Distributed denial-of-service (DDoS) attacks are increasingly becoming a problem for global companies that have a significant portion of their business online. Knowing how to stop a DDoS attack is vitally important, especially considering that it can cost a business significantly in lost revenue. This might mean employing protection tools — my personal pick is Security Event Monitor.
What Is a DDoS Attack?
A DDoS attack uses a tool, like a bot, that floods the network with signals over and over again, which eventually causes the network to stop being able to process genuine requests from users or other parts of the network. Web services and platforms are particularly at risk, as hackers can target critical services by overwhelming the network with traffic. DDoS attacks are often used against large businesses or banks; they can also cause problems with a business reputation if users do not know why a website or service is down. For these reasons, learning how to stop and prevent these attacks is crucial to business operations and success.
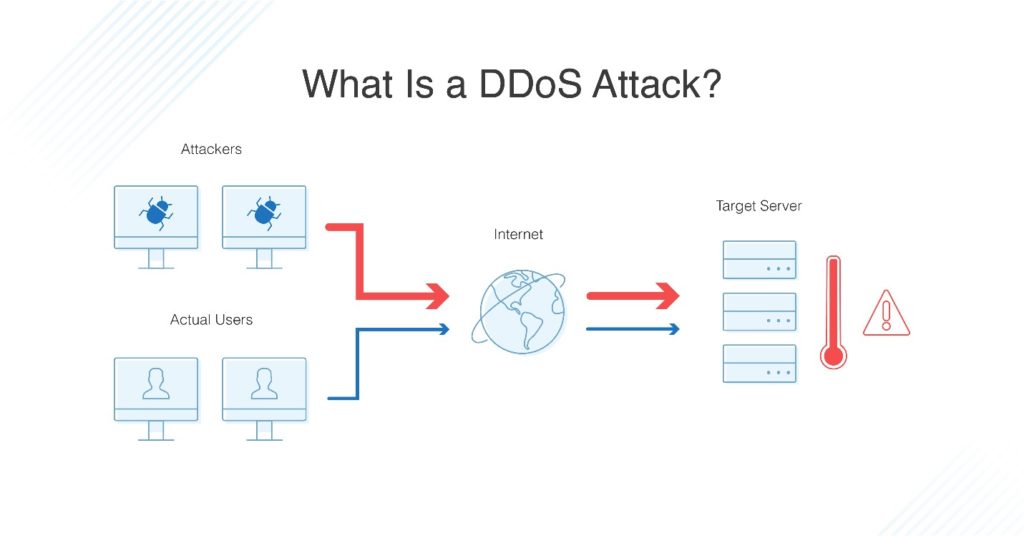
Types of DDoS Attacks
There are several types of DDoS attacks, and they target your network or systems in different ways. They include:
- Volumetric attacks. This is the most common type of DDoS attack. A bot overwhelms the network’s bandwidth by sending huge numbers of false requests to every open port. This means that legitimate requests are unable to get through. The two main kinds of volumetric attacks are called UDP floods and ICMP floods. UDP stands for User Datagram Protocol and is a protocol that relates to the transmission of data without checks. ICMP means Internet Control Message Protocol, and is a protocol used between network devices when they communicate with each other.
- Application-layer attacks. This type of DDoS attack targets the applications that users actually interact with. It interferes directly with web traffic by attacking the HTTP, HTTPS, DNS, or SMTP protocols. Often this type of attack can be hard to catch and troubleshoot, as it can mimic legitimate web traffic more easily.
- Protocol attacks. Protocol attacks are usually targeted at parts of the network that are used for verifying connections. They work by sending purposefully slow or malformed pings so that the network uses up a lot of memory trying to verify these pings. This type of attack can also target firewalls by sending large amounts of purposefully irregular data.
In some cases, attackers use DDoS attacks of all three types at once, to completely overwhelm a network and cause it to crash.
How to Prevent DDoS Attacks
It’s possible to prevent a DDoS attack with careful planning and security measures. The first thing to understand is that DDoS attacks can happen to anyone, even if your business is small or relatively unknown. While many attacks occur for political reasons, business reputation issues (such as a petrol company’s website being attacked after an oil spill), or because of trolling, even smaller businesses can be targeted by DDoS hackers. There are several measures that you can use to protect your business from a DDoS attack:
- Have a plan. To start, set up a DDoS response plan. Putting a plan in place means going through your system and working out any possible security vulnerabilities, as well as defining a clear response from your organization in the event of a DDoS attack.
- Allocate roles. You should have a defined response team in place for your data centers as well as in your network administration or IT teams. Make sure everyone knows their role and who to talk to if they need to escalate the situation and provide a list of internal and external contacts who can help.
- Install protection tools. Make sure you have appropriate protection tools installed for both your networks and your applications. This includes such key tools as firewalls, network monitoring software, anti-virus and anti-malware programs, as well as threat monitoring systems. With these, you can monitor your network baseline traffic and set up alerts for behavior that is out of the ordinary.
- Keep everything up to date. All these systems should be kept up to date, to make sure that any bugs or issues are fixed. Detecting threats as early as possible is the best way to prevent a DDoS attack from taking down important network infrastructures and affecting your end users.
Tools for Preventing DDoS Attacks
There are a few tools I recommend for preventing and stopping DDoS attacks.
1. Security Event Manager
For keeping track of network behavior and flagging threats before they become overwhelming, I like SolarWinds Security Event Manager (SEM).
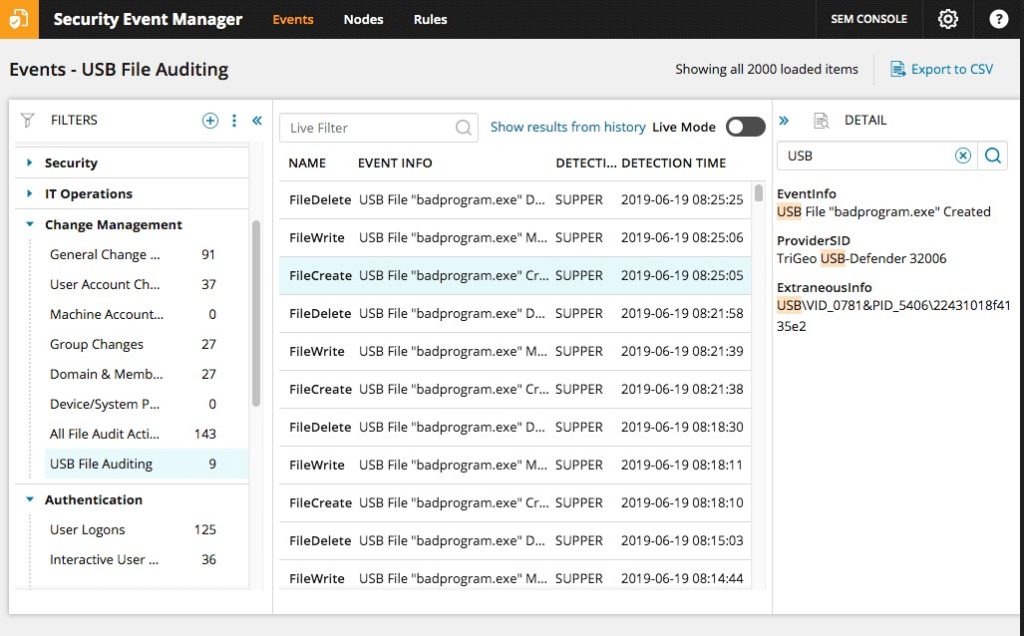
The ability to respond to a threat quickly is vital, as security initiatives can quickly become useless if they take too long to deploy. The SEM includes automated responses that can block a suspicious IP or USB, disable malicious devices or turn off their privileges, and kill applications that are behaving in unexpected ways. This means that time delays in dealing with something like a DDoS attack are minimized.
SEM also monitors file and USB integrity, so that if something doesn’t look quite right, it can be stopped in its tracks.
SolarWinds SEM is offered for free for a thirty-day trial. After that, you can look into pricing on a per-node basis.
2. Cloudflare
Cloudflare offers a resilient and scalable tool that combines multiple DDoS mitigation techniques into one solution. It prevents harmful and malicious traffic from getting through to your network while allowing the rest of your network to remain functional and high-performing. Cloudflare uses a reputation database to keep track of potential threats from attackers.
For businesses, Cloudflare costs $200 USD per month, but at an enterprise level you need to contact Cloudflare for a quote.
3. Imperva
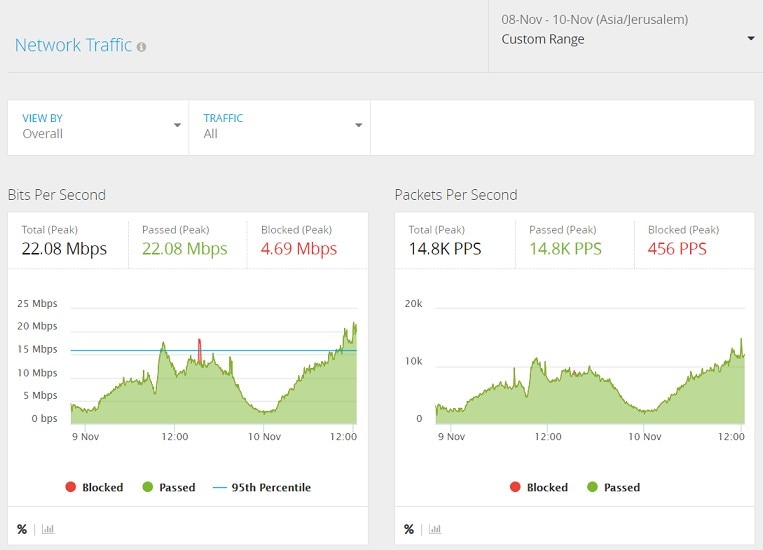
The Imperva DDoS protection tool keeps the entire network safe and shielded from attack by using high-capacity packet processing. It provides either always-on or on-demand DDoS protection, depending on what suits your business most, and also includes automatically updating dashboards that show attack traffic details. The main downside of the Imperva tool is that it is limited to DDoS attack protection.
Recommended Reading
In today’s environment, learning how to protect yourself from DDoS attacks is crucial to the security and success of your business. I recommend every business have network and data teams that fully understand how DDoS attacks work and have a clear plan or tool like SolarWinds Security Event Manager in place to help prevent and respond.
Find out more about DDoS attacks:
- Understanding Denial-of-Service Attacks – The Cybersecurity and Infrastructure Security Agency (CISA) security tips
- Read more about other types of security threats: Data Breach 101, Ransomware Prevention & Protection


