Not all IT professionals are clear on IDS vs. IPS, even though these concepts are important for overall network security. Think of it this way: security alerts and responses go together. A burglar alarm won’t do you much good if it doesn’t somehow deter crime in progress. On the other hand, having the cops show up at your house won’t help if it’s a false alarm. Sometimes an alert is enough, and sometimes you need a well-calibrated response. You can essentially translate these ideas to IT security to understand the function of intrusion detection systems (IDS) and intrusion prevention systems (IPS).
What Is IDPS?
It’s important to note that intrusion detection systems and intrusion prevention systems are both important parts of network integrity and include concepts that you may want to consider for IT security actions and decisions. Sometimes the systems overlap, and sometimes they’re combined or referred to together as IDPS. Although IPS is becoming a more dominant security method, it’s important to be familiar with both. In this article, I’ll provide an overview of what you need to know about IDS and IPS. Plus, I’ll point out where to start with security tools for any enterprise that needs a better intrusion detection or prevention strategy.
What Is an Intrusion Detection System?
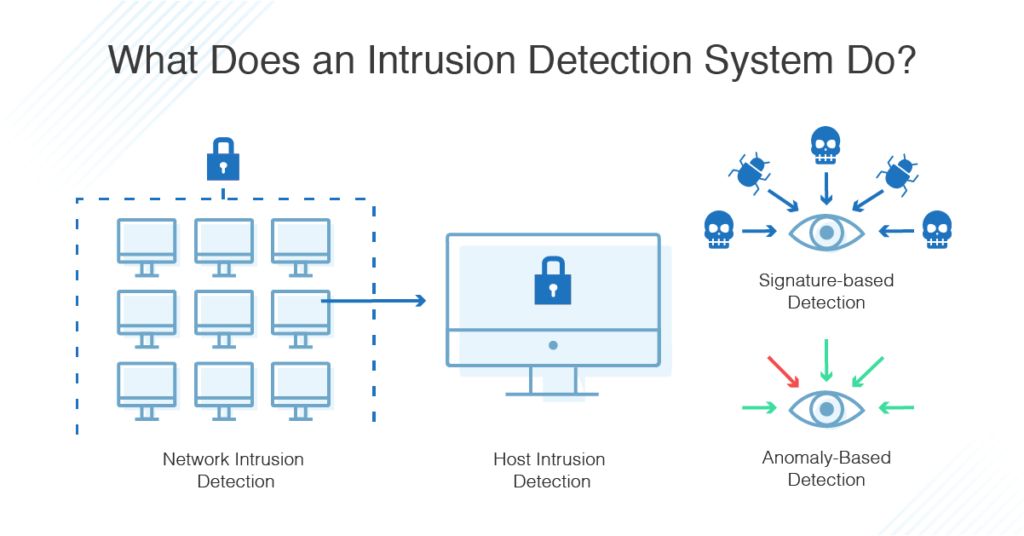
An IDS monitors your network for possible dangerous activity, including malicious acts and violations of security protocols. When such a problem is detected, an IDS alerts the administrator but doesn’t necessarily take any other action. There are several types of IDS and several methods of detection employed.
- Network Intrusion Detection System (NIDS): A network intrusion detection system (NIDS) monitors packets moving into and out of a network or subset of a network. It could monitor all traffic, or just a selection, to catch security threats. A NIDS compares potential intrusions to known abnormal or harmful behavior. This option is preferred for enterprises, as it’s going to provide much broader coverage than host-based systems.
- Host Intrusion Detection System (HIDS): A host intrusion detection system lives on and monitors a single host (such as a computer or device). It might monitor traffic, but it also monitors the activity of clients on that computer. For example, a HIDS might alert the administrator if a video game is accessing private files it shouldn’t be accessing and that have nothing to do with its operations. When HIDS detects changes in the host, it will compare it to an established checksum and alert the administrator if there’s a problem.
HIDS can work in conjunction with NIDS, providing extra coverage for sensitive workstations and catching anything NIDS doesn’t catch. Malicious programs might be able to sneak past a NIDS, but their behavior will be caught by a HIDS.
Types of Intrusion Detection Systems
There are two primary types of intrusion detection systems you should be aware of to ensure you’re catching all threats on your network. Signature-based IDS is more traditional and potentially familiar, while anomaly-based IDS leverages machine learning capabilities. Both have their benefits and limitations:
- Signature-based: Signature-based IDS relies on a preprogrammed list of known attack behaviors. These behaviors will trigger the alert. These “signatures” can include subject lines and attachments on emails known to carry viruses, remote logins in violation of organizational policy, and certain byte sequences. It is similar to antivirus software (the term “signature-based” originates with antivirus software).
Signature-based IDS is popular and effective but is only as good as its database of known signatures. This makes it vulnerable to new attacks. Plus, attackers can and do frequently disguise their attacks to avoid common signatures that will be detected. Also, the most thorough signature-based IDS will have huge databases to check against, meaning big bandwidth demands on your system.
- Anomaly-based: Anomaly-based IDS begins with a model of normal behavior on the network, then alert an admin anytime it detects any deviation from that model of normal behavior. Anomaly-based IDS begins at installation with a training phase where it “learns” normal behavior. AI and machine learning have been very effective in this phase of anomaly-based systems.
Anomaly-based systems are typically more useful than signature-based ones because they’re better at detecting new and unrecognized attacks. However, they can set off many false positives, since they don’t always distinguish well between attacks and benign anomalous behavior.
What Is an Intrusion Prevention System?
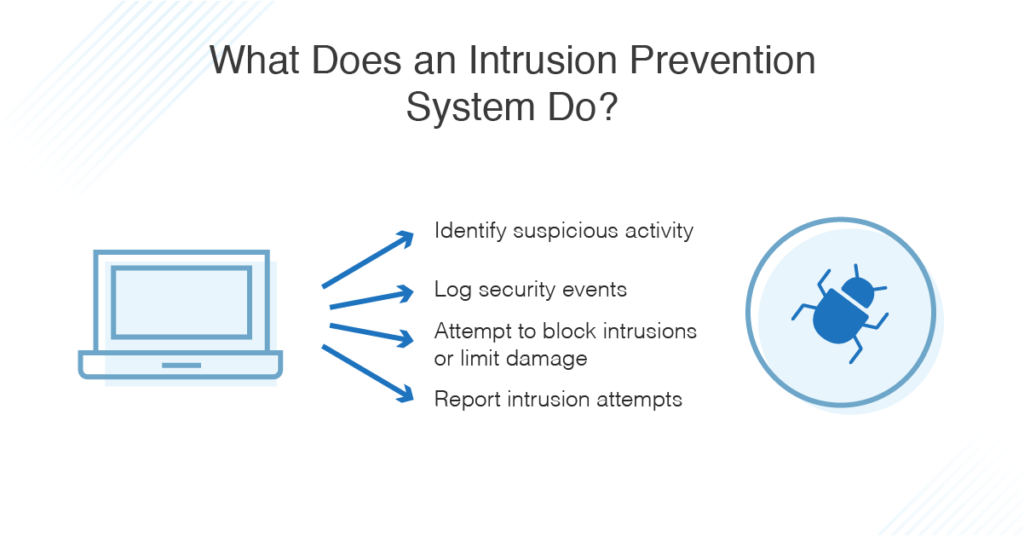
Some experts consider intrusion prevention systems to be a subset of intrusion detection. Indeed, all intrusion prevention begins with intrusion detection. But security systems can go one step further and act to stop ongoing and future attacks. When an IPS detects an attack, it can reject data packets, give commands to a firewall, and even sever a connection.
IDS and IPS are similar in how they’re implemented and operate. IPS can also be network- or host-based and can operate on a signature or anomaly basis.
Types of Intrusion Prevention Systems
A robust IT security strategy should include an intrusion prevention system able to help automate many necessary security responses. When risks occur, a prevention tool may be able to help quickly to thoroughly shut down the damage and protect the overall network.
- Network-based Intrusion Prevention Systems (NIPS): As the name suggests, a NIPS covers all events on your network. Its detection is signature-based.
- Network Behavior Analysis (NBA): NBA is similar to NIPS in that it provides network-wide coverage. But unlike NIPS, NBA operates on anomalies. Like anomaly-based IDS, NBA requires a training phase where it learns the network’s baseline norm.
NBA also uses a method called stateful protocol analysis. Here, the baseline norm is pre-programmed by the vendor, rather than learned during the training phase. But in both cases, the IPS is looking for deviations rather than signatures.
- Wireless-based Prevention Systems (WIPS): Protecting your network brings its own unique challenges. Enter WIPS. Most WIPS have two components, including overlay monitoring (devices installed near access points to monitor the radio frequencies) and integrated monitoring (IPS using the APs themselves). Combining these two, which is very common, is known as “hybrid monitoring.”
- Host-based Intrusion Prevention Systems (HIPS): HIPS live on and protect a single host, providing granular coverage. They are best used in conjunction with a network-wide IPS.
Differences Between IDS and IPS
There are several differences between these two types of systems. IDS only issues alerts for potential attacks, while IPS can take action against them. Also, IDS is not inline, so traffic doesn’t have to flow through it. Traffic does, however, have to flow through your IPS. In addition, false positives for IDS will only cause alerts, while false positives for IPS could cause the loss of important data or functions.
The Best IDS/IPS Software
At this point, IPS has largely overtaken IDS in the IT industry. And my top choices contain elements of both.
An intrusion detection software can stand up to the demands (and more) of IT professionals. If you’re having trouble keeping up with the manual demands of IDS for multiple networks, IDS software is there to automate a lot of those processes. As I noted, an IDS is only as good as the list of threats it has cataloged, and an IDS tool like SolarWinds ® Security Event Manager provides regular updates to its known threats from the leading databases. Plus, it’s audit-ready, putting all of the documentation needed at your fingertips.
SolarWinds Security Event Manager (formerly Log & Event Manager) provides thorough event logging and has a major emphasis on automated threat responses. These include any actions you could need to terminate a threat, from jetting a USB drive to disabling a domain user. The system comes with many pre-programmed rules for responses and allows you to program your own.
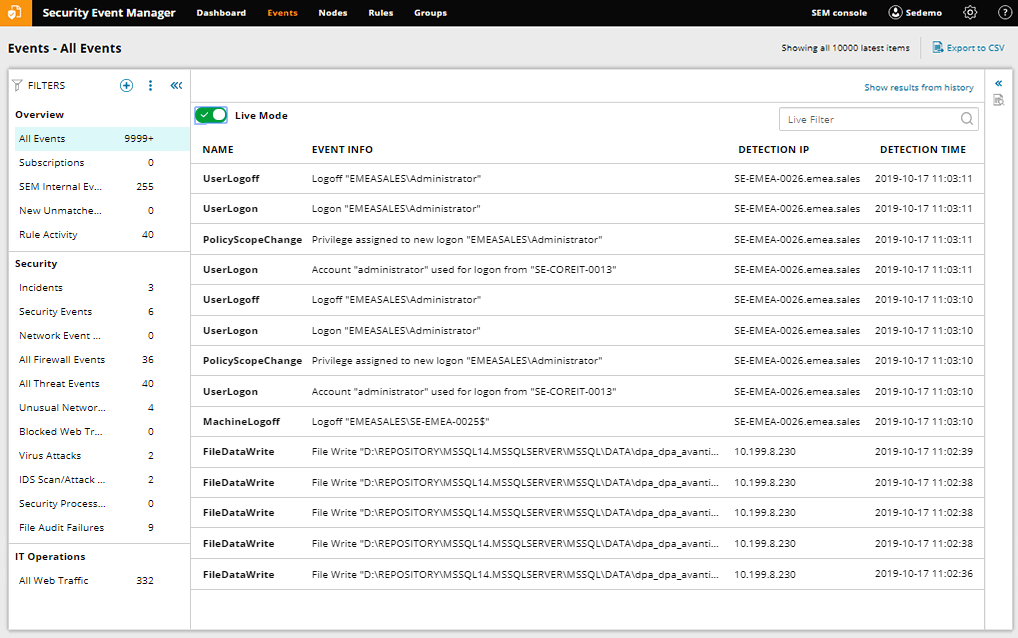
It comes with a great feature called the Snort IDS log analyzer tool, which works with Snort, a popular free, open-source IDS/IPS software. Enterprise-grade IT professionals need more functionality than open-source programs can offer, and Snort IDS log analyzer layers on top of Snort to provide real-time, automated analysis of all that data. Plus, it can also activate the responses mentioned above.
To wrap it up, there’s a lot of overlap between IDS and IPS, and IPS mostly dominates the scene now. If you’re looking for an enterprise-grade product for a better security strategy, my take is that Security Event Manager is one of the best IDS/IPS tool on the market today.


