Not so long ago, plain-text log management was a widespread, grueling, and lengthy process. Plain-text data isn’t without its uses—in fact, under certain circumstances, it can be of great value—but it can’t replace a sophisticated log management solution when it comes to complex analysis and gaining advanced insight into infrastructure. If you want to optimize your code quality, then you’ll benefit significantly from investing in a suitable log monitoring tool.
Tools used for monitoring and logging can vary immensely. The market is saturated with competitors, each claiming to offer a unique take on log file monitoring and alerting. Some will prioritize usability; others will choose quantity of features over quality, or perhaps aspire to technological sophistication at the expense of user-friendliness. To help you make the right choice for your business, I’ve put together a list of the best monitoring and logging tools available this year.
Read also: How Your Website Can Benefit From Log Monitoring
Table of content
What Is a Log Monitoring Tool?
How Do Log Monitoring & Event Logging Tools Work?
Why are Log Monitoring Tools Important?
What is the Best Log Monitoring Tool?
1. Security Event Management (SEM) by SolarWinds
17. Splunk Enterprise Security
How to Choose the Right Log Monitoring Tool for Your Needs
What Is a Log Monitoring Tool?
A software program created to gather, examine, and handle log data produced by different devices, programs, and systems on a network is called a log monitoring tool. These tools offer real-time insights into system performance and behavior, enabling organizations to monitor, detect, and respond to operational concerns, security risks, and compliance needs. Log monitoring solutions assist IT workers in finding patterns, resolving issues, and guaranteeing the uninterrupted operation of vital infrastructure by methodically examining log data.
Key Features and Functionalities
- Real-time Monitoring: Real-time monitoring gives users instant access to information about system activity and possible problems as they arise.
- Data Collection: Compiles log data from a variety of sources, such as security systems, servers, apps, and network devices.
- Log Management: Centralized log management makes analysis and reporting simpler by combining log data onto a single, cohesive platform.
- Notifications and Alerts: Notifies users instantly of any anomalies, threshold breaches, or specified events.
- Automated Analysis: Makes use of machine learning algorithms to automatically examine log data to spot trends, abnormalities, and patterns.
- Visualization and Reporting: Provides comprehensive reports, graphs, and dashboards to help with the comprehension and analysis of log data.
- Log Filtering: Users can search and filter log data to find particular occurrences or information quickly.
- Compliance Support: By guaranteeing correct log data retention and audit trails, compliance support helps meet regulatory requirements.
Examples of Data and Events That Log Monitoring Tools Track
Log monitoring tools track a wide variety of data and events to provide comprehensive visibility into system operations. Examples of data typically tracked include:
- system logs (e.g., login attempts, configuration changes),
- application logs (e.g., error messages, transaction records),
- network logs (e.g., traffic patterns, access attempts),
- security logs (e.g., firewall activities, intrusion detection alerts).
By monitoring these diverse data sources, log monitoring tools can detect performance issues, unauthorized access attempts, configuration errors, and other critical events that may impact the security and functionality of an organization’s infrastructure.
How Do Log Monitoring & Event Logging Tools Work?
Log monitoring and event logging tools function by systematically collecting, analyzing, and managing log data from various sources within an organization’s IT infrastructure. These tools follow a multi-step process to ensure comprehensive monitoring and effective incident response.
- Log Collection: The process begins with agents deployed on various devices (servers, applications, network equipment) or connectors established with cloud-based services. These agents and connectors continuously collect log data generated by the respective systems.
- Log Parsing and Normalization: Raw log data often varies in format depending on the source. The log monitoring tool employs parsing techniques to extract relevant information from each log entry, including timestamps, severity levels, event descriptions, and user data. This process transforms the raw data into a standardized format, enabling easier analysis and consolidation from diverse sources.
- Log Indexing and Storage: Once parsed, the normalized log data is indexed for efficient searching and retrieval. The tool stores the indexed logs in a centralized repository, providing a comprehensive historical record of system activity.
- Real-time Analysis and Alerting: The log monitoring tool continuously analyzes the log streams in real-time. It can be configured to identify specific events or patterns based on predefined rules or custom filters. Upon detecting critical events or errors, the tool triggers automated alerts via email, SMS, or other designated channels, notifying IT teams for immediate investigation.
- Data Visualization and Reporting: Log monitoring tools provide a user-friendly interface to explore and analyze log data. They leverage dashboards, charts, and graphs to present complex information in a visually intuitive manner. This allows IT professionals to identify trends, pinpoint anomalies, and gain a deeper understanding of system health and performance.

Why are Log Monitoring Tools Important?
In today’s IT landscape, maintaining the smooth operation and security of your systems is crucial. Log monitoring tools play a vital role in achieving these goals by offering a wealth of benefits:
- Enhanced Troubleshooting Efficiency: Log files provide a treasure trove of information about system activity. By analyzing these logs, IT professionals can quickly identify the root cause of issues, saving valuable time and resources compared to manual troubleshooting methods.
- Improved System Performance: Log monitoring tools can detect performance bottlenecks and resource constraints by analyzing resource utilization data within the logs. This empowers IT teams to take proactive measures like scaling resources or optimizing configurations, ensuring optimize system performance.
- Real-time Threat Detection and Security: Security events like unauthorized access attempts, suspicious logins, or malware activity are often reflected in log files. Log monitoring tools can be configured to detect these events in real-time, enabling IT teams to respond swiftly to potential security breaches and mitigate risks.
- Simplified Compliance Management: Many regulations require organizations to maintain detailed audit trails of system activity. Log monitoring tools can streamline compliance efforts by facilitating log collection, secure storage, and long-term archiving, ensuring adherence to industry standards and regulations.
- Proactive Problem Identification: By analyzing trends and patterns within log data over time, IT teams can proactively identify potential issues before they escalate into critical problems. This preventive approach minimizes downtime and disruptions to business operations.
- Enhanced Decision-Making: Log analysis provides valuable insights into system usage, application behavior, and user activity. This data can be used to make informed decisions about resource allocation, capacity planning, and application optimization efforts.
Read more: 9 Best SIEM Tools for 2024
What is the Best Log Monitoring Tool?
The benefits of employing a log monitoring tool are substantial. The right tool can boost productivity, make meeting regulatory compliance requirements easier, inform marketing strategies, assist with troubleshooting, optimize security, and help you analyze your business processes. This section of the guide looks at the best-paid and open-source software on the market.
1. Security Event Management (SEM) by SolarWinds
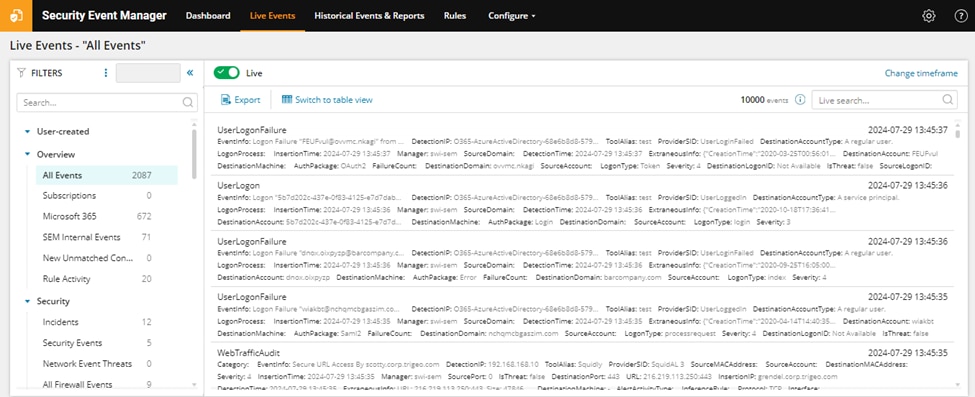
© 2024 SolarWinds Worldwide, LLC. All rights reserved.
Security Event Management (SEM) by SolarWinds is a comprehensive log and event management solution designed to enhance your security posture by providing real-time monitoring, event correlation, and automated responses to security incidents. It is particularly favored for its user-friendly interface and powerful features that help organizations detect, analyze, and respond to security threats efficiently.
Key Features:
- Centralized Log Management: Collects logs from a wide range of security devices and applications, consolidating them into a single platform for unified analysis and threat detection.
- Advanced Correlation Rules: Leverages pre-built and customizable correlation rules to identify suspicious activity patterns that might indicate potential security breaches.
- Incident Response Management: Offers tools to streamline the incident response process, including investigation, containment, eradication, and recovery procedures.
- Compliance Reporting: Simplifies compliance reporting by providing out-of-the-box reports that meet various industry standards and regulations.
Advantages and Disadvantages:
One of the significant advantages of SolarWinds SEM is its ability to provide real-time insights and automated responses, which significantly reduces the time needed to detect and mitigate threats. Its compliance reporting capabilities are robust, making it easier to adhere to various regulatory requirements. The tool’s integration capabilities with other IT systems and security tools enhance its versatility.
However, the initial setup and configuration can be complex, especially for smaller organizations with limited IT resources. Additionally, while the user interface is intuitive, the tool’s extensive features may require a steep learning curve for new users. Despite these drawbacks, SolarWinds SEM remains a powerful tool for enhancing security and compliance through effective log and event management
It is worth mentioning that SolarWinds offers a 30-day free trial, during which you can fully test the tool!
2. Papertrail (SolarWinds)
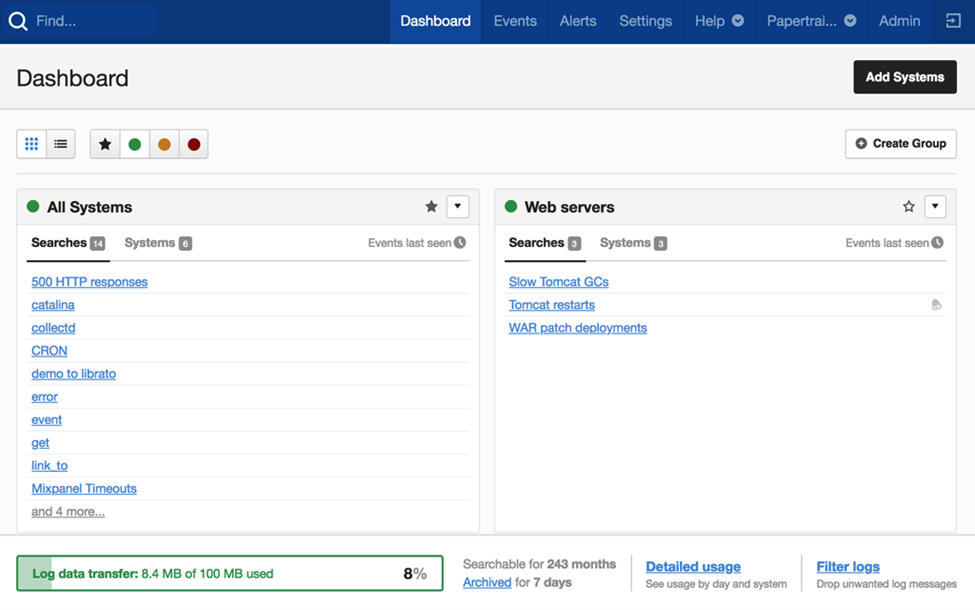
© 2024 SolarWinds Worldwide, LLC. All rights reserved.
Easy to use and reasonably priced, Papertrail is a cloud-based log management solution from SolarWinds. It is quite good at gathering, centralizing, and instantly analyzing logs from multiple sources.
Key Features:
- Real-time Log Monitoring: Provides immediate visibility into log data streams, enabling users to identify and address issues promptly.
- Advanced Search and Filtering: This feature makes it possible to efficiently explore logs using keywords and filters that are based on applications, severity levels, or timestamps.
- Seamless integration with other SolarWinds tools and third-party applications
- Intuitive web-based interface
- Alerts and notifications for specific log events
Advantages and Disadvantages:
One of Papertrail’s main benefits is its real-time log aggregation and monitoring features, which let you quickly find and fix problems as they arise. Troubleshooting can be done more effectively by drilling down into specific logs thanks to the tool’s robust search and filtering options. Its usefulness in a multi-tool scenario is further enhanced by its smooth interface with several third-party applications and other SolarWinds products. Even for people who may not have much experience with log management solutions, the user-friendly web-based interface makes it accessible and simple to use.
3. Loggly (SolarWinds)
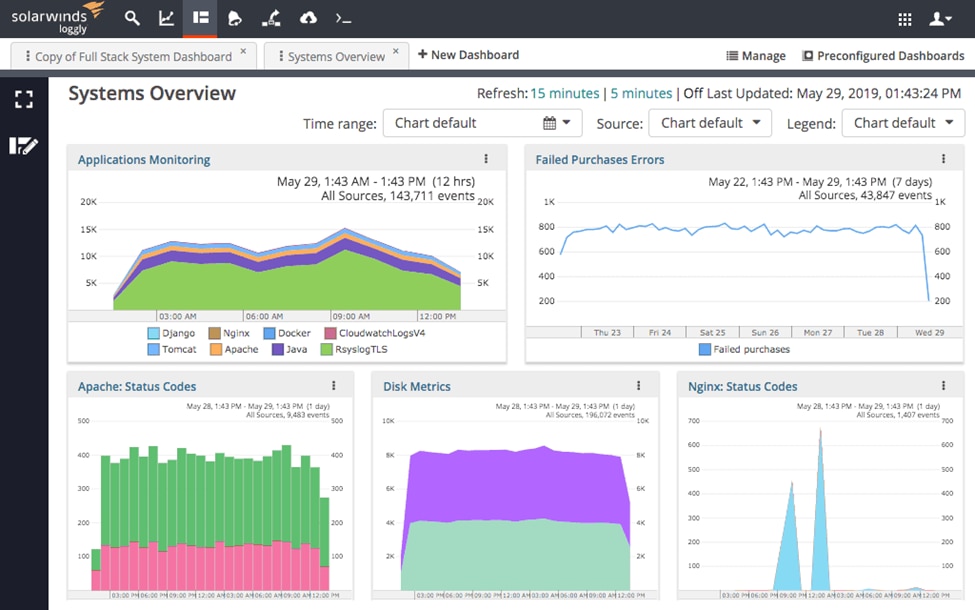
© 2024 SolarWinds Worldwide, LLC. All rights reserved.
It is a cloud-based service that makes log analysis and monitoring easier for teams working on IT operations, DevOps, and development projects. Loggly facilitates the efficient identification and resolution of problems by providing a centralized platform for the collection, analysis, and visualization of log data. This leads to improved performance and seamless operations.
Key Features:
- Centralized log collection and management
- Real-time log analysis and visualization
- Powerful search and filtering capabilities
- Pre-configured dashboards and customizable charts
- Integration with various third-party tools and services
- Anomaly detection and alerting
Advantages and Disadvantages:
Loggly’s centralized log collection and management streamline the process of handling log data from multiple sources, making it easier for you to monitor and analyze your system’s performance in real time. Its powerful search and filtering capabilities allow you to quickly locate specific log entries, facilitating efficient troubleshooting. The pre-configured dashboards and customizable charts provide visual insights into log data, helping you to better understand and respond to operational trends.
A noteworthy benefit of Loggly is its easy interaction with a wide range of third-party products and services, increasing its adaptability and usefulness in different IT contexts. Furthermore, proactive monitoring is made possible by its anomaly detection and alerting features, which let you take care of possible problems before they get worse.
The drawback of Loggly is that it can get pricey for larger enterprises or those with high log volumes. The initial setup and configuration may seem complicated to some users, particularly if they are unfamiliar with log management software. Furthermore, even though Loggly has a lot of sophisticated features, there can be a learning curve involved in making the most of it. Notwithstanding these difficulties, Loggly is still a popular option because of its extensive log management features and easy-to-use interface.
4. BetterStack
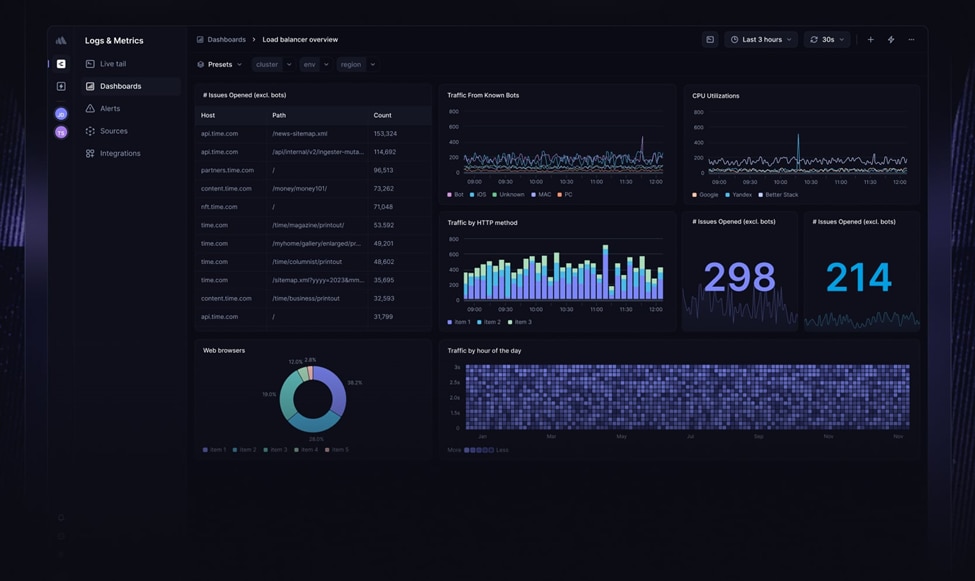
© 2024 Better Stack, Inc.
BetterStack is a modern log management and monitoring platform that combines log analysis, performance monitoring, and incident management into a single, cohesive solution. Designed for reliability and ease of use, BetterStack helps you ensure the availability and performance of your applications by providing real-time insights into system logs and metrics.
Key Features:
- Unified platform for log management and performance monitoring
- Real-time log analysis and visualization
- Customizable dashboards and reports
- Incident management and alerting
- Integration with various third-party tools and services
- Scalable and flexible infrastructure
Advantages and Disadvantages:
BetterStack’s unified platform simplifies the process of log management and performance monitoring, allowing you to gain real-time insights into your applications’ behavior and performance. The customizable dashboards and reports enable you to visualize data in a way that best suits your needs, making it easier to identify trends and anomalies.
A significant advantage of BetterStack is its integrated incident management and alerting system, which helps you respond swiftly to potential issues and minimize downtime. The platform’s scalability and flexibility ensure that it can grow with your organization’s needs, making it suitable for both small and large enterprises.
However, one potential disadvantage is that BetterStack’s extensive feature set might be overwhelming for new users to log management and monitoring tools. Additionally, while the platform offers integration with various third-party services, setting up these integrations can be time-consuming and may require a certain level of technical expertise. Despite these challenges, BetterStack stands out for its comprehensive approach to log management and performance monitoring, making it a valuable tool for maintaining the health and reliability of your applications.
5. Mezmo
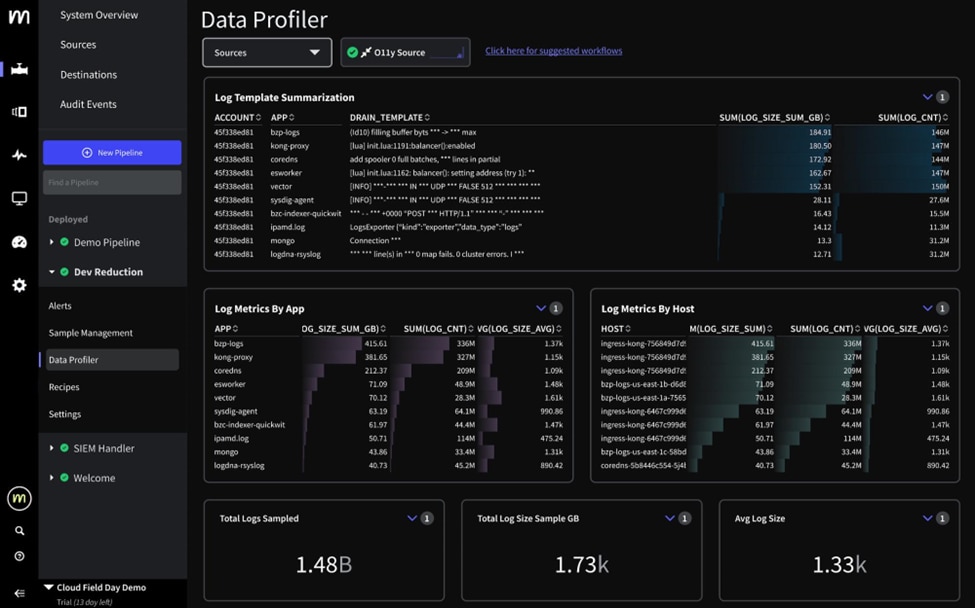
@2024 Copyright Mezmo Inc.
Mezmo, formerly known as LogDNA, is a robust log management tool designed to handle large volumes of log data efficiently. It offers real-time log analysis, allowing you to quickly identify and troubleshoot issues within your infrastructure. With its intuitive interface and powerful search capabilities, Mezmo simplifies the process of log monitoring and management.
Key Features:
- Real-time log ingestion and analysis
- Intuitive, user-friendly interface
- Powerful search and filtering capabilities
- Customizable alerts and notifications
- Comprehensive integration options with various DevOps tools
- Scalability to handle large volumes of log data
Advantages and Disadvantages:
Mezmo’s key advantage lies in its real-time log analysis and powerful search capabilities, which enable you to quickly identify and resolve issues, thereby minimizing downtime. The intuitive interface makes it accessible for users of varying technical expertise, and its customizable alerts ensure that you are promptly notified of any critical events. Additionally, Mezmo’s extensive integration options allow for seamless incorporation into existing DevOps workflows, enhancing its utility.
However, a potential disadvantage is that Mezmo’s extensive feature set may come with a learning curve for new users, potentially requiring additional time to fully leverage its capabilities. Furthermore, while the tool is highly scalable, organizations with particularly large volumes of log data might find the cost to be relatively high, making it important to assess the tool’s value in relation to its pricing. Despite these considerations, Mezmo remains a powerful and user-friendly log management solution.
6. Sematext Logs
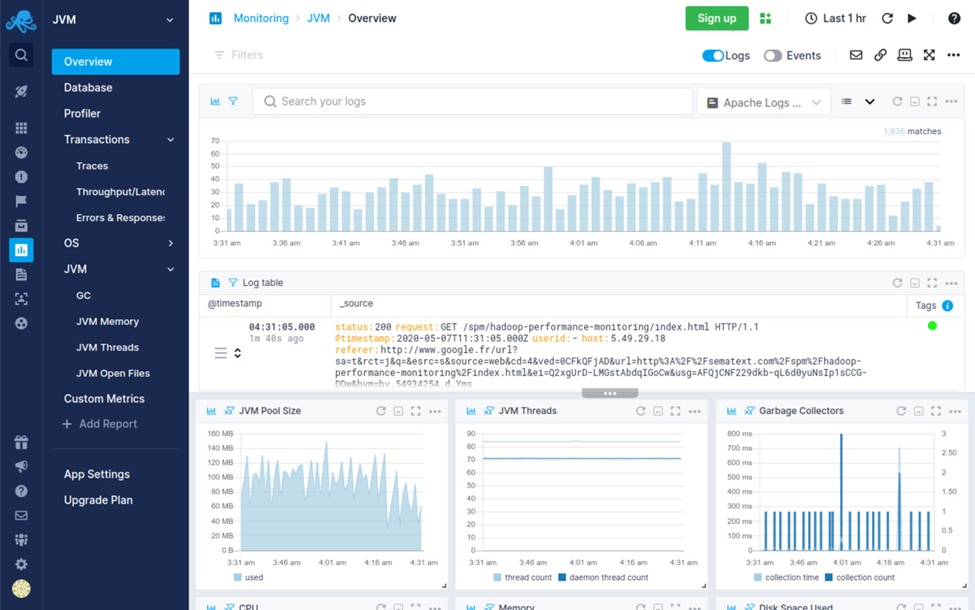
© Sematext
Sematext Logs is a feature-rich log management solution that provides real-time analysis, monitoring, and centralized logging. It is made to manage log data from many different sources and offer in-depth analysis of system security and performance. Sematext Logs is an adaptable tool for a range of IT architectures because it supports both on-premises and cloud environments.
Key Features:
- Centralized log management
- Real-time log analysis and monitoring
- Flexible alerting and notification system
- Support for cloud and on-premise environments
- Integration with various data sources and DevOps tools
- Advanced search and filtering capabilities
Advantages and Disadvantages:
Sematext Logs excels in offering a centralized platform for managing logs from many sources, giving you a thorough understanding of the security and performance of your system. Its real-time monitoring and analytical capabilities aid in the prompt identification and resolution of problems. The tool’s adaptability is increased by its ability to support both on-premises and cloud systems. Its sophisticated search and filtering tools also make it simple to find particular log entries.
The intricacy of Sematext Logs could be a drawback for novice users who require some time to become acquainted with the system. Though helpful, the wide range of customization possibilities may also result in a higher learning curve. Sematext Logs is nevertheless a reliable and adaptable log management solution that works well in a variety of IT settings, despite these possible downsides.
7. Sumo Logic
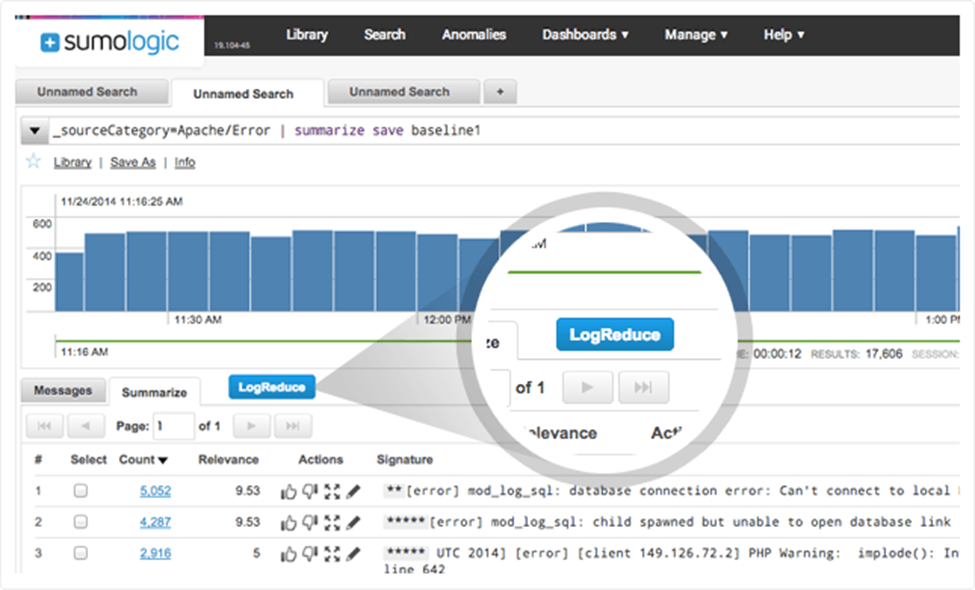
©2024 Sumo Logic
A cloud-native log management and analytics tool that offers real-time insights into log data is called Sumo Logic. It is intended to support businesses in monitoring, debugging, and safeguarding their infrastructure and applications. Sumo Logic makes proactive problem detection and resolution possible with its strong analytics and machine learning capabilities.
Key Features:
- Cloud-native architecture
- Real-time log monitoring and analytics
- Machine learning-driven insights
- Comprehensive security and compliance monitoring
- Scalable to handle large data volumes
- Integration with numerous data sources and applications
Advantages and Disadvantages:
The main benefit of Sumo Logic is its cloud-native architecture, which guarantees easy deployment and scalability. Proactive issue detection and resolution are made possible by its machine learning-enhanced sophisticated analytics and real-time monitoring. The extensive security and compliance capabilities of the platform aid in upholding a safe and law-abiding IT environment. Sumo Logic is also a flexible solution due to its integration capabilities with other data sources and apps.
However, Sumo Logic’s sophisticated features and capabilities can be very expensive, which might prevent smaller businesses from using it. Due to the platform’s complexity, proper deployment and use may also demand a significant investment of time and money. Sumo Logic provides a strong and scalable log management and analytics solution despite these difficulties.
8. LogicMonitor
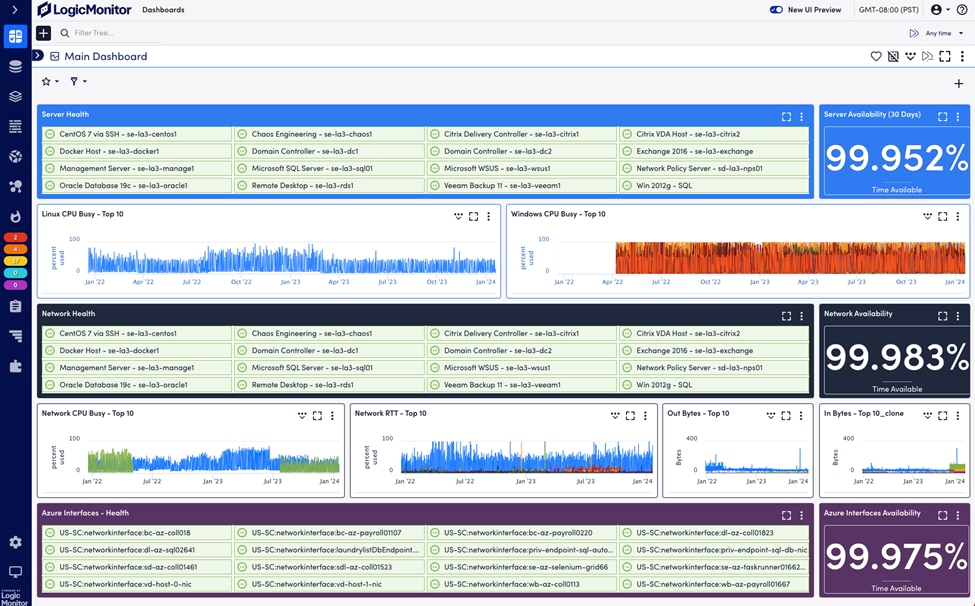
© Copyright 2024 LogicMonitor Inc
A cloud-based infrastructure monitoring tool called LogicMonitor gives you a thorough insight into your IT setup. LogicMonitor has strong log management tools in addition to its infrastructure monitoring capabilities. It enables you to gather, examine, and correlate log data to learn more about the functionality and state of the system.
Key Features:
- Comprehensive infrastructure and log monitoring
- Real-time data collection and analysis
- Automated alerting and anomaly detection
- Customizable dashboards and reports
- Integration with a wide range of IT systems and applications
- Scalable to support growing IT environments
Advantages and Disadvantages:
The primary benefit of LogicMonitor is its capacity to offer a unified view of log and infrastructure data, enabling a comprehensive approach to monitoring and troubleshooting. Its automated alerting features and real-time data collection help find and fix problems quickly. You can customize the dashboards and reports on the platform to fit your own needs and preferences for monitoring. Furthermore, LogicMonitor’s scalability guarantees that it can accommodate expanding IT infrastructures.
On the downside, novice users may find LogicMonitor to have a steep learning curve due to its vast functionality and customization choices. Even while the integration process is thorough, it can also be difficult and time-consuming. Furthermore, smaller businesses may be concerned about the expense of LogicMonitor. Notwithstanding these possible disadvantages, LogicMonitor offers an effective and comprehensive infrastructure and log monitoring.
9. Datadog
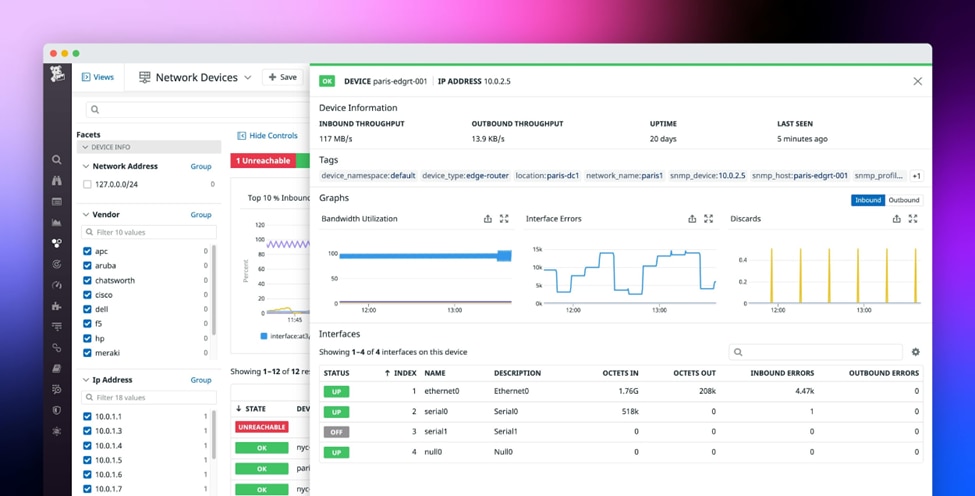
© Datadog 2024
Datadog is a platform for cloud-native security and monitoring of logs, applications, and infrastructure. It is intended to give you a unified view of your IT environment and full-stack observability. Comprehensive insights are obtained through the integration of Datadog’s security and monitoring features with its log management capabilities.
Key Features:
- Unified monitoring and log management
- Machine learning-based anomaly detection
- Seamless integration with over 450 services
- Real-time log analytics and visualization
Advantages and Disadvantages:
Datadog’s primary benefit is its capacity to offer an integrated monitoring experience by fusing log management with application and infrastructure monitoring. Its anomaly detection system, which is based on machine learning, aids in the early discovery of problems. Compatibility with a wide range of IT settings is ensured by the extensive integration with over 450 services. However, Datadog can be expensive, especially for smaller businesses, and setting it up and optimizing it can take a long time due to the intricacy of the platform.
10. Dynatrace
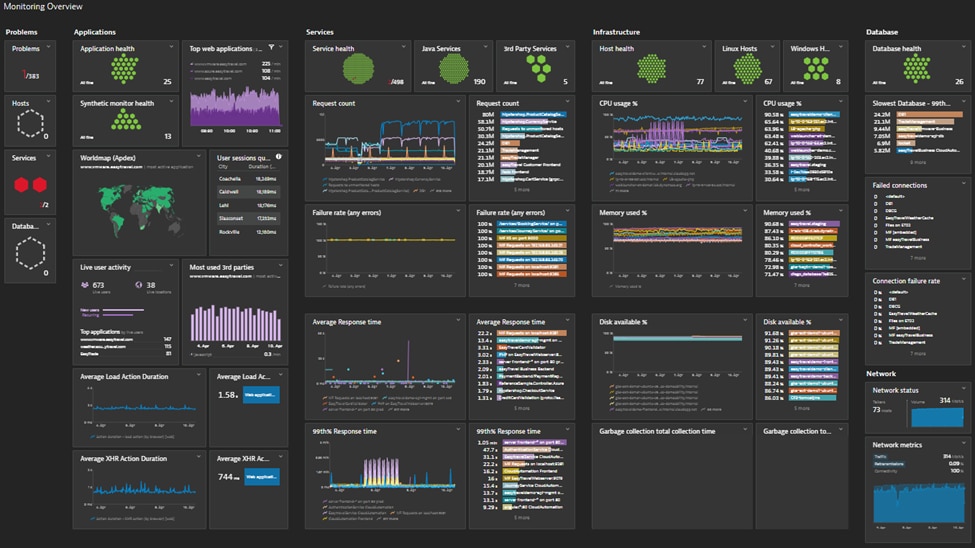
© 2024 Dynatrace LLC. All rights reserved.
A software intelligence platform called Dynatrace combines continuous automation, AI-powered observability, and monitoring. Renowned for its sophisticated application performance management (APM) skills, it provides strong log management capabilities that are intricately linked with its array of observability features.
Key Features:
- AI-driven observability and root-cause analysis
- Automatic discovery and instrumentation of log data
- Full-stack monitoring with log management integration
- Real-time monitoring and alerting
Advantages and Disadvantages:
The unique characteristic of Dynatrace is its AI-driven observability, which makes exact root-cause investigation and issue-solving possible. The setup procedure is streamlined by the automatic discovery and instrumentation of log data. Complete visibility throughout the entire IT environment is ensured by the integration of full-stack monitoring with log management. Dynatrace’s comprehensive capabilities may necessitate a steep learning curve for users to fully realize its potential, and its advanced features come at a premium cost.
11. Logstash
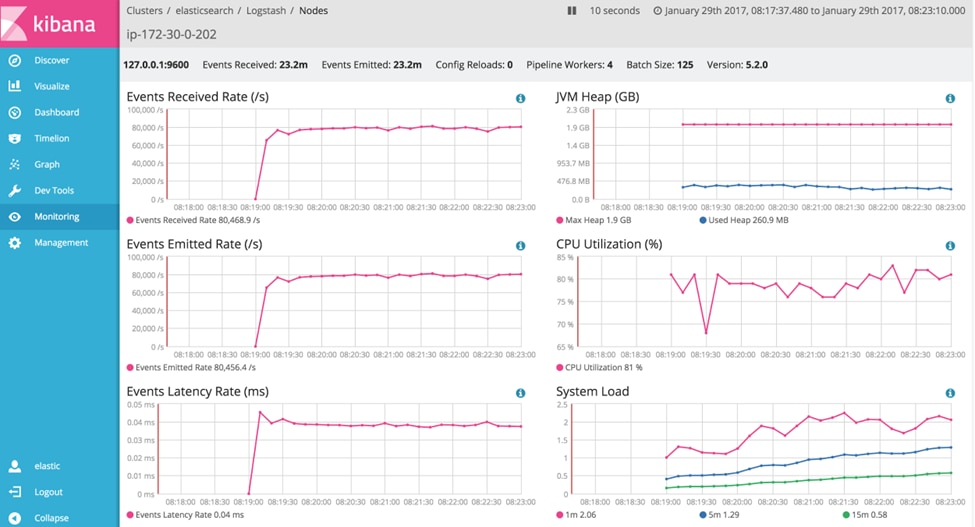
© 2024. Elasticsearch B.V. All Rights Reserved
An open-source data processing pipeline called Logstash receives, processes, and distributes log data to a central place for analysis. It is an essential part of the Elastic Stack, offering powerful log management features along with a wide range of options for data enrichment and transformation.
Key Features:
- Flexible log data ingestion and transformation
- Integration with Elasticsearch and Kibana
- Extensive plugin ecosystem for data processing
- Real-time data pipeline capabilities
Advantages and Disadvantages:
The main benefit of Logstash is its adaptability in ingesting and converting log data, which enables you to customize the data pipeline to meet certain requirements. Its combination with Kibana and Elasticsearch offers a robust stack for log analysis and visualization. Its data processing skills are enhanced by the vast ecosystem of plugins. However configuring and maintaining Logstash may be challenging, necessitating a solid grasp of its pipeline concepts. Furthermore, compared to commercial alternatives, it could take more work to set up and maintain because it is an open-source tool.
12. GrayLog
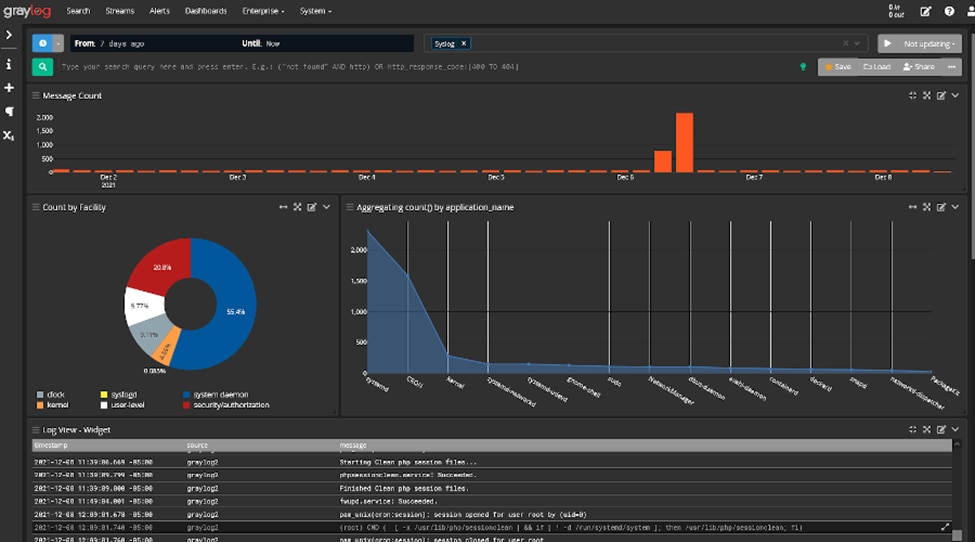
© 2024 Graylog, Inc. All rights reserved
Real-time log data collection, indexing, and analysis are possible using Graylog, an open-source log management application. Because of its strong search and analytical features, it is a well-liked option for businesses looking to extract insights from their log data.
Key Features:
- Real-time log collection and analysis
- Scalable architecture with Elasticsearch integration
- Powerful search capabilities and flexible alerting
- Customizable dashboards and visualization tools
Advantages and Disadvantages:
The main benefit of Graylog is that it’s open-source software that provides an affordable log management solution. Issues can be quickly identified because of its comprehensive search functionality and real-time log gathering and analysis capabilities. Efficient searching and scalable data storage are made possible by the integration with Elasticsearch. However setting up and configuring Graylog can be difficult, and optimizing it requires a great deal of experience. Furthermore, although the open-source version is free, there can be a fee for enterprise functionality.
13. Fluentd
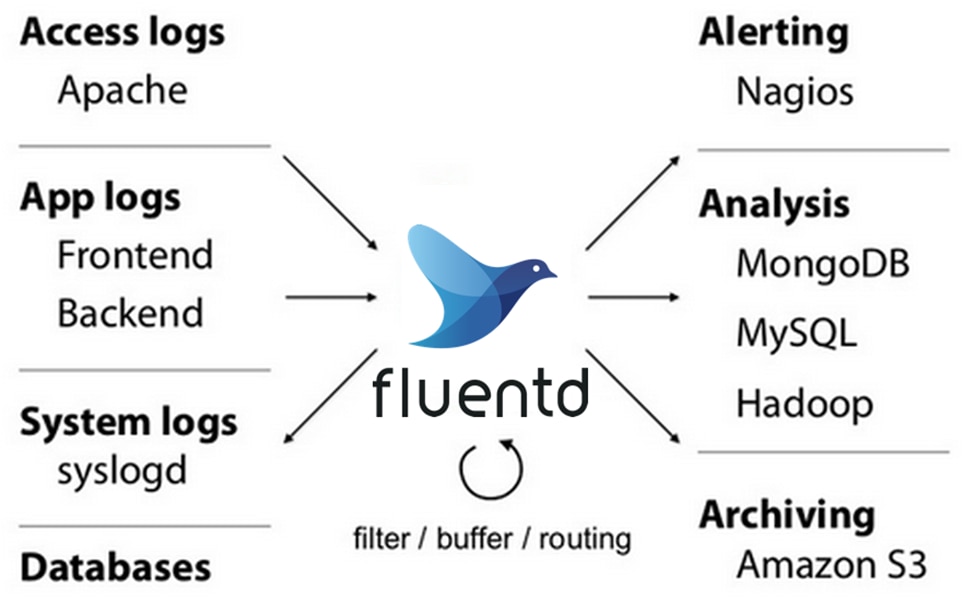
©2010-2024 Fluentd Project. ALL Rights Reserved.
An open-source data collector called Fluentd combines data gathering and consumption for improved data utilization and comprehension. Its great versatility allows it to process and alter data in real time while handling log data from multiple sources.
Key Features:
- Unified logging layer with over 500 plugins
- Real-time log data collection and processing
- Support for multiple data outputs
- High extensibility and flexibility
Advantages and Disadvantages:
The main benefit of Fluentd is its adaptability, which is backed by a sizable ecosystem of plugins that enable it to work with a variety of data sources and outputs. Its flexibility allows it to be used for a wide range of use cases, and its real-time processing capabilities allow for quick data insights. But it might be difficult to set up and configure at first, especially for those who are not familiar with its architecture. Furthermore, even though Fluentd is strong, constant upkeep and tuning can be necessary to guarantee peak performance.
14. New Relic
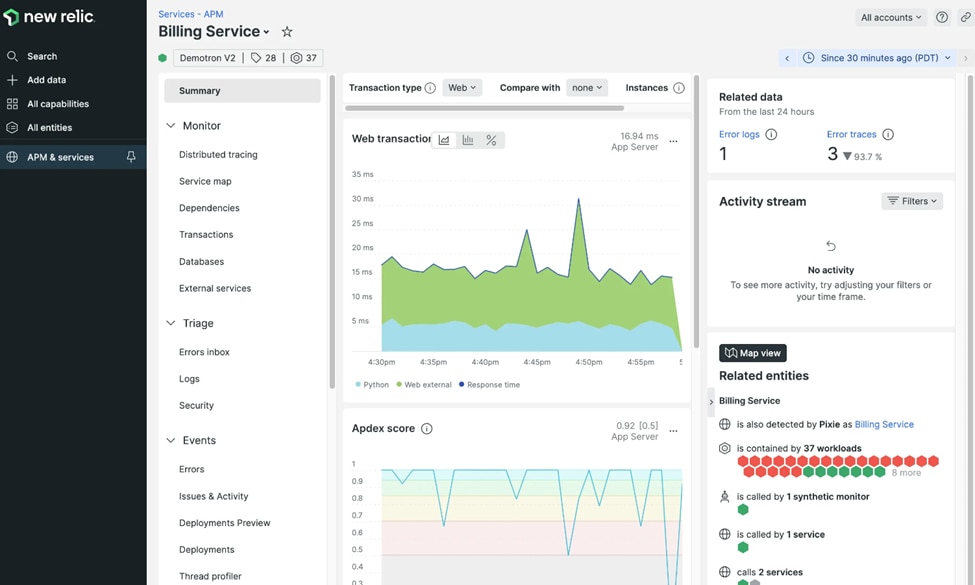
©2008-24 New Relic, Inc. All rights reserved
Log management, infrastructure monitoring, and application performance monitoring (APM) are all provided by the all-inclusive observability platform New Relic. Its various monitoring tools and log management features work together seamlessly to give users a single, comprehensive picture of the health of their infrastructure and applications.
Key Features:
- Integrated APM, infrastructure monitoring, and log management
- AI-driven insights and anomaly detection
- Advanced query capabilities with New Relic Query Language (NRQL)
- Customizable dashboards and alerting
Advantages and Disadvantages:
The main benefit of New Relic is its all-inclusive observability suite, which unifies log management, infrastructure monitoring, and APM into a single platform. Comprehensive insights into system health and performance are made possible by this integration. Its anomaly detection and AI-driven insights support proactive problem identification and resolution. Nevertheless, New Relic can be costly, especially for large-scale installations, and there might be a learning curve for its more sophisticated capabilities. Furthermore, users could find the wide range of customization choices confusing, especially if they are not well-trained.
15. ManageEngine Log360
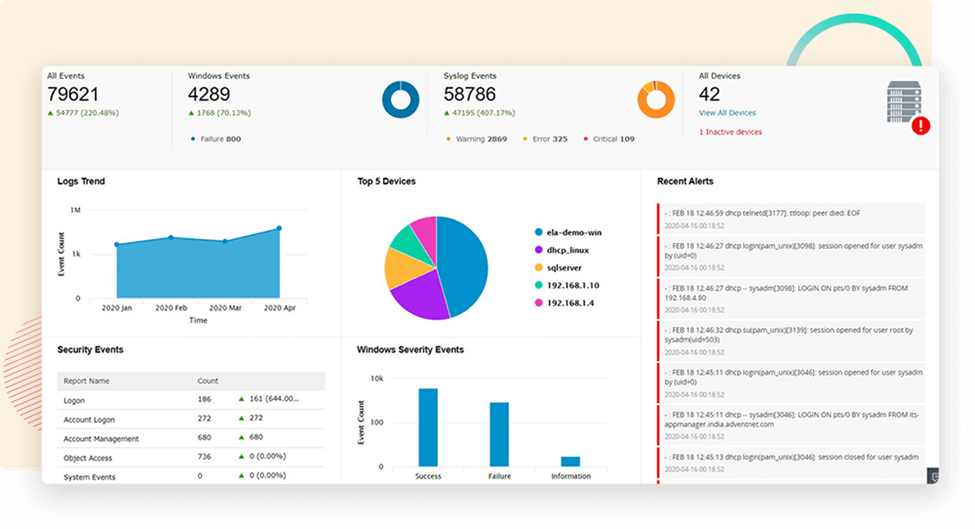
© 2024 Zoho Corporation Pvt. Ltd. All rights reserved.
A unified platform for IT security and compliance is provided by ManageEngine Log360, a complete log management and network security solution that integrates many security solutions. It offers thorough auditing as well as real-time log gathering and analysis for various network components.
Key Features:
- Centralized log collection and management
- Real-time event correlation and alerting
- Comprehensive auditing and compliance reporting
- Integration with Active Directory, Office 365, and cloud platforms
Advantages and Disadvantages:
The primary benefit of ManageEngine Log360 is its capacity to combine many technologies into a single platform, giving an integrated perspective of network security. This connection improves real-time threat detection and response capabilities while streamlining security administration. It helps comply with regulations thanks to its thorough auditing and compliance reports. It may take some time to properly comprehend and make use of all the features of the platform, though, as it can be difficult to setup and configure. Furthermore, even though it has a lot of capability, license fees can mount up, particularly for larger businesses.
16. IBM Security QRadar SIEM
© 2024 IBM
Through the gathering, normalization, and analysis of log and event data, IBM Security QRadar SIEM is a powerful security information and event management (SIEM) system that offers profound security insights. It provides sophisticated threat detection and reaction features.
Key Features:
- Advanced threat detection and anomaly detection
- Real-time event correlation and alerting
- Comprehensive compliance reporting and auditing
- Integration with various data sources and security tools
Advantages and Disadvantages:
QRadar SIEM’s primary advantage is its advanced threat detection capabilities, powered by sophisticated anomaly detection and real-time event correlation. It provides extensive integration options, allowing it to aggregate data from a wide range of sources for comprehensive security insights. The platform’s robust compliance reporting helps organizations meet regulatory standards. However, QRadar SIEM can be resource-intensive, requiring significant hardware and personnel to manage effectively. Additionally, the complexity of its setup and operation might be challenging for organizations without dedicated security teams.
17. Splunk Enterprise Security
© 2005 – 2024 Splunk Inc. All rights reserved.
Strong SIEM capabilities are offered by Splunk Enterprise Security (ES), which gives enterprises thorough insight into security data and the ability to quickly identify, look into, and address issues. It makes use of Splunk’s data analytics capabilities to provide real-time threat intelligence and actionable insights.
Key Features:
- Real-time monitoring and advanced threat detection
- Extensive data integration and normalization
- Customizable dashboards and visualizations
- Automated incident response and workflow management
Advantages and Disadvantages:
Many businesses consider Splunk ES to be the best option because of its exceptional ability to provide real-time threat detection and thorough visibility into security data. Users can customize the dashboards and robust data analytics features of the platform to suit their own requirements. The security operations workflow is streamlined by the automated incident response features. However, Splunk ES can be expensive, especially as data quantities increase, and managing the platform’s complexity may call for specialized knowledge. Furthermore, even though the many customization choices are powerful, they may be too much for inexperienced users to handle.
18. LogRhythm SIEM
© LogRhythm, Inc. All Rights Reserved.
A complete security information and event management system, LogRhythm SIEM is made to assist enterprises in promptly and efficiently identifying, addressing, and eliminating cyber threats. It combines multiple log management and security analytics features into one platform.
Key Features:
- Advanced threat detection and response
- Real-time log collection and analysis
- User and entity behavior analytics (UEBA)
- Centralized security management and incident response
Advantages and Disadvantages:
The main benefit of LogRhythm SIEM is its sophisticated threat detection and response capabilities, which are fueled by behavior analytics and real-time log analysis. This makes it possible for companies to swiftly recognize and neutralize possible threats. The platform’s comprehensive reporting tools support compliance initiatives and its unified management streamlines security operations. However, due to the system’s complexity, setup and continuing management may take a substantial amount of time and resources. Furthermore, while LogRhythm has a lot of capabilities, smaller businesses may not be able to afford it, and some users may find the learning curve to be too high.
19. Microsoft Azure Sentinel
© Microsoft 2024
A cloud-native SIEM and security orchestration automated response (SOAR) solution, Microsoft Azure Sentinel provides threat intelligence and intelligent security analytics for use throughout the company. It offers a scalable and effective security management platform by utilizing AI and the cloud.
Key Features:
- Cloud-native SIEM with integrated SOAR capabilities
- AI-driven threat detection and automated response
- Extensive integration with Microsoft and third-party services
- Real-time monitoring and analytics
Advantages and Disadvantages:
The primary benefits of Azure Sentinel are its cloud-native architecture, which guarantees scalability and flexibility, and its smooth connection with Microsoft services. The efficiency of security operations is greatly increased by AI-driven threat detection and automated response capabilities. Its analytics and real-time monitoring offer strong security insights. Organizations that rely significantly on non-Microsoft environments, however, can encounter integration difficulties. Furthermore, even though Azure Sentinel has many useful capabilities, its dependency on cloud infrastructure could raise issues with availability or latency in some use scenarios. As data ingestion rates rise, costs may also become a factor, particularly for large-scale deployments.
How to Choose the Right Log Monitoring Tool for Your Needs
Making the right log monitoring tool selection is essential to guaranteeing effective, safe, and legal IT operations. With so many options available, it’s critical to select a solution that fits the specific needs and objectives of your firm. Here’s a guide to assist you in making a wise choice:
Assessing Organizational Requirements and Goals
Start by clearly defining what you need from a log monitoring tool. Consider the specific security, compliance, and operational needs of your organization. Identify the key metrics and outcomes you aim to achieve, such as threat detection capabilities, compliance reporting, or performance monitoring.

Evaluating Tool Compatibility with Current Infrastructure
Ensure the tool you choose integrates seamlessly with your existing IT infrastructure. This includes compatibility with your servers, applications, and other monitoring systems. Assess whether the tool can handle the volume and variety of logs generated by your systems without compromising performance.
Considering Budget Constraints
The Budget is a critical factor in selecting a log monitoring tool. Evaluate the total cost of ownership, including initial purchase, subscription fees, implementation costs, and ongoing maintenance. Consider whether the tool offers scalable pricing models that can grow with your organization.
Looking into Vendor Reputation and Support
Research the reputation of the vendor offering the log monitoring tool. Look for customer reviews, case studies, and industry reports to gauge their reliability and customer satisfaction. Additionally, assess the quality of their customer support and the resources they provide for troubleshooting and guidance.
Testing Tools Through Demos and Trials
Most vendors offer demos or trial versions of their tools. Take advantage of these opportunities to test the tool’s functionality, user interface, and ease of use. Pay attention to how well it integrates with your systems and whether it meets your performance and usability expectations.
Seeking Peer Reviews and Industry Recommendations
Consult with peers, industry experts, and professional networks to gather insights and recommendations. Online forums, review sites, and industry conferences can provide valuable feedback from users with firsthand experience. These insights can help you avoid common pitfalls and select a tool that has been validated by the community.
By systematically evaluating these factors, you can choose a log monitoring tool that not only meets your immediate needs but also supports your long-term strategic objectives.
Conclusion
In this article, you’ve delved into the critical role of log monitoring tools in modern IT operations. These tools enable organizations to efficiently manage and analyze vast amounts of log data, facilitating proactive troubleshooting, security threat detection, and compliance adherence. By understanding the diverse features and functionalities offered by leading log monitoring solutions, you’re equipped to enhance operational efficiency, mitigate risks, and ensure regulatory compliance within your organization’s IT infrastructure.
SolarWinds’ Security Event Manager stands out as a premier solution in the realm of log monitoring and event logging. Its robust capabilities in real-time threat detection, compliance reporting, and centralized log management make it an indispensable tool for organizations prioritizing security and operational visibility.
Alongside Security Event Manager, SolarWinds offers a suite of complementary tools like Papertrail, Loggly, and AppOptics, each addressing specific aspects of log management with precision and scalability. Whether you choose Security Event Manager or explore other offerings from SolarWinds, you’re assured of comprehensive log monitoring solutions that meet the diverse needs of modern IT environments. It’s worth taking advantage of the 30-day trial period to test this tool before you buy!


