Active Directory is essentially a registry containing all the information about a network, including users, groups, computers and printers, and servers. Each of these things, whether physical or virtual, is considered an “object” in Active Directory, and has various attributes assigned to it, such as a name, number, or group membership.
Active Directory is used by network administrators to assign privileges and access to the system, as well as to control how various objects authenticate to the system and show they’re trusted. If Active Directory is compromised, the components keeping your IT system secure could be accessed maliciously, which could result in your organization’s data and assets being compromised. This is why maintaining Active Directory security is absolutely vital for keeping your organization safe from intrusion.
In this article, I define what exactly Active Directory security groups are (including their functions and scope) before sharing my quick guide to Active Directory security groups’ best practices. I also explain why I think SolarWinds® Access Rights Manager is the best tool available on the market today to help support your AD security efforts.
Jump ahead to my 6 AD security groups best practices:
- Protect default groups and accounts
- Set up password protections
- Monitor and audit
- Minimize excesses
- Always update
- Make a plan
What Are Active Directory Security Groups?
In Active Directory, the layout follows a tier structure comprising domains, trees, and forests. A domain is a group of objects (such as users or devices) sharing the same Active Directory database. A tree is a collection of domains, and a forest is a collection of trees. Objects in separate forests can’t interact with each other, and this acts as a structural security boundary. Sometimes people get confused and think domains are the security boundary when they’re management and organizational boundary—the forest is the only real security boundary. Your domains aren’t protected from each other unless they’re in separate forests.
Active Directory groups users, devices, and other objects so they can be managed as a single object. There are two main types of groups in Active Directory: distribution groups and security groups.
Distribution groups are solely for email distribution, for use with Microsoft Exchange or Outlook, for example. You can add or remove users from the group depending on whether you want them to receive the relevant email messages.
Security groups are much more important and need to be protected with clear security protocols, as they govern user and computer access to resources. Some of these resources could be confidential, sensitive, or critical to the organization. As a result, these security groups need to be carefully managed in terms of access, permissions, and auditing.
Functions of Active Directory Security Groups
You can do two main things with Active Directory security groups:
- Assign user rights. User rights can be assigned to a security group, to determine what the users within the group can do within a domain or forest. For some security groups, user rights are automatically assigned for administration purposes.
- Assign permissions for resources. User permissions are different than user rights. Rights determine the abilities users have, whereas permissions relate to access to resources. Some permissions are automatically assigned to default security groups, including the Account Operators and Domain Admins groups. These groups are created automatically when you create an Active Directory domain. Due to their automatic security permissions, you need to take extra care in managing these groups.
Scope of Active Directory Security Groups
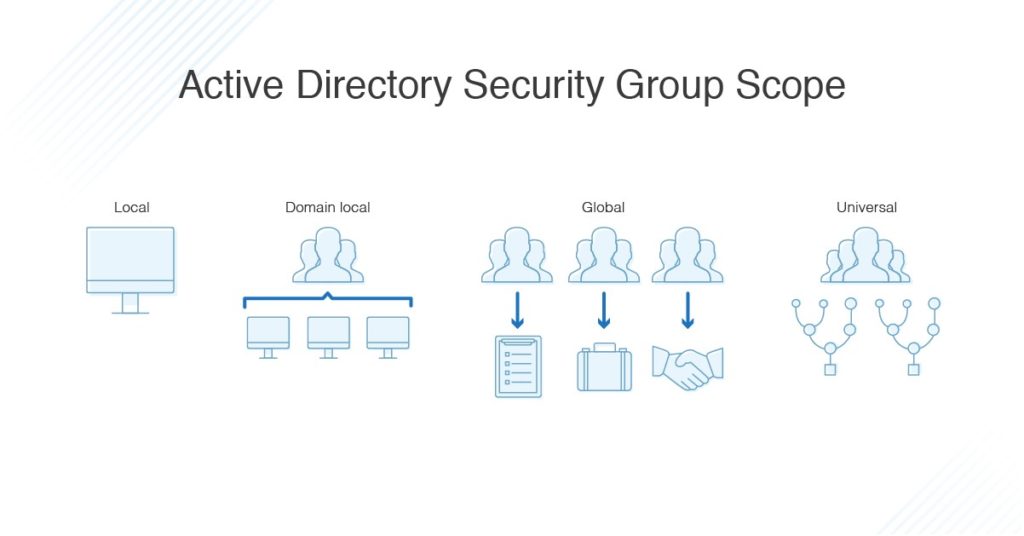
Active Directory groups are characterized by their scope. Scope determines which users can belong to the group, as well as where within the forest or domain the group’s permissions can be applied. There are four levels of scope:
- Local – Local groups are specific to and available only on the computer they were created on.
- Domain local – Domain local groups can be applied anywhere in the domain and can be useful for managing resource permissions. A domain local group can include members of any type, as well as members from trusted domains. You could, for example, create a domain local group for managers with permissions for various folders on one or more servers.
- Global – Global groups define collections of domain objects (users, computers, groups), typically based on business roles. They’re usually used as role-based groups of users or computers, e.g., for marketing or HR.
- Universal – Universal groups are for use in multi-domain forests. You can define roles and set up permissions for resources spread across more than one domain. A universal group is stored in the domain you create it in, but the Group Catalog stores the group membership and replicates this membership forest-wide.
Active Directory security groups include Account Operators, Administrators, DNS Admins, Domain Admins, Guests, Users, Protected Users, Server Operators, and many more. Understanding how to approach all these groups with a best-practice mindset is key to keeping your system secure.
Active Directory Security Groups Best Practices
Attackers can enter your system by obtaining the credentials for a user, or by compromising an account using a virus, through which they can then give themselves further user privileges to access resources. If an attacker gains entry to your Active Directory and compromises a vital security group or account, your entire system can quickly be compromised as well.
Following these Active Directory security best practices can help ensure your Active Directory can’t be compromised.
- Protect default groups and accounts. Default security groups are created when you set up an Active Directory domain, and some of these groups have extensive permissions. Take care to manage these groups properly, as gaining access to one means gaining access to a powerful tool. For example, make sure there are no day-to-day accounts in the Domain Admins group, other than the default Domain Administrator user. If another person needs domain admin access, put their account in the group while they need it, and then remove it again when their job is done.
Only use the Domain Administrator account for domain setup and disaster recovery; nobody should use this account for anything other than those purposes. Put the password in a secure location only accessible on a need-to-know basis.
Make sure the Local Administrator account is disabled, as it’s often configured with the same password on every domain and has the same SID across installations, which is often known by attackers. Disable it to prevent it from becoming an access point for intruders. - Set up password protections. Make sure all your users have 12-character passphrases (three or more random words put together), not 8-character complex passwords. And if a password is attempted incorrectly three times, the user should be locked out. Use two-factor authentication for extra password protection. You can use Microsoft MFA, or other tools such as Duo and RSA.
- Monitor and audit. Carefully and continuously monitor your events, logs, and Active Directory access processes. Keep an eye out for unusual or malicious activity, including spikes in bad login attempts or locked-out accounts, changes to any privileged groups, disabled or removed antivirus software, or logon/logoff events.
Also, it’s important to regularly take stock of who has access to what and change or remove permissions whenever necessary to make sure nobody has more security access than they need. My go-to tool for managing user accounts is SolarWinds Access Rights Manager, which can not only manage your security groups but also provide insight into which users are in which groups.
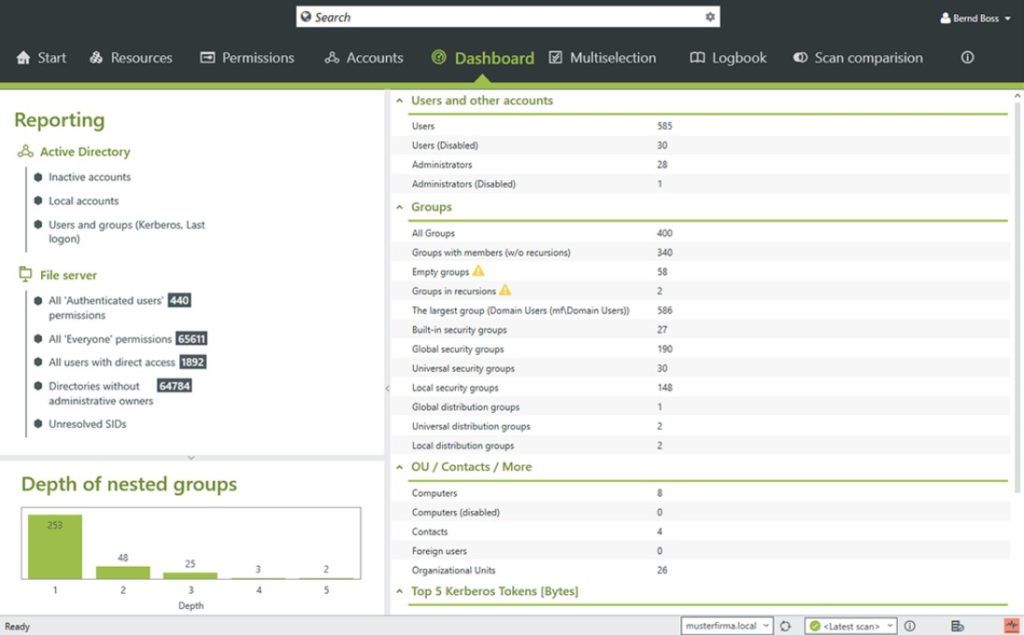
Access Rights Manager equips you to regularly audit your systems and manage, monitor, and analyze your group policy and Active Directory. It enhances security by keeping track of whether changes have been made, when they were made, and by whom, and it helps identify any high-risk accounts. - Minimize excesses. Install only the tools and functions you need, and make sure accounts only have the necessary permissions and are part of groups they need to be in. If you give everyone a lot of permissions or access to your system, it makes it much harder to detect internal threats and leaves your system vulnerable if you have a lot of people in high-access security groups.
- Always update. Use a patch manager to keep all software on your system up-to-date. A good patch manager will let you know if there are vulnerabilities in any of your software, and will also provide information on any threats it detects, including attackers targeting Active Directory loopholes in particular.
- Make a plan. Develop a clear plan for approaching your Active Directory security groups management, setup, maintenance, and what to do if an account is breached. Cyberattackers can quickly gain access to your system and take down the entire network, and it’s important to have a response plan in place, so everybody knows what to do straightaway. Prioritize server recovery and conduct walkthroughs and training to ensure response times are as fast as possible.
How to Set Up Security Groups in Active Directory
By setting up good security protections, minimizing exposure, and continuously monitoring, you will be well-positioned to keep your systems safe from attack. This is why I recommend using a solution like Access Rights Manager from SolarWinds to support monitoring and managing your Active Directory security groups and help ensure your overall organizational safety.


