While they don’t sound particularly glamorous, patch management processes are vitally important for system security, and can make a big difference to whether you’re vulnerable to malicious attackers or not.
One of the most important things to keep in mind is patch management should not just be performed when you remember, or when you hear a critical security issue has come up. Rather, patch management should be a continuous and well-established process carried out in some way at all times. Enterprise patch management best practices need to be followed to the letter, with particularly comprehensive policies and approaches, as enterprises store and manage huge amounts of proprietary and individual private information, as well as data such as credit card details.
Feel free to jump ahead to the description of each patch management best practices:
- Making an inventory
- Categorizing your systems
- Quickly patching processes
- Deploying to a test environment
- Regular patching
- Scanning and auditing for vulnerabilities
- Automation
- Reporting
Windows 10 and Windows Server operating systems were all recently hurriedly patched after a critical and urgent security flaw was discovered by the National Security Agency (NSA). This flaw allowed secure certificates to be spoofed for web sessions, which meant malicious websites could effectively be disguised as safe ones. The NSA noted “rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.” This highlights the importance of using good patch management tools, such as SolarWinds® Patch Manager, in tandem with best practices, as it could be the difference between a critical security flaw and a secure system.
Factors Increasing Patch Management Complexity
There are several factors contributing to the increasing complexity of patch management.
- Automation. Increasing software orchestration means many computer systems and processes have become automated, including their configurations and management. This makes life easier for IT teams, and for the most part increases security and keeps systems performing at a much higher level than when manual monitoring and management takes place. However, this also means the software you use to manage all the other software needs to be high-quality.
The key thing to understand about orchestration is these processes are designed with a business goal in mind, not simply automation. So, the process needs to align with business needs and aims. This complicates the role of patch management—a critical yet potentially intrusive process, as applying an urgent patch could mean interrupting service uptime. - Containers. Virtual machines and cloud services are used more and more as part of enterprise IT infrastructure, and in many cases, applications are run inside containers. Containers facilitate the movement of software or applications from one device or environment to another. This is similar to the use of a virtual machine; however, containers have much larger functionality. This makes them more useful in many cases, but also means their attack surface is increased. As a result, having patches to work effectively with container-based systems and applications is vital.
- External Devices. Businesses are becoming more likely to have mobile devices as part of their network and infrastructure, and most of the time employees bring their personal devices to work and connect to work networks. Having security processes in place for external devices is important, as these devices can bring malicious software onto the network easily and without foresight from the offending employee. Patching software should be able to handle new devices coming onto and the network, and to determine whether they’re carrying any applications with vulnerabilities needing to be tackled.
8 Patch Management Best Practices
The exact patch management processes you follow will depend on the industry, as each separate practice area has patch management best practices. NIST guidelines, for example, outline the approach large organizations should take to fixing software flaws and patch management, in a way complying with the Federal Information Security Management Act (commonly known as FISMA).
In addition, you need to look at whether any particular frameworks should inform your patch management best practices. ITIL includes patch management as part of release management, for example, which constitutes one of the 17 ITIL service management practices.
I’ve compiled the following patch management checklist to help you make sure you’ve covered all your bases and are protecting your enterprise IT infrastructure in a responsible way. If you are following an ITIL framework, you should be using these patch management best practices:
- First, make a thorough inventory of the devices, services, and dependencies creating your IT infrastructure.
This inventory should include what operating systems you’re using and which versions, and native and third-party applications. You should also be aware of what security systems you have in place, such as firewalls and anti-malware programs, including their configuration and latest version. When you have a clear inventory of what’s in your IT environment, you can make sure your patch management approaches are covering everything needing to be protected.
- Categorize your systems.
To apply effective patch management processes, you need to have performed a clear risk assessment to ensure the highest-risk or most sensitive parts of your infrastructure are patched first. Having a more refined policy instead of a one-size-fits-all approach means you won’t be applying low-priority patches during the middle of the work day or failing to apply a critical patch when it’s necessary.
- It’s essential any patches be applied as soon as practically possible.
The exact time frame will vary depending on how critical the application or service is, how severe the vulnerability is, and how much time it takes to test and deploy the patch itself. In all cases, patches to your operating system should be deployed immediately when they’re released, as operating system vulnerabilities can have serious and wide-reaching effects.
- All patches should be deployed to a test environment before you deploy them to the entire system.
It’s possible to roll back patch deployments, but in the meantime a bad patch can break other parts of your system or even expose new vulnerabilities.
- For non-critical patches, a regular timeline should be established in which the patches are deployed, to minimize disruption to the business.
When a patch is deployed, this can slow down your business and network performance, so maintenance is best performed with automated systems during the lunch hour or overnight. Make sure you have an alerting system set up for patches deployed when you aren’t there, so if any part of the patch fails or any issue arises, you’ll be notified.
- Regularly scan and audit your systems for any vulnerabilities missed the first time around.
The longer these security holes stay open, the more likely it is you’ll be the subject of an attack. Patch management should be a continuous process with regular and ongoing scanning.
- Use an automated tool or piece of software for the patch management process.
Using software to manage and maintain your patches and updates can take a huge workload off your shoulders, and in many cases will be much more accurate and effective than trying to do things manually. My top choice of patch management tool is SolarWinds Patch Manager.
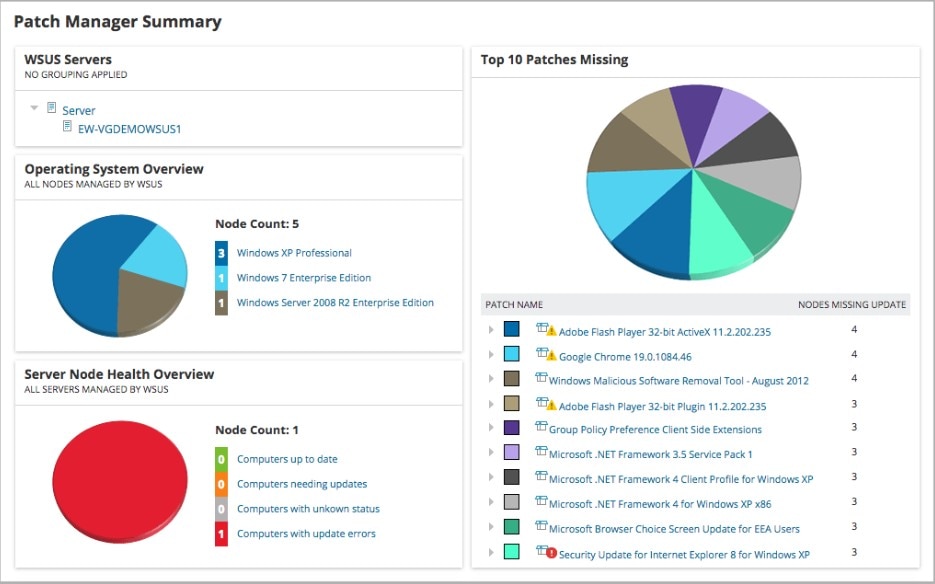
Patch Manager has several features making it an excellent choice for maintaining your patch management processes. First, it works with Microsoft WSUS and SCCM, as well as third-party applications, to enhance your Windows patching tools. Second, it includes pre-built and tested patches for third-party applications, so you don’t need to spend as much time creating and testing these patches yourself. The Patch Manager dashboard is also excellent, as it displays the patch status of your entire environment. You can also see the top 10 missing patches, so you can focus on patching the most vulnerable parts of your software first.
- Undertake reporting and regular reviews to ensure your patch management processes and software are all working as expected.
SolarWinds Patch Manager includes a utility capable of creating reports from your patch history, whether to demonstrate compliance with any legal or regulatory standards, or simply to show auditors or internal management you’re on top of security measures.
Key Takeaways
Patch management is a field constantly evolving, as malicious attackers become increasingly sophisticated. Most businesses use large numbers of applications, different operating systems, and cloud-based storage, services, or infrastructure, which means more surface area available to attack. As a result, having good patch management processes are vital, as they may make the difference between your services operating as planned and a massive shutdown or data breach.
You should also consider leveraging a tool like SolarWinds Patch Manager as an automated patch management solution to help simplify your current patching processes. You can even try the tool risk-free for 30 days by downloading a free trial.


