Email is one of the most popular methods of online correspondence, especially for businesses. But a large proportion of malware installed on compromised networks originates from an email attachment. Without the right security measures, email can easily serve as a gateway for phishing attempts and malicious links and attachments.
Your business email accounts are prime targets for cybercriminals, as a likely source of valuable business and client data. Implementing email security best practices can help you mitigate the risk of email-borne cyberattacks by helping you prevent malicious individuals from leveraging email as a means of accessing your data and systems.
This article outlines essential business email security best practices for employees to help you establish a robust layer of email protection and safeguard email continuity. SolarWinds®Identity Monitor can make implementing enterprise email security best practices for employees significantly easier by monitoring breach exposure and keeping you informed of potential email threats and vulnerabilities. Identity Monitor allows you to check your email exposure for free. Click here to find out if your corporate credentials have been leaked.

Essential Email Security Best Practices
These email security best practices for employees can help you protect your company’s email accounts against the risk of email-borne cyberattacks, such as email spoofing and malicious attachments.
-
Train Your Staff in Cybersecurity Awareness
Although often overlooked, cybersecurity awareness training is a critical aspect of a successful cybersecurity strategy. Every single employee, regardless of seniority, should be given comprehensive cybersecurity awareness training. Whether you’re an enterprise operating in multiple continents or a small business just getting yourself off the ground, you are a target for cyberattacks. It’s a common misconception that small businesses are safe from cybercrime—in fact, small businesses are often the victim of cyberattacks simply because they’re less likely to have advanced security measures in place, making them easy targets.
Given the constant threat of email-borne cybercrime, it’s crucial for your employees to have a robust understanding of how email-based threats operate and how they can be avoided. Employees should be trained in how to respond when they believe they’ve received a malicious or suspicious email. If a phishing email is received, staff can respond in two ways. They can either open the attachment, which will infect their device with the malicious program and potentially cause a large-scale breach or ransomware attack on your company—or, they can move the email to the junk folder and forward it to the IT department, keeping them informed of email-borne threats. The IT department may then choose to send an email or memo to other employees warning them against opening emails of this nature. If the cybercriminal responsible sends the email to other employees, they’re less likely to be fooled into opening the attachments.
As this example demonstrates, comprehensive cybersecurity awareness training can make a difference. If, however, the employee who receives a malicious email doesn’t know how to differentiate a suspicious email from a safe one, the risk of falling victim to a cyberattack is significantly higher. As such, cybersecurity awareness training should teach employees how to identify and flag suspicious emails. Training should be updated regularly, to reflect evolving scam tactics.
Here are a few other cybersecurity awareness tips you should be include in training sessions:
- Emphasize the importance of keeping business and personal emails separate
- Discourage employees from checking business emails from their mobile phones
- Encourage employees to update email passwords regularly
- Encourage employees to use complex, unique passwords
-
Ensure Password Security
Passwords are our primary line of defense against cybercrime and unauthorized access to our sensitive data. But they are only as strong as we make them. There are several ways you can help ensure passwords are strong and secure. We recommend implementing a password policy for employees to follow, to ensure they understand what makes a strong password and they’re not inadvertently creating vulnerabilities in your network. A password policy should include the following, as standard:
- Reset passwords regularly
- Ensure passwords are unique and not reused across multiple accounts
- Ensure passwords don’t contain common phrases or personal information (i.e., birthdays, names, etc.)
- Ensure passwords are at least eight characters in length and include lowercase and uppercase letters, as well as symbols and numbers
- Discourage password sharing
- Store passwords safely (i.e., in a password management solution with advanced encryption methods)
Using strong passwords plays a critical role in protecting your email accounts and is an essential email security best practice. Implementing a password policy can help you enforce password security.
-
Develop a Cybersecurity Plan
A password policy should be a part of a wider cybersecurity plan. A comprehensive, well-developed cybersecurity plan can help your company avoid many of the threats and risks lurking online. When developing it, make sure you account for email-borne threats. You should include policies, guidelines, requirements, and recommendations regarding how to implement and use all the technologies your business uses, including email communication channels.
Establishing a cybersecurity plan is very important, because even the most successful enterprise email security best practices will be rendered obsolete if your company is vulnerable to cyberattack in other areas.
-
Use an Antivirus Solution
Many enterprise antivirus solutions come equipped with mail filtering and scanning functionality for files and websites. These features can help your company proactively identify email-based threats, reducing the likelihood of your devices and networks becoming compromised. We recommend setting up your antivirus software to work with your mail proxy/relayer, if possible—this will enable your antivirus solution to scan business emails and filter out malicious emails, helping prevent your employees from ever receiving them.
-
Implement Email Security Solutions
In addition to antivirus software, you should also consider implementing other email security tools, such as malware protection and mail protection solutions. Business-grade email protection tools can significantly reduce the chances of human error leading to business email compromise and help you detect and protect against targeted attacks.
An identity monitoring tool is a type of email security solution that can also be extremely useful to businesses. Identity monitoring solutions can help prevent account takeover, reduce response time with early warnings, notify you of exposed credentials, and monitor multiple domains. For instance, SolarWinds Identity Monitor is an easy-to-use, comprehensive, and scalable email security service designed to keep your corporate credentials safe and notify you when they are leaked.
SolarWinds Identity Monitor
SolarWinds Identity Monitor is a versatile email security solution designed to help you stay ahead of threats. This SaaS solution can monitor IP addresses for possible malware, allowing you to add an IPv4 address or IPv4 network CIDR to your watchlist to be monitored for botnets and breaches. When an IP address is matched from a botnet, this could indicate a staff member has active credential-stealing malware on their device.
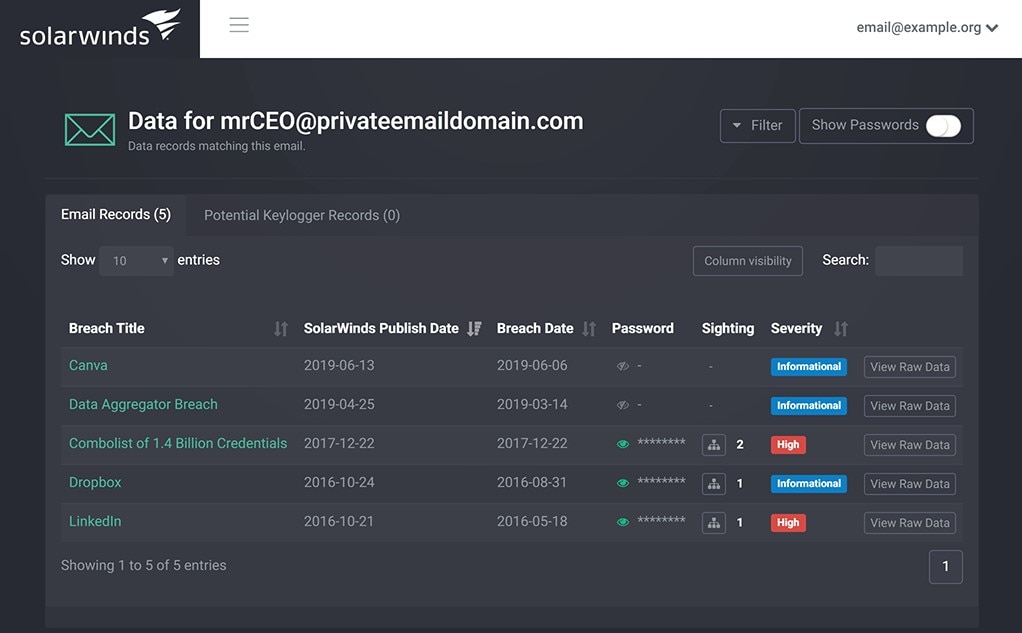
This solution can also monitor private email credentials for key employees and multiple domains to afford you complete coverage. This is especially useful for large organizations likely to have multiple email domains. With Identity Monitor, you can monitor your email domains for exposure in a data breach. You will be notified if any of your domains appear in a data breach, so you can take action to prevent account takeover.
To help prevent account takeover and contain your risk if credentials are exposed, Identity Monitor sends immediate notifications and offers expert remediation advice. This tool also allows you to force a password reset for at-risk accounts before they can be used to launch an attack on your business assets.
Identity Monitor can monitor past, present, and future exposure, continuously monitor for new leaks, and give you complete visibility of credential safety. By adding credential leak monitoring to your email protection toolset, you can gain new insight into how safe your business truly is. This discourages complacently and serves as a constant reminder of the dangers of improperly managed email security.
Getting Started
By implementing the enterprise email security best practices for employees listed in this guide, you can help ensure your business email accounts are secured against email-borne threats. None of these email security best practices are designed to work alone—to achieve robust email security, you should be implementing multiple email security best practices to mitigate potential vulnerabilities and threats. To stay informed of threats to your email security, try checking your exposure with SolarWinds Identity Monitor.


