It’s no question that bottlenecks, downtime, and other common network performance issues can vastly affect the end-user experience and put productivity on hold, ultimately cutting into your company’s bottom line. Getting to the root cause of performance problems is a top priority for nearly every sysadmin. This is where packet sniffers, also known as network sniffers or network analyzers, come into play. With the right packet sniffer, you’ll be well-equipped to capture and analyze network traffic, helping you identify the cause of network performance problems and prevent them from recurring.
What Are Packet Sniffers?
How Do Packet Sniffers Work?
The Benefits of Packet Sniffing
Packet Sniffing Best Practices
A Word of Warning — How Hackers Use Packet Sniffers
Types of Packet Sniffing Tools
10 Best Packet Sniffers
- SolarWinds Network Performance Monitor (My personal favorite tool)
- Paessler PRTG Network Monitor
- ManageEngine NetFlow Analyzer
- Savvius Omnipeek
- tcpdump
- WinDump
- Wireshark
- Telerik Fiddler
- NETRESEC NetworkMiner
- Colasoft Capsa
What Are Packet Sniffers?
A packet sniffer is either a software or hardware tool to intercept, log, and analyze network traffic and data. These tools aid in the identification, classification, and troubleshooting of network traffic by application type, source, and destination. There are a variety of tools on the market, most of which rely on application program interfaces (APIs) known as pcap (for Unix-like systems) or libcap (for Windows systems) to capture network traffic. The best packet sniffers then analyze this data, enabling you to both pinpoint the source of an issue and prevent it from happening in the future.
My personal favorite is the SolarWinds Network Performance Monitor. This comprehensive software offers in-depth packet sniffing capabilities as well as a host of other cutting-edge resources at a reasonable price point.
To truly understand the power of packet sniffers, it’s important to establish a sound knowledge base of internet routing. Let’s start at the beginning. Every email you send, webpage you open, and file you share is distributed across the internet as thousands of small, manageable chunks known as data packets. These packets are transmitted through a protocol stack known as the Transmission Control Protocol/Internet Protocol (TCP/IP). The TCP/IP is broken into four layers: the application protocol layer, transmission control protocol (TCP) layer, internet protocol (IP) layer, and hardware layer.
Each packet moves through your network’s application layer to the TCP layer, where it’s assigned a port number. Next, the packet migrates to the IP layer and receives its destination IP address. Once a packet has a port number and IP address, it can be sent over the internet. Sending is carried out through the hardware layer, which converts packet data into network signals. When a packet arrives at its destination, the data used to route the packet (port number, IP address, etc.) is removed, and the packet moves on through the new network’s protocol stack. Once it reaches the top, it’s reassembled into its original form.
How Do Packet Sniffers Work?
Packet sniffers work by intercepting traffic data as it passes over the wired or wireless network and copying it to a file. This is known as packet capture. While computers are generally designed to ignore the hubbub of traffic activity from other computers, packet sniffers reverse this. When you install packet sniffing software, the network interface card (NIC)—the interface between your computer and the network—must be set to promiscuous mode. This commands the computer to capture and process, via the packet sniffer, everything that enters the network.
What can be captured depends on the network type. For wired networks, the configuration of network switches, which are responsible for centralizing communications from multiple connected devices, determines whether the network sniffer can see traffic on the entire network or only a portion of it. For wireless networks, packet capture tools can usually only capture one channel at a time unless the host computer has multiple wireless interfaces.
The Benefits of Packet Sniffing
So, what’s the point of packet analyzers, and why should you want to IP sniff? A packet sniffer can help you target new resources when expanding your network capacity, manage your bandwidth, increase efficiencies, ensure delivery of business services, enhance security, and improve end-user experience. Here’s how.
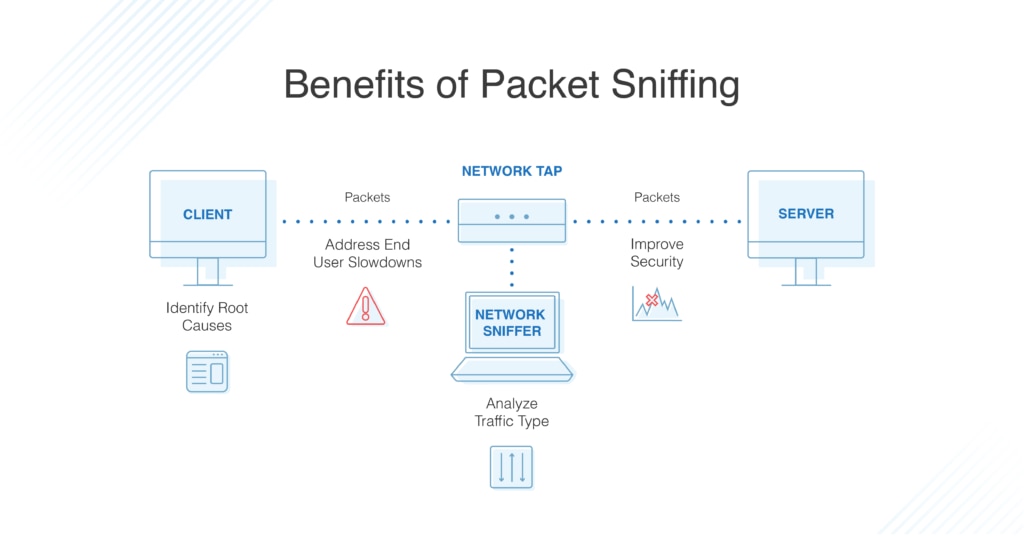
- Identify the Root Cause. For companies large and small, daily tasks can instantly be derailed by performance issues related to the network, an application, or both. To get their company back up and running, sysadmins must be able to quickly determine the root cause. Because packet sniffers view and gather information for all the traffic across the network, they can evaluate critical network pathways to help admins determine whether the application or the network is the cause of poor user experience. With this information in hand, admins are better equipped to pinpoint—and resolve—the origin of an issue.
- Dig Deep into Slowdowns. When users report slowness, admins can use PCAP analysis to measure the network response time—also known as network path latency—and determine the amount of time required for a packet to travel across a network path from sender to receiver. This enables admins to quickly determine the cause of slowdowns and identify affected applications, so they can take action.
- Analyze Traffic by Type. When evaluating network and application performance issues, having a firm grasp of the traffic on your network is paramount. With the right IP sniffer and packet analyzer, traffic is categorized into types based on destination server IP addresses, ports used, and measurement of the total and relative volumes of traffic for each type. This empowers you to identify excessive levels of non-business traffic (such as social media and external web surfing) that may need to be filtered or otherwise eliminated. You can also identify traffic flowing over a network link as well as traffic to specific servers or applications for capacity management purposes.
- Improve Bandwidth. When users complain “the network is slow,” or “the internet is down,” productivity grinds to a halt, reducing ROI and jeopardizing business growth. To get back on track, you need to understand how your network bandwidth is being used and by whom. A Wi-Fi packet sniffer can retrieve performance metrics for autonomous access points, wireless controllers, and clients. Many also offer fault, performance, and network availability monitoring, cross-stack network data correlation, hop-by-hop network path analysis, and much more, to help you detect potential issues and minimize network downtime.
- Improve Security. A high volume of outbound traffic could indicate a hacker is using your applications, either to communicate externally or to transfer a large amount of data. A packet sniffer can highlight unusual spikes in traffic so you can dig deeper to determine whether a cybercriminal is at work.
10 Best Packet Sniffers List >>>
Packet Sniffing Best Practices
With your packet sniffer in hand and your NIC set to promiscuous mode, you’ll be off and running with packet capture. But while many of the benefits of packet sniffing will fall into place, there are certain best practices to follow if you want to reap the full results and protect your company from security violations. To get the most out of your packet sniffer, ensure you:
- Know the Basics. To analyze network traffic, you must understand how networking works. Yes, some packet sniffers will break data down and offer dashboards full of insight, but knowing about the types of network traffic on a healthy network, such as the Address Resolution Protocol (ARP), for communication, and the Dynamic Host Configuration Protocol (DHCP), for network management, is key. You need to know what you want the packet sniffer to collect and have at least a general idea of what’s normal and what’s not. With a base-level understanding of network traffic, you can help ensure you’re evaluating the right mass of packets. Equip yourself with the foundational principles and you’ll be set for success.
- Copy Conservatively. Each packet contains a header identifying its source and destination as well as a payload—the term used to describe the contents of the packet. A basic packet sniffer will copy the payload and headers of all packets traveling on the network. If the packet payload isn’t encrypted, members of your IT team can access sensitive business data, opening the doors to a plethora of potential security risks. To help you protect your company and avoid putting sensitive information in jeopardy, many packet sniffers can be set to copy only the header information. Most of the time, this is the only information you’ll need to perform network performance analysis.
- Monitor Storage Space. Even if you’re only capturing packet headers, storing every packet can consume a large amount of your disk space. If you want to glean an understanding of network usage over a set period, say a few days, it’s best to copy every tenth or twentieth packet rather than copying every single one. This is known as packet sampling, and it’s a practice widely used to characterize network traffic. Packet sampling works by leveraging randomness in the sampling process to prevent synchronization with any periodic patterns in the traffic. While this method of network characterization is not 100% accurate, it’s a solution with quantifiable accuracy.
- Decode the Data. Some of the network data gathered by a packet sniffer will be encoded. To glean the full benefits of the data capture process, choose a packet sniffer able to decode this administrative information as well as extract other valuable insights, such as the varying port numbers between which the packets travel. This information will help you generate a more robust analysis of your network traffic.
A Word of Warning — How Hackers Use Packet Sniffers
While sniffer software is a tremendous asset to any IT team when implemented correctly, it can also be used by hackers to collect passwords, eavesdrop on unencrypted data within the packets, and steal data in transit. Hackers also use packet sniffers to conduct man-in-the-middle attacks, in which data is altered and diverted in transit to defraud a user. The malicious use of packet sniffers can lead to security breaches, industrial espionage, and more.
To protect your business from unlawful packet sniffing, it’s critical to always use HTTPS (SSL encrypted sessions) when entering and sending form data. Never rely on HTTP; it’s not secure and it puts your personal, sensitive information, like login credentials, in jeopardy. If you or someone in your business is using a website with HTTP, see if it will accept an HTTPS connection by typing “https://” into the browser bar before the site address. Oftentimes, a website has an SSL certificate in place but doesn’t require visitors to use it.
Alternatively, you can opt to skip this extra step and implement the Electronic Frontier Foundation browser add-on, known as HTTPS Everywhere, for Chrome, Firefox, and Opera. This add-on is designed to automatically connect every website you visit using HTTPS.
Compared to other security measures, VPNs, virtual private networks, offer the most protection because they encrypt your traffic. You can also protect the metadata of your packets, such as destination addresses, by ensuring your DNS queries go through the VPN. Nevertheless, while VPNs are a security must-have, you should continue to use HTTPS even when a VPN is in place.
Many sysadmins also choose to invest in intrusion detection systems, which monitor network traffic for unusual spikes in traffic—a telltale sign of an intruder. Another option is to leverage tools like AntiSniff, which detect when a network interface has been put into promiscuous mode, raising a red flag if this occurred without your knowledge.
Types of Packet Sniffing Tools
There are countless packet sniffers on the market today, both paid and free. And while each tool is built on the core tenets of network traffic collection, they vary greatly in their breadth and depth. Many open-source tools are starkly simple in their design, and that’s the point: these tools have been built to offer reliable, clean data collection while leaving as small a footprint as possible. If you’re in need of some simple sniffing and quick diagnostics, a free, open source tool may serve the purpose. Many—although not all—free versions can be upgraded to provide additional analytical features if you determine greater support is needed.
With so many products on the market, it can be hard to know which packet sniffer to choose. While free options abound, putting some money behind your packet sniffer can ensure you’re armed with a tool that not only captures data but also offers intuitive analysis. Going beyond your basic packet sniffers, of which there are dozens, you’ll find the more robust analytic packet capture and network sniffing tools. In many cases, what sets these tools apart is their ability to perform deep packet inspection (DPI).
DPI software relies on sensors installed on transaction servers and a network sensor attached to a test access point (TAP) or mirror port. The software gathers data about the response time in interactions between clients and servers for both connectivity-level and application-level transactions. This metadata empowers admins to regulate traffic flows and differentiate between network issues and application issues to determine the cause of bottlenecks, slowdowns, and downtime.
These large enterprise-level tools are often equipped to alert on exception cases and to produce intuitive graphs and charts displaying detailed metrics. While they come at a price, they’re well worth the investment.
10 Best Packet Sniffers
1. SolarWinds Network Performance Monitor (Free Trial)
While there are plenty of free options out there, none offer the wide range of features, scalability, and ease of use you’ll get with SolarWinds Network Performance Monitor (NPM) and accompanying packet sniffer. This multi-layered tool provides a comprehensive view of your network, so you can quickly detect, diagnose, and resolve network performance issues and avoid downtime. Plus, the system uses minimal bandwidth, requiring low overhead on Orion® Platform servers and nodes.
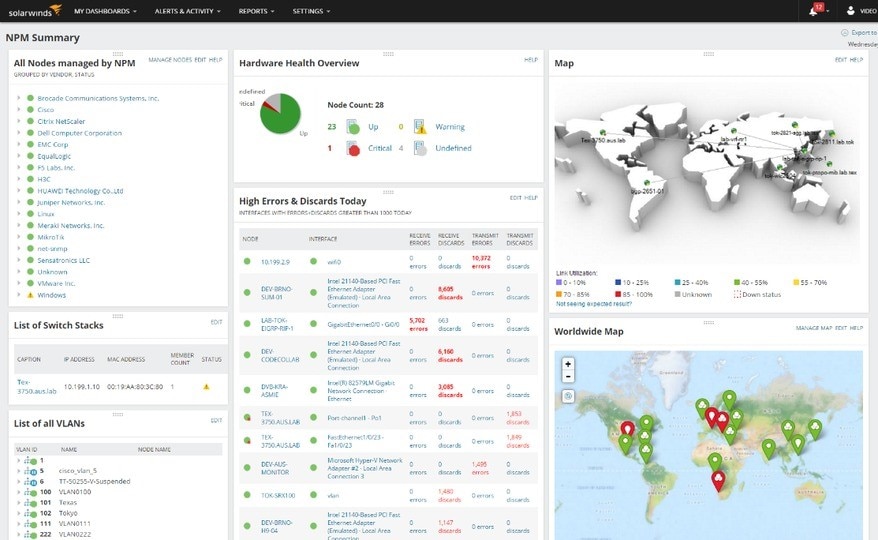
NPM leverages DPI to capture packet-level data across your network by accessing managed Windows devices and drawing on installed sensors. Within NPM’s Quality of Experience module, you can use the step-by-step “wizard” to deploy sensors and select pre-configured or custom applications to monitor.
With probes installed on network devices, SolarWinds NPM can view and gather metadata for all the traffic across the network. The diagnostic tool then registers and displays information like response times, data volume, and transactions to locate slowdowns and flag any issues. These DPI insights guide you in determining whether the application or the network is the cause of poor user experience and create a hop-by-hop packet path map for you to view bottleneck locations at a glance.
In addition, through the tool’s bandwidth analyzer feature, you can glean an understanding of how your network bandwidth is being used and by whom. NPM leverages
- NetFlow
- JFlow
- sFlow
- NetStream
- IPFIX
data built into most routers to identify the users, applications, and protocols consuming your bandwidth. This empowers you with the information you need to shut down bandwidth-hogging users and apps before putting extra spend behind more bandwidth. You can also use NPM as a wireless sniffer, taking advantage of Wi-Fi packet capture capabilities featuring performance, traffic, and configuration details for devices and apps on-premises, in the cloud, or across hybrid environments.
But that’s not all. NPM boasts a web-based performance dashboard with dynamic charts and graphs categorizing both real-time insights and historical data. Within this intuitive dashboard, you can accelerate root cause identification by dragging and dropping network performance metrics on a common timeline for immediate visual correlation across all your network data.
The tool also offers customizable, intelligent alerts to make it easy to stay abreast of network device health, performance issues, and suspicious spikes in traffic activity. With this level of alerts, you can quickly act if something appears amiss, helping to prevent a security breach and keep hackers at bay.
To find out if NPM is the right network sniffer tool for you, download the free, fully functional 30-day trial.
2. Paessler PRTG Network Monitor
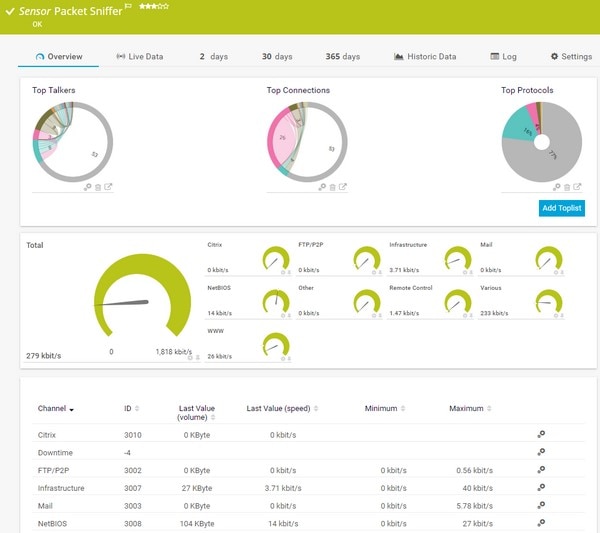
The PRTG Network Monitor from Paessler includes an impressive array of packet capture capabilities. The software relies on four core sensors in your network to sniff IP packets. Each sensor has its own unique capabilities. The packet sniffing sensor is designed to help sysadmins monitor an array of traffic, including web, mail, file transfer, infrastructure, and remote control traffic. It only analyzes packet headers, not packet payloads, so it places less strain on your system and helps safeguard sensitive information. The sFlow sensors are designed to place even less strain on your system: they analyze every nth packet, making them suited for large networks. The NetFlow and JFlow sensors, meanwhile, are designed specifically for monitoring data traffic and packets from Cisco devices and Juniper devices, respectively.
Beyond the scope of those four sensors, PRTG enables customizable NetFlow, IPFIX, JFlow, and sFlow sensors to serve as individual channels or to monitor the specific data traffic you wish to analyze. PRTG also boasts a list of more than 200 sensors to help ensure you’re capturing the exact data traffic you need, thus pinpointing and resolving your issues more quickly. All the data PRTG captures can be viewed in the software’s dashboard, which neatly displays all key facts and figures, helping you quickly identify anomalies, such as an unusual increase in protocols or traffic type.
PRTG is free for up to 100 sensors. Because each device requires approximately five to ten sensors, larger companies will need to put a little spend behind this robust platform.
3. ManageEngine NetFlow Analyzer
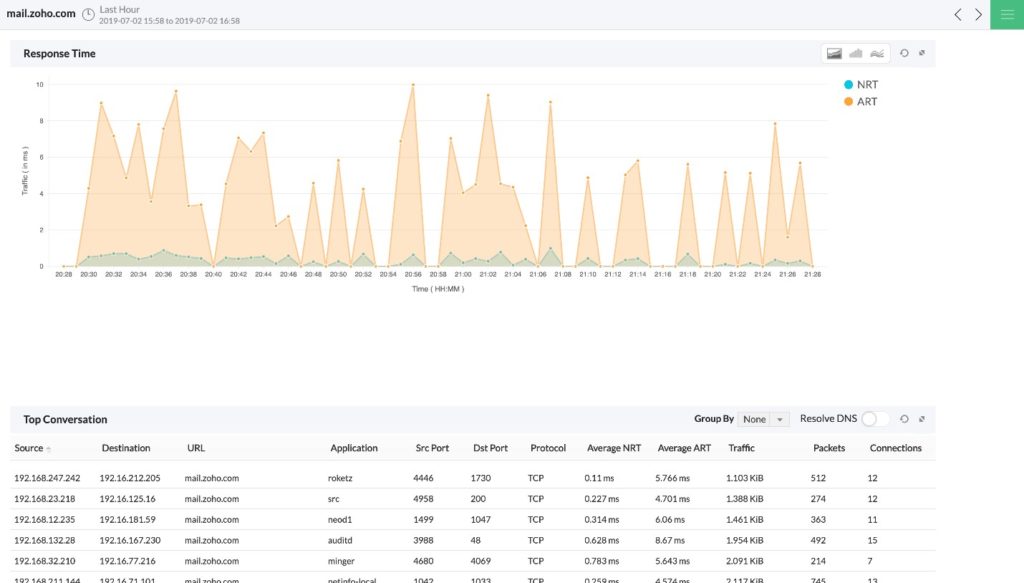
ManageEngine offers a packet sniffer within its NetFlow Analyzer tool, which can be installed on Windows and Linux. NetFlow Analyzer is a complete traffic analysis software leveraging flow technologies to provide your team with in-depth insights into network bandwidth performance and traffic patterns. The software uses a DPI add-on to determine whether the network or the application lies at the root of issues, enabling you to put an end to performance problems before they drastically affect end-user experience. If a problem will affect a group of end-users, NetFlow Analyzer allows you to pull the list of affected users so that you can inform them that a solution is in motion.
To take DPI analysis a step further, NetFlow Analyzer provides a Response Time Dashboard featuring graphs for traffic volumes based on top applications, providing the details you need to troubleshoot bandwidth issues at a glance. Once you identify the application and/or user straining your bandwidth, NetFlow Analyzer provides regulation capabilities in the form of traffic shaping (also known as packet shaping). Traffic shaping is a bandwidth management technique to delay the flow of certain types of network packets to ensure network performance for higher-priority applications.
NetFlow Analyzer also offers some reporting features. With the conversation report function, sysadmins can drill down to better understand the conversation between top users and applications, thereby helping prevent future issues. Along those lines, the historical report function assists in spotting trends and recurring issues so you can take steps to prevent them from happening yet again.
There are two versions of NetFlow Analyzer: the Essential edition and the Enterprise edition. However, DPI is considered an add-on for both.
4. Savvius Omnipeek
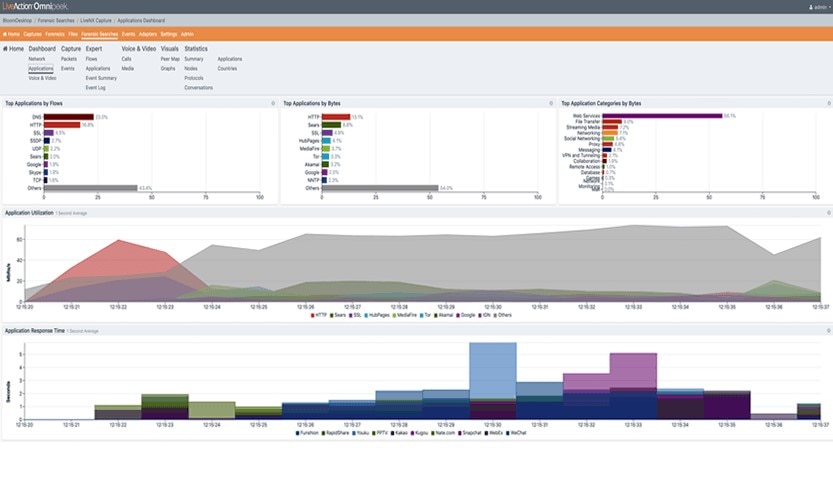
Omnipeek by Savvius is designed for larger networks with a vast amount of data running through them every second. At its core, it’s a performance, analytics, and forensics tool providing the basics as well as in-depth analysis. Omnipeek can decode over 1,000 protocols for real-time analysis. The software’s intuitive graphic displays and visualization make it easy to drill down, compare, and look across network traffic to identify performance issues. Omnipeek even suggests the most likely root cause of a network problem, further facilitating the troubleshooting process.
In addition, this packet sniffer tool offers remote access for sysadmins, allowing them to troubleshoot from afar, as well as wireless packet capture capabilities and advanced IP sniffing through voice and video monitoring. An alert system is also part of the package, so you can generate automated notifications based on expert views or when pre-determined network policies are violated.
Omnipeek is available in three versions: Connect, which is limited to distributed analysis; Professional, for small to midsize businesses; and Enterprise, for large organizations.
5. tcpdump
Many sysadmins know tcpdump as the original packet sniffer. While it has evolved slightly since its launch in 1987, it remains largely unchanged. An open-source tool, tcpdump comes installed on nearly all Unix-like operating systems and is a go-to for packet capture on the fly. Because it’s a command-line tool, it doesn’t require a heavy-duty desktop to run, making it a favorite among sysadmins.
tcpdump captures all traffic on the specified network via libcap and then “dumps” it directly to your screen. From there, you can leverage the tool’s complex filtering language to winnow the vast amount of data collected into manageable chunks. A myriad of filters can be applied to accomplish this; you just need to know the right commands. Most sysadmins use commands to segment the data, then copy it to a file exported to a third-party tool for analysis. This is due, in large part, to the fact that tcpdump can’t read the pcap files it captures.
The rudimentary nature of tcpdump combined with its complex commands and highly technical language leads to a rather steep learning curve. Nevertheless, tcpdump is a powerful tool for identifying the cause of network issues once it has been mastered. To give it a try, type “tcpdump” into your search bar to see if it’s already installed on your device.
6. WinDump
Due to the success of tcpdump on Unix-like operating systems, it was “ported over” to the Windows platform. This simply means it was cloned to allow for Windows packet capture. Like tcpdump, WinDump is a command-line tool, and its output can be saved to a file for deeper analysis by a third-party tool. WinDump is used in much the same way as tcpdump in nearly every aspect. In fact, the command-line options are the same, and the results tend to be pretty much identical.
Along with the striking similarities between the two, there are a few distinct differences. Unlike tcpdump, which is built into an operating system, WinDump must be downloaded; it’s delivered as an executable file and requires no installation. For WinDump to run, the WinPcap library (the Windows version of the libpcap library used by tcpdump) must be installed. However, WinDump doesn’t have to be installed on every single one of your machines—you can simply copy it over as needed.
7. Wireshark
Like tcpdump and WinDump, Wireshark has been around for a few decades and helped set the standard for network protocol analysis. Wireshark is a completely free, open-source tool that has been ported over to nearly all network operating systems, including Windows, Linux, macOS, Solaris, FreeBSD, and NetBSD. To this day, Wireshark remains a volunteer-run organization backed by several significant sponsorships.
The Wireshark packet sniffing tool is known for both its data capture and its analysis capabilities. You can apply filters to limit the scope of data Wireshark collects, or simply let it collect all traffic passing through your selected network. Importantly, it can only collect data on a server with a desktop installed. Since desktops aren’t common on servers, many sysadmins choose to use tcpdump or WinDump to capture traffic to a file, which they then load into Wireshark for in-depth analysis.
Whether or not you use Wireshark for data capture, you can still leverage its dynamic set of filters to home in on the exact set of information you’re interested in. One filter feature that distinguishes Wireshark from the pack is its ability to follow a stream of data. For example, if you want to view only the Google IP address, you can right-click and select “Follow” and then “TCP Stream” to view the entire conversation. In addition to its filtration capabilities, Wireshark is widely respected for its rich VoIP analysis, gzip decompression, live data readings from Ethernet sniffing, and decryption support for a variety of protocols, including IPsec, WPA and WPA2, and SNMPv3. Nevertheless, the learning curve for Wireshark is steep, as it’s not as intuitive as other packet sniffers.
8. Telerik Fiddler
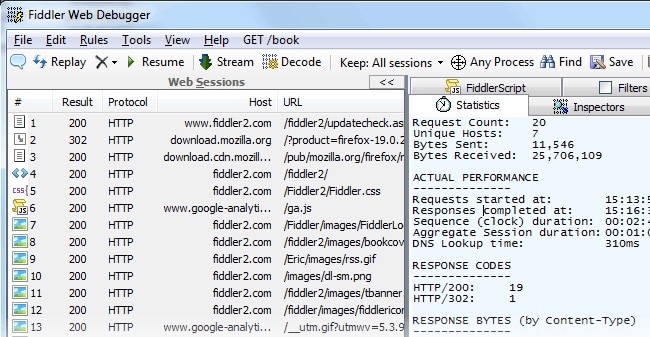
While Telerik Fiddler technically isn’t a packet sniffer or network analyzer, it is a useful http sniffer known for its desktop debugging capabilities. Unlike other tools and browser functions, Fiddler captures both browser traffic and any HTTP traffic on the desktop, including traffic from non-web applications. This is key due to the sheer volume of desktop applications using HTTP to connect to web services.
While tools like tcpdump and Wireshark can capture this type of traffic, they can only do so at the packet level. To analyze this information with tcpdump or Wireshark would require the reconstruction of those packets into HTTP streams, a time-consuming endeavor. Fiddler makes web sniffing easy and can help discover cookies, certificates, and payload data coming in or out of applications. You can even use the tool for performance testing to improve the end-user experience. Simply leverage Fiddler’s API response analysis and you’ll be able to determine which part of the response contains a bottleneck, allowing you to quickly diffuse the issue.
Fiddler is a free tool designed for Windows. However, beta builds for OS X and Linux (using the Mono framework) can be downloaded.
9. NETRESEC NetworkMiner
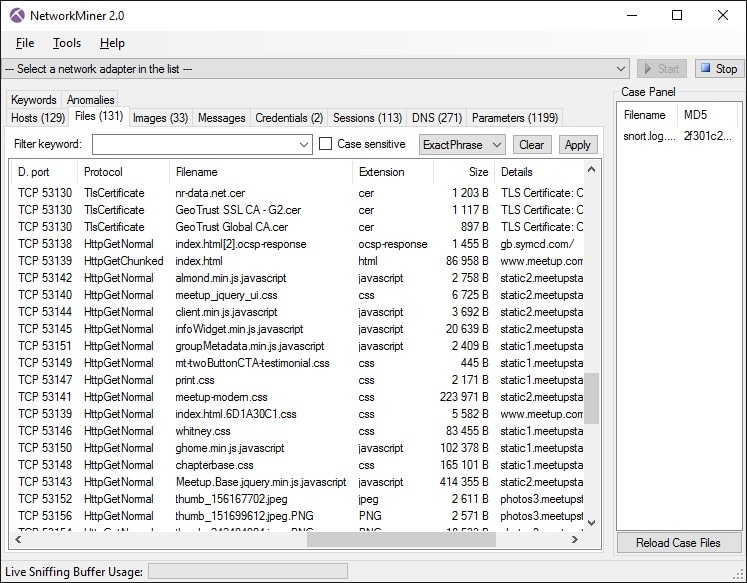
NETRESEC NetworkMiner is an open-source network forensic analysis tool (NFAT) that can be leveraged as a network sniffer and packet capture tool to detect operating systems, sessions, hostnames, open ports, and so on, without putting any of its own traffic on the network. Like Wireshark, NetworkMiner can follow a specified TCP stream and reconstruct files sent over the network, giving you access to an entire conversation. This software can also work in offline mode, parsing pcap files for offline analysis and regenerating/reassembling transmitted files and certificates from pcap files. Simply use tcpdump to capture the packets of your choosing and import the files into NetworkMiner for analysis.
NetworkMiner was designed for Windows, but it can be run on any operating system with a Mono framework. While a free version is available, a professional license is required to use the tool’s more advanced features, including IP-based geolocation, custom scripting, and the ability to decode and play back VoIP calls.
10. Colasoft Capsa
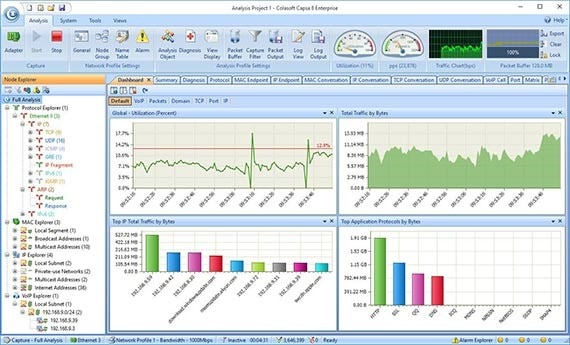
Capsa, developed by Colasoft, is a Windows packet capture tool boasting free, standard, and enterprise editions. The free version is designed for Ethernet sniffing and can monitor 10 IP addresses and approximately 300 protocols. While the free version is fairly limited in scope, it offers some graphical analysis of the network traffic it captures and can even be used to set alerts. It’s best suited for those who want to dip their toes into network monitoring and learn how to pinpoint network problems and enhance network security.
Capsa Standard is designed with small and budget-strapped teams in mind. It helps sysadmins troubleshoot network problems by monitoring traffic transmitted over a local host and a local network. Capsa Standard provides advanced network protocol analysis of more than 1,000 protocols and network applications and can monitor 50 IP addresses. Through the platform’s in-depth packet decoding, all network traffic collected is displayed in hex, ASCII, and EBCDIC. You can also view real-time data as well as perform historical analysis to help stop a performance problem in its tracks and prevent recurring issues from disrupting the end-user experience.
The most robust of the bunch is Capsa Enterprise, which, despite its name, is suited for small and large businesses alike. Capsa Enterprise performs network monitoring, troubleshooting, and analysis for both wired and wireless networks, making it a comprehensive option for identifying and diagnosing network issues. It can monitor an unlimited number of IP addresses and identify and analyze 1,500 protocols and sub-protocols, including VoIP, as well as network applications based on the protocol analysis. But what truly makes the Enterprise edition stand out is its user-friendly dashboard and the extensive statistics it provides for each host and its accompanying traffic.
The Takeaway
While packet sniffing products abound, finding the best fit for your company comes down to your own skill level and needs. My preferred packet sniffing software is Network Performance Monitor. This comprehensive tool offers in-depth network sniffing capabilities as well as a myriad of other features to help you quickly and efficiently identify the cause of bottlenecks, downtime, and more, all at a reasonable price point. Whether you’re an IT veteran working for a major corporation or a new sysadmin at a small organization, SolarWinds NPM can be tailored to fit your unique needs.
Related Articles
6 Best FREE Patch Management Software
Whether you’re a small nonprofit or a major corporation, patch management must be incorporated into your IT team’s strategy to repair vulnerabilities that, if left unattended, can allow attackers to strike and put your entire system in jeopardy. Here’s my list of the best free options on the market.
Best IT Asset Management Software
Your company relies on hundreds of printers, computers, phones, software, and more to operate successfully on a day-to-day basis. Managing the health, inventory, and contractual agreements associated with each of these devices is no easy task. Here’s my list of the best IT asset management software, designed to help you consolidate your assets, remain compliant, and boost security.


