As organizations invest more heavily in their digital infrastructure, the consequences of data breaches and cybersecurity attacks have also increased. Research from the Ponemon Institute indicates that the average cost of a data breach in 2018 rose by 6.4% compared with the previous year to a total of $3.86 million. Related to that, the average cost of each stolen file also increased to $148.

Given the rising stakes and increasing costs of data breaches, organizations across a range of industries need to ensure that they understand what they’re up against. This is particularly important given that cybercriminals—whether outside of organizations or within them—are exploiting the same vulnerabilities that are the result of the same mistakes made from one industry to the next. In fact, the 2018 Verizon Data Breach Investigations Report found that 94% of security incidents and 90% of data breaches have fallen into the same nine categories since 2014.
For IT teams and CISOs, this means that it’s time to learn how to prevent a data breach and invest in tools to close the cybersecurity gaps that make such incidents possible. While this will mean different things for different organizations and enterprises, what’s important is identifying what risks you currently face, situating those risks in the context of cybersecurity breaches across your industry and others, and implementing solutions that can help protect your sensitive data and digital infrastructure.
It’s important to ask clear questions to help you mount a proper defense. For example, what are the types of data breaches? What are the reasons for data breaches? What products on the market can help your team avoid data breaches? By beginning to answer these questions and working to evaluate industry responses, you can move your organization closer to a data security strategy that fits your needs.
What is a Data Security Breach?
The exact nature of data breaches will vary depending on industry, organization size, and network architecture. However, at the most basic level, a data breach is defined as the unauthorized access of otherwise private digital information. What cybercriminals do with that data varies depending on their intent, but what’s key is the illicit nature of their access to personal information that doesn’t belong to them. Data security breaches can also include the exfiltration of information bad actors have access to but shouldn’t or data they have access to without explicit approval to disseminate.
If you’re asking what is a data breach, it’s worth noting they follow a set pattern, although there are different types of data breaches we’ll discuss further. By evaluating the most common steps bad actors may take on their way to pulling off a successful data breach, cybersecurity teams can better analyze their own vulnerabilities and prepare defenses to make it too difficult for most cybercriminals to successfully penetrate.
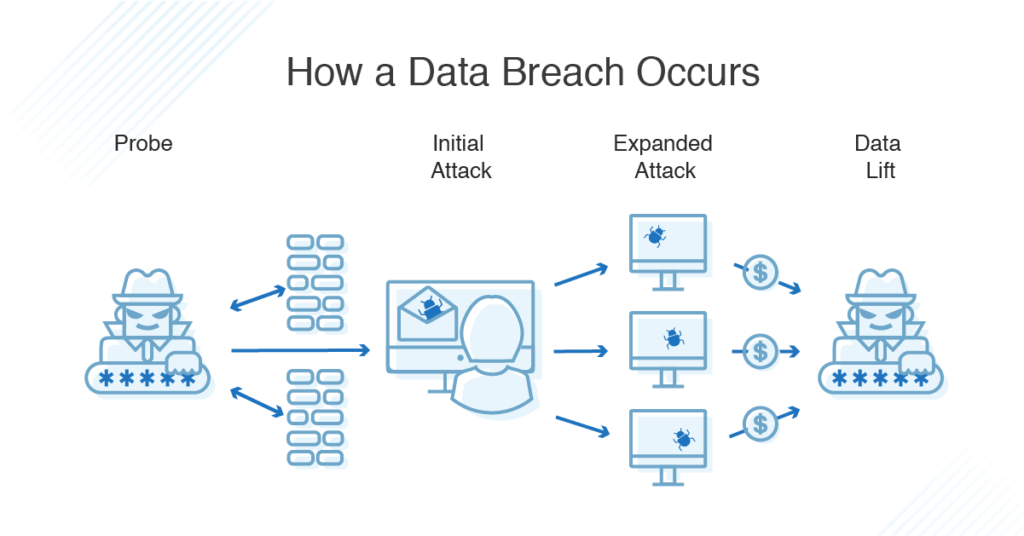
- Probe: Malicious parties begin by attempting to learn more about your network and broader digital environment. They may probe your cybersecurity defenses, test passwords, evaluate how to launch an eventual phishing attack, or look for out-of-date software without the latest security patches.
- Initial Attack: Once they have a handle on how best to carry out their attack, they’ll launch a first wave, perhaps by sending an email that attempts to trick employees into clicking on a link to a malicious website or by corrupting an application essential to employee workflows.
- Expanded Attack: Once a vulnerability has been exploited in this way, cybercriminals will evaluate their next steps. Typically, this will involve them leveraging whatever toehold they have to attack the rest of the network and locate as much valuable personal information as possible.
- Data Lift: Because different types of cybersecurity breaches occur on different timescales, bad actors may attempt to exfiltrate as much data as quickly as possible or lay dormant until they understand just how much they can get away with.
The exact kind of information stolen from an external cybercriminal or an internal bad actor will vary from one organization to the next. However, the Verizon study found 76% of breaches were financially motivated. This may involve trade secrets, proprietary financial information, and sensitive government records, or it may center on the theft of customers’ personal data—as it has with publicized breaches with Facebook, Yahoo, and Uber—cybercriminals could then use for their own gain. And it’s crucial to know how to prevent security breaches in healthcare for entities governed by HIPAA, as patients could have their health data put at risk.
What Are the Main Types of Data Security Breaches?
As explained above, there are a lot of caveats when it comes to discussing how to avoid data breaches. The exact nature of an assault will depend on an organization’s specific vulnerabilities and what a given cybercriminal intends to do with the information they steal.
With that said, there are several main types of data breaches. These include basic human error, cyberattacks ranging from phishing and malware to ransomware and password attacks, and assaults deliberately carried out by insiders.
- Human Error: Data security breaches caused by human error are, as the category implies, accidental. For example, IT teams may inadvertently expose customer personal information (like credit card numbers, login credentials, and email addresses) by misconfiguring servers, or employees may fall prey to social engineering attacks. These types of attacks attempt to trick an organization’s team members into clicking on malicious links or downloading seemingly safe files. According to CompTIA, more than half of data breaches are the result of human error, making this category one of the most important to resolve.
- Device Loss: Additionally, the loss of devices due to personal forgetfulness or outright theft can pose a major security risk. Individuals may be careless and leave smartphones, laptops, tablets, or thumb drives behind—devices with proprietary information or unfettered access to your network. They may also not pay proper attention to those devices and give bad actors a chance to steal them when they’re not being looked after. In either situation, criminals may be able to bypass a given device’s security protocols and gain access to sensitive information.
- Cyberattack: The next category, cyberattack, is understandably at the forefront of the data security conversation. With the cost of cybercrime surpassing $600 billion around the world, organizations are concerned about the threats posed by bad actors attempting to game their defenses. To do so, cybercriminals may deploy malware to infect systems, phishing to gain access through network users, or ransomware to extort companies after stealing valuable information. While the underlying vulnerabilities exploited during these attacks differ—malware may depend on applications that haven’t been updated properly, while phishing relies on human error—the concerted, nefarious intent of the attacks remain the same.
- Internal Breaches: Finally, internal data security breaches that aren’t accidental are a real threat. Disgruntled employees, employees who suspect they’re about to be terminated, or dismissed employees whose credentials have, inadvertently, yet to be revoked, may exfiltrate information they have access to without permission to disseminate. While there can be any number of reasons they may decide to attempt an attack like this, from extortion to black market trading, organizations should remember breaches coming from the inside often aren’t caused by human error alone.
Best Practices: How to Prevent a Data Security Breach
For IT teams, defending organizations from such a diverse array of threats is daunting. You need to know to prevent a data breach and what steps are essential building blocks of any larger cybersecurity defense. Traditionally, the data breach lifecycle includes five key stages: discover, detect, prioritize, remediate, and manage. These stages aren’t one-and-done steps, however. Rather, they should be ongoing components of an around-the-clock data breach prevention operation.
- Discovery: During the discovery phase, security professionals should work through sensitive information to identify any unprotected data at rest. This kind of information is an easy target for bad actors both within and outside your organization, so it’s vital to take steps to secure it. You can start this process by reviewing what insiders have access to what data and changing authorizations to ensure only those who need to work with that data can.
- Detection: Next comes detection. At this stage, IT professionals should be monitoring for security threats that can provide cybercriminals with easy entry points into your network. Without this kind of vigilance, it can be surprisingly easy for bad actors to access and exfiltrate your data. For instance, if major applications haven’t been updated with the latest security patches, bad actors can easily exploit those vulnerabilities to access your network. Regularly reviewing pending updates is, in this way, essential.
- Prioritization: During the prioritization phase, it’s important to triage at-risk assets to secure the most glaring cybersecurity openings. By leveraging the combined intelligence of security information and data operations to pinpoint where bad actors might attack your network, your team can close gaps and better protect your organization. To accomplish this, security professionals will need to conduct audits to understand what needs to be prioritized.
- Remediation: With remediation, you’ll work to resolve the threats to data security that you’ve identified and prioritized during the previous steps. As explained earlier, this could involve updating applications with the latest security patches. It could also require you to encrypt sensitive information to control access to it, remove it from your network entirely, or revise authorizations and user permissions across your organization.
- Management: Finally, IT professionals need to manage this process strategically and effectively. Taking control of the data breach prevention lifecycle and making it work for your organization will require scalable solutions leveraging useful data from across your network and turning it into actionable insights. As stated above, this process is an ongoing one, rather than a project with a finite endpoint. It’s worth investing in tools to make it easier for cybersecurity teams to monitor your digital infrastructure and resolve potential threats.
What Are the Best Tools for Preventing a Data Breach?
Preventing a data breach of sensitive information is an essential task for IT teams and cybersecurity professionals, albeit a challenging one. Given the rise of advanced cybercrime around the world and the proliferation of new technologies and digital behaviors such as IoT and BYOD, respectively, securing sensitive information across sprawling companies calls for sophisticated solutions with next-generation capabilities to help support your organizational cybersecurity strategy.
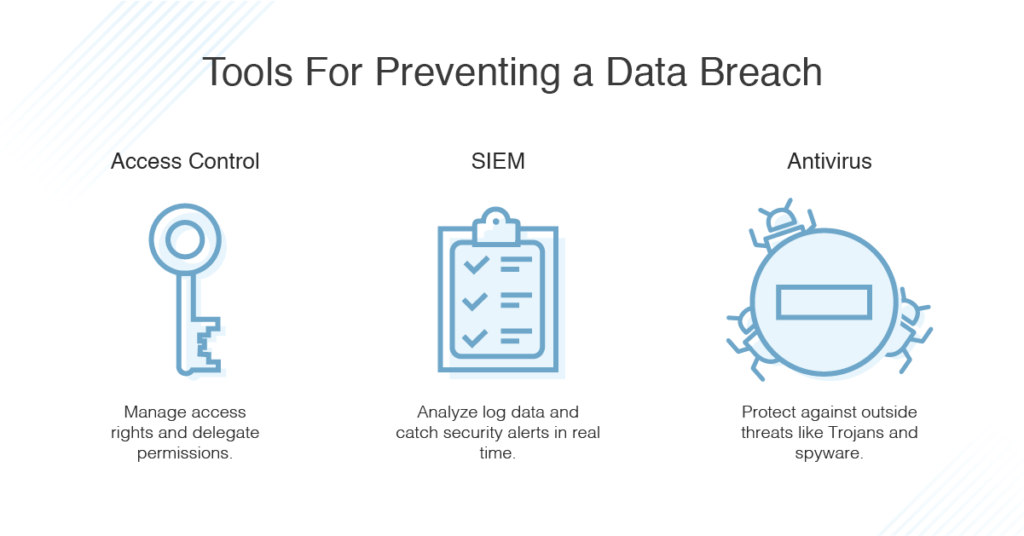
The following are some common types of security software designed to help you protect your business from breaches of sensitive data:
- Access control: It’s important to have a tool to manage access rights and help delegate proper permissions to employees. Access control software provides basic and essential security for businesses, as it lets IT monitor who has access to given information and more easily amend permissions as needed. A configurable, role-based template helps ensure IT teams can automatically assign what your company deems is the proper amount of permission levels based on job role. In some cases, this kind of software can help you audit trails and generate compliance reports.
While having effective access control is a good step towards preventing security issues related to user accounts, having a solution to monitor for data exposed in breaches can also help you stay aware of potentially compromised credentials. Using a purpose-built tool combining automation with human intelligence to monitor find and flag breach data from public and non-public sources can lower your risk of and help prevent account takeovers. - SIEM: Security information and event management (SIEM) software combines security information management (SIM) and security event management (SEM) for a more comprehensive solution. The primary focus of a SIEM tool is log management, which entails collecting and storing log messages, and analyzing and reporting on log data. The software also oversees security alerts in real time, and in some cases can resolve typical threats automatically. IT can also use the SIEM tool to view and act on current threats and look over historical data of past threats.
- Antivirus: Antivirus security software can help protect against outside threats and assist you in identifying and removing threats that have already infiltrated your defenses. Ideally, antivirus tools can help protect you from issues like Trojans, worms, adware, spyware, ransomware, and all manner of malicious activity. A robust antivirus tool should address a range of these threats and provide full visibility into cyberattacks.
No matter what kind of IT security management tools you implement, be sure their features are robust. Platforms should come with automatic updates and patching to ensure reliability. Be sure the software takes data encryption into account, if relevant. In addition, look for a tool that checks potential threats against an updated database of known global threats. New cyberattacks designed to avoid traditional detection methods can spread incredibly quick, and your security solution should continually “evolve” to stay one step ahead.
Overall, if you’re looking to protect your organization against a range of data breaches, it’s crucial to assess potential threats, understand how an attack might occur, and choose powerful, business-grade tools designed to fully protect networks, servers, and sensitive data.


