, IT staff can spot abnormalities or performance degradation before they become severe problems.
- Performance optimization—Network device monitoring identifies bottlenecks and inefficiencies, allowing network resources to be fine-tuned and optimized.
- Security threat detection—By examining network traffic and device behavior, potential security breaches can be recognized and handled quickly.
- Maintaining network uptime and availability—Continuous monitoring helps ensurs that network devices are performing properly, reducing downtime and increasing network reliability.
How Network Device Monitoring Works
Network device monitoring involves a systematic approach to gathering, analyzing, and responding to network data.
- Data collection: This is the first phase in which information is collected from network devices. This includes gathering information about device status, performance metrics, and network traffic patterns using methods such as Simple Network Management Protocol (SNMP), Syslog, NetFlow, or sFlow; API calls; or flow data analysis.
- Data analysis and visualization: This is the next step, in which acquired data is processed and interpreted to generate useful insights. Metrics such as device uptime, network latency, bandwidth utilization, and security events are evaluated and frequently visualized using graphs and charts. This step facilitates the discovery of trends, abnormalities, and potential problems.
- Alerts and notifications: One important aspect of network device monitoring is the ability to set thresholds and triggers for various performance metrics and security indications. When certain criteria are exceeded, the system issues alerts and messages. These warnings can be delivered via email, SMS, or integrated communication channels, allowing administrators to respond quickly to possible issues and eliminate potential risks before they affect the network.
By following these steps, network device monitoring provides a comprehensive view of the network’s health and performance, helping ensure that problems are identified early and remedied promptly.
Key Metrics Monitored in a Network Device
Network device monitoring involves tracking various metrics to assess device health, performance, and overall network efficiency. Key metrics include:
- Device health—Device health includes CPU utilization, memory consumption, disk space, temperature, and fan speed. Monitoring these metrics allows you to spot potential hardware issues or performance bottlenecks.
- Network performance—Network performance metrics like latency, jitter, packet loss, and bandwidth usage provide information about network responsiveness and capacity. Tracking these metrics allows network administrators to discover congestion spots and optimize network performance.
- Network traffic—Analyzing network traffic patterns can assist in uncovering potential security concerns, performance bottlenecks, and application behavior. Network optimization relies heavily on metrics such as traffic volume, protocol distribution, and error rates.
- Device availability—Monitoring device uptime and downtime is important to network reliability. Tracking device availability allows you to estimate the effect of failures and plan for repair.
- Security events—Network devices frequently produce security-related events, such as failed login attempts, intrusion detection alarms, and malware detections. Monitoring these occurrences allows you to identify and respond to potential security threats.
Importance of Network Device Monitoring
Network device monitoring is essential for keeping an organization’s network healthy, performant, and secure. Here are some of the main reasons why network device monitoring is important:
Enhanced Network Performance
Network device monitoring provides valuable insight into network performance, allowing IT professionals to identify bottlenecks, optimize resource consumption, and increase overall network efficiency. This insight equates to faster application response times, a better user experience, and more productivity.
Improved Security Posture
Monitoring network devices prevents cyber threats. Organizations can discover abnormalities that indicate malicious activity, such as unauthorized access, data breaches, or DDoS attacks, by regularly monitoring network traffic patterns and device behavior. This proactive strategy protects sensitive information and helps ensure system integrity.
Cost Reduction
Effective network device monitoring improves resource allocation and avoids wasteful hardware purchases. Organizations can minimize operational costs and increase the return on investment in their IT infrastructure by identifying unused devices and improving network settings.
Data-Driven Decision-Making
The information gathered by network device monitoring can be used to make sound decisions about network growth, upgrades, and capacity planning. Organizations can assist business growth by studying performance patterns and identifying areas for improvement in their IT infrastructure.
Network device monitoring is more than a technical job; it’s a strategic requirement that helps ensure company continuity, efficiency, and security.
What Types of Network Devices Can Be Monitored?
Monitoring network devices involves closely observing the functionality and condition of different network components. The types of devices that can be monitored include:
Routers
They facilitate data transfer between various networks and guarantee that information reaches its intended location. Routers come in various types, such as:
- Core routers: A network’s central component that manages heavy traffic volumes.
- Edge routers: Connect a network to other external networks or the internet.
- Distributed routers: Distribute traffic within a network.
Tracking traffic flow, routing errors, and possible bottlenecks are made easier by monitoring routers.
Switches
Devices in a network are connected by switches, which provide effective communication. To identify port problems, clear network congestion, and keep the best possible connectivity, you need to monitor switches. The various types of switches include:
- Ethernet switches: These are the most common type, and they are used to connect devices within a network.
- Wireless switches: Used to connect wireless devices to a wired network.
- Fiber switches: Handle high-speed data transmission over fiber optic cables.
Firewalls
Firewalls monitor incoming and outgoing traffic based on security rules. We have software firewalls (integrated into operating systems or network devices) and hardware firewalls (specialized devices that protect a network against unauthorized access). Firewall monitoring is important for detecting potential breaches, malicious traffic, and firewall issues.
Load Balancers
Network traffic is distributed among several servers using load balancers. Hardware load balancers are used to boost performance by dividing traffic among several servers, while software load balancers. By monitoring these devices, you can minimize server overload, ensure balanced traffic, and improve network reliability.
Servers
Applications, files, and services are hosted on servers. Monitoring server performance includes tracking CPU, memory, disk usage, and network traffic to ensure smooth operations. The two types of servers are:
- Physical servers: Traditional hardware servers.
- Virtual servers: Software-based servers that can be created and managed on a single physical machine.
5 Top Network Monitoring Tools
Here are five top network device monitoring tools we strongly recommend, each offering unique features and capabilities to help you maintain a robust and secure network.
1. SolarWinds Observability Self-Hosted (Free Trial)
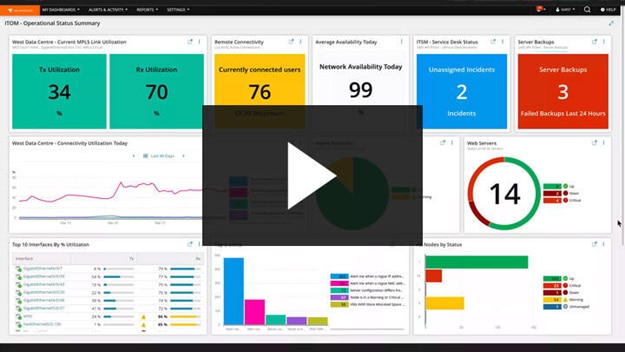
© 2024 SolarWinds Worldwide, LLC. All rights reserved.
SolarWinds® Observability Self-Hosted is a monitoring and management tool that offers a unified view of complicated IT infrastructures. It merges on-premises, cloud, and hybrid infrastructure into a unified platform that provides real-time data on performance, availability, and overall system health. This technology is especially useful for enterprises functioning in changing IT landscapes, as it allows them to anticipate and address possible difficulties in advance.
SolarWinds Observability takes a comprehensive approach to monitoring by gathering and analyzing data from a variety of IT components, including networks, servers, apps, and databases. Its main features include end-to-end visibility, real-time insights, anomaly detection, alerting, dashboards, and configuration management.
Pros
- Unified platform: Streamlines monitoring across diverse environments.
- Improved performance: Helps optimize resource utilization and system efficiency.
- Faster troubleshooting: Quickly identifies and resolves issues.
- Reduced downtime: Proactive identification of potential problems.
- Enhanced collaboration: Facilitates teamwork and knowledge-sharing.
Cons
- Complex setup: While designed to be simple to get started with, the initial setup and configuration can be complex for some users.
- Learning curve: The comprehensive and integrated features may present a steeper learning curve for new users.
Learn more Download Free Trial
2. PRTG Network Monitor
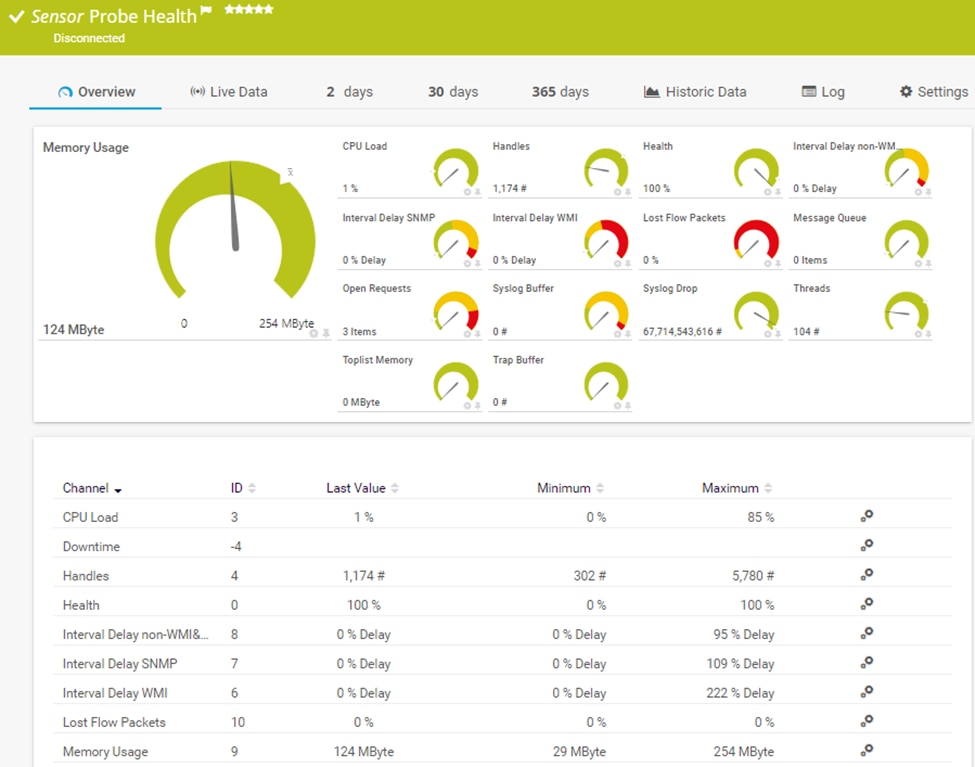
© 2024 Paessler GmbH. All rights reserved.
PRTG® Network Monitor is a network monitoring solution suitable for businesses of all sizes. It delivers real-time information about network performance, availability, and resource utilization. With the ability to monitor a wide range of devices and applications, PRTG provides a centralized view of the IT infrastructure.
PRTG collects data from network devices via various protocols (SNMP, WMI, packet sniffing, etc.) and displays it in a user-friendly interface. The key features are multi-vendor support, real-time monitoring, performance measurements, alerting, reporting, and remote management.Pros
- Comprehensive monitoring: Covers a wide range of network components and applications.
- User-friendly interface: Easy to set up and use.
- Scalability: Handles networks of various sizes.
- Cost-effective: Offers different pricing options to suit different needs.
- Strong community support: Active user community and extensive documentation.
Cons
- Agent requirement: While agentless monitoring is supported, some features might require agents.
- Resource consumption: Monitoring a large network can impact server performance.
- Feature overload: The abundance of features might be overwhelming for some users.
- .
3. OpManager
OpManager® is a network monitoring tool that delivers real-time information about the health and performance of network devices and infrastructure. It provides a wide range of capabilities to assist IT professionals in proactively managing network issues and optimizing performance.
OpManager monitors a variety of network components, such as routers, switches, firewalls, servers, and virtual machines. It collects and analyzes performance data to get insights into network behavior and identify potential problems. Multi-vendor support is often one of the key characteristics. Monitoring, performance analysis, fault management, capacity planning, and reporting are done in real-time.
Pros
- Comprehensive monitoring: Covers a wide range of network devices and components.
- User-friendly interface: Offers an intuitive dashboard for easy navigation.
- Cost-effective: Provides a good balance of features and pricing.
- Strong support: Offers technical support and resources.
- Scalability: Can handle networks of various sizes.
- ConsComplexity: Advanced features may require additional training.
- Potential for alert fatigue: Excessive alerts can be overwhelming.
- Dependency on agents: Some monitoring features might require agent installation.
4. Datadog
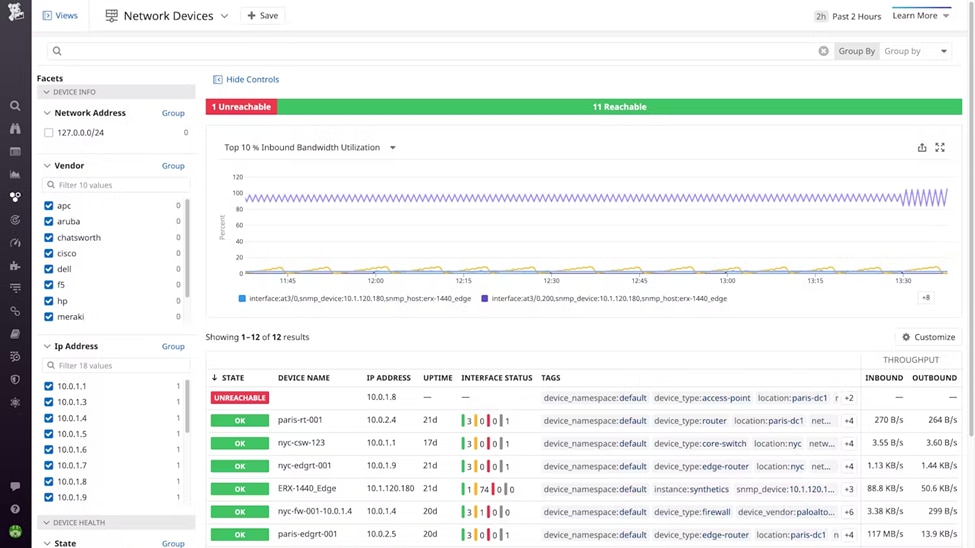
© 2024 Datadog, Inc.. All rights reserved.
Datadog® is a cloud-based observability tool that offers full monitoring and analytics for complicated IT settings. It provides an in-depth overview of application, infrastructure, and network performance, allowing teams to swiftly detect and rectify issues. Datadog is ideal for enterprises with modern, cloud-native infrastructures.
Datadog collects and analyzes information from a variety of sources, including applications, infrastructure, and networks. It offers real-time monitoring, performance data, and visualizations to assist teams in understanding system behavior and spot abnormalities. Key capabilities include application performance monitoring (APM), infrastructure monitoring, network monitoring, log management, real user monitoring (RUM), synthetic monitoring, distributed tracing, anomaly detection, alerting, incident management, and customized dashboards.
Pros
- Comprehensive platform: Offers a unified view of applications, infrastructure, and networks.
- Cloud-native focus: Well-suited for modern, cloud-based architectures.
- Rich feature set: Provides a wide range of monitoring and analytics capabilities.
- Scalability: Handles large-scale and complex environments.
- Strong community and support: Active user community and extensive documentation.
Cons
- Cost: Datadog can be expensive for large-scale deployments.
- Steep learning curve: Mastering all features may require time and effort.
- Vendor lock-in: Reliance on Datadog for monitoring can create challenges for migration.
Overall, Datadog can provide a comprehensive view of complex IT environments, which makes it a popular choice for many organizations.
5. LogicMonitor
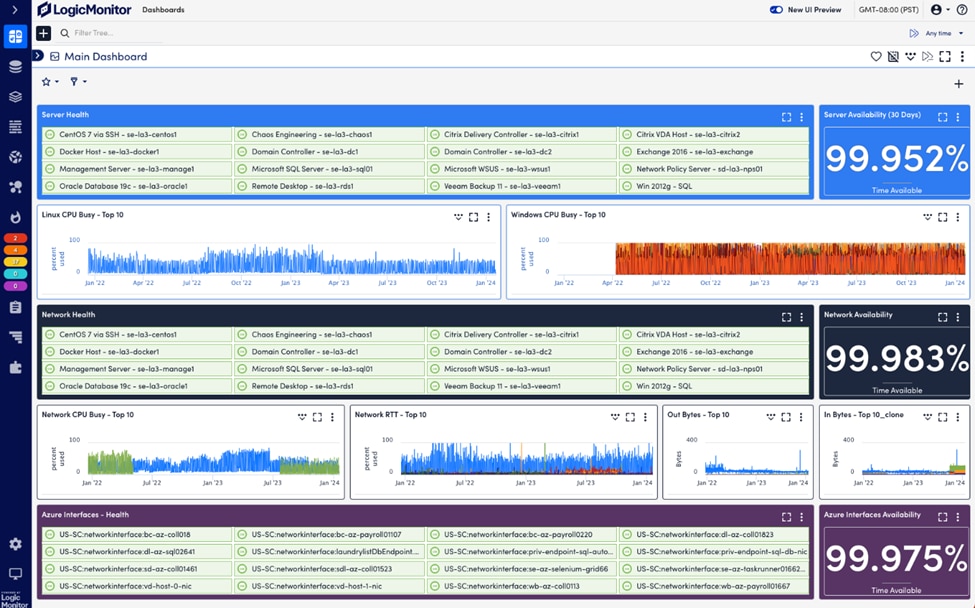
© 2024 LogicMonitor Inc. All rights reserved.
LogicMonitor® is a cloud-based observability platform that enables the complete monitoring and administration of IT infrastructure, applications, and services. It provides enterprises with real-time insights into system performance, availability, and health, allowing them to fix issues and enhance operations.
LogicMonitor collects and analyzes data from a variety of IT components, including servers, networks, applications, and cloud environments. Its primary features include infrastructure monitoring, APM, network monitoring, cloud monitoring, container monitoring, alerting and notification, dashboards and visualizations, automation, and remediation.
Pros
- Cloud-based platform: Offers scalability and accessibility.
- Comprehensive monitoring: Covers a wide range of IT components.
- Real-time insights: Provides up-to-date information on system performance.
- Automation capabilities: Reduces manual intervention and improves efficiency.
- Strong focus on AI and machine learning: Enables predictive analytics and anomaly detection.
Cons
- Potential for complexity: Managing a large-scale monitoring platform can be complex.
- Cost: Pricing might be higher compared to some other options.
- Vendor lock-in: Relying heavily on LogicMonitor could limit flexibility.
Most Important Capabilities of Device Monitoring Solutions
Effective device monitoring tools provide several essential capabilities to provide the best possible network security and performance. The following are some of the important features:
Scanning for Device Discovery
- Automatic discovery: Identifies network devices automatically, including ones that have recently been added or removed.
- Port scanning: Network ports are scanned to find out which services are active on each device.
- VLAN discovery: This process involves finding virtual local area networks (VLANs) and the devices connected to them.
Device Locator
- Inventory management: Maintains a comprehensive inventory of all network devices, including their location, model, and configuration.
- Device profiling: Compiles full data on every device, including hardware specifications, firmware version, and operating system.
- Dependency mapping: This shows how devices are related to one another and their dependencies.
Troubleshooting
- Real-time monitoring: Constantly monitor the health and performance of the device to spot any problems.
- Alerting: Sends out notifications when anomalies or possible issues are found.
- Root cause analysis: Helps in identifying the underlying causes behind network issues.
Device Configuration
- Configuration management: Stores and manages device configurations.
- Configuration compliance: Ensures that devices follow predefined configuration standards.
- Configuration changes: keeps track of and audits configuration changes to ensure stability and security.
Choosing the Right Network Monitoring Tool for Your Company
Selecting the appropriate network device monitoring tool is crucial for effective network management. Several factors should be considered when making this decision:
Identify Your Monitoring Needs
Understanding your monitoring needs is very important. Consider the size and complexity of your network, the types of devices you must monitor, and the key performance indicators (KPIs) you wish to track. This process will help you limit your alternatives and focus on products that are appropriate for your organization’s needs.
Scalability and Flexibility
Choose a tool that can grow with your network. A scalable solution eliminates the need for regular tool changes as your network grows. Flexibility is also significant since it allows you to customize the tool to meet changing monitoring needs.
Cost
Consider the overall cost of ownership, which includes initial setup, license, and continuing maintenance payments. Compare the tool’s features and capabilities to the needs and budget of your organization to determine whether it provides good value for your money.
Ease of Use and User Interface
The application should be easy to use with an intuitive UI. Consider your team’s technical knowledge and choose a tool that provides acceptable levels of complexity. A well-designed interface allows for more efficient monitoring and troubleshooting.
Integration with Existing Systems
Consider how the monitoring solution will work with your existing IT infrastructure. Compatibility with other systems, such as ticketing or security tools, can help to streamline workflows and increase overall efficiency.
Network Device Monitoring Best Practices
Implementing effective network device monitoring requires adherence to certain best practices to maximize its benefits. Here are some key guidelines:
- Perform regular device discovery: Continuously scan the network for new connections and make sure no forgotten or illegal devices are joined. Frequent device discovery enhances visibility and lowers security threats by keeping the network inventory current.
- Establish clear monitoring objectives: Establish your goals for network device monitoring, such as reducing downtime, boosting security, or increasing performance. Establishing clear goals helps prioritize actions when problems occur and directs the setting of the monitoring tools.
- Automate routine tasks: Reduce the workload associated with manual management and monitoring by utilizing automation. To ensure consistent performance across all network devices, common procedures like firmware updates, threshold adjustments, and device configuration can be automated to save time and reduce human error.
- Ensure compliance and security monitoring: Monitoring network devices involves more than simply performance—security is also important. To identify unusual activity, unauthorized access, or potential vulnerabilities, make sure that monitoring tools are connected to security systems. Automated compliance checks are necessary to guarantee that devices follow security guidelines.
- Review and update monitoring tools regularly: The technologies used for monitoring should also change as network infrastructures do. Ensure that your monitoring system is still compatible with new devices, protocols, and technologies by giving it a regular review.
Conclusion
In conclusion, network device monitoring is critical to ensuring optimal network performance and security. Organizations may proactively discover and address issues, optimize performance, and protect against threats by measuring and analyzing network components in real-time.
By carefully assessing your requirements, reviewing available possibilities, and picking a solution that corresponds with your organization’s goals, you may greatly improve the resilience and efficiency of your network.
Remember that a well-managed network is a healthy network. Invest in network device monitoring to safeguard your company and drive success.
This post was written by Vincent Chosen. Vincent is a web developer and technical writer. He has proficient knowledge in JavaScript, ReactJS, NextJS, React Native, Nodejs, and Database. Aside from coding, Vincent loves playing chess and discussing tech-related topics with other developers.


