While it can sometimes seem SIEM systems compete with log management solutions, the two tools should ideally work together to provide a comprehensive data source. Together, they are essential for storing and examining a system’s data to troubleshoot potential problems and ward off security threats before they become serious breaches.
Here is everything you need to know about SIEM and log management to choose the right tools to protect your network. If you’d just like our recommendation for the best tool, consider SolarWinds® Security Event Manager for comprehensive log management capabilities.
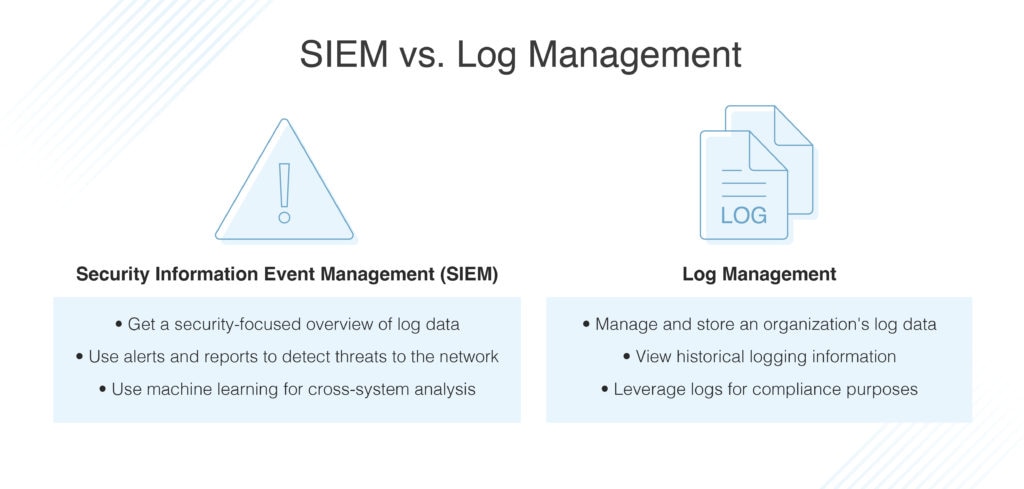
What Is SIEM?
SIEM is an acronym for Security Information Event Management. The term SIEM refers to the system, including log analysis and the products and software intended to offer admins a complete picture of all the activity occurring within a network. SIEM systems contain all of the functionalities of log management systems. However, SIEM systems also include security capabilities in three specific areas: security event management (SEM), security information management (SIM), and security event correlation (SEC). SEIM systems take a security-focused approach to log analysis.
To focus on security, SIEM systems collect, analyze, and report the log data from an entire network, which includes all applications, servers, and other endpoints within an operating system. A sound SIEM system will offer a complete overview of an organization’s entire network while also providing advanced approaches to detecting threats to the network that automatically produce alerts the moment a security breach is detected. Additionally, cutting-edge SIEM technology uses machine learning to process information to link seemingly disparate events within a network that, when examined together, might suggest a security threat.
However, it is crucial to understand SIEM cannot be a stand-alone security system. Instead, SIEM helps the security systems an organization has already adopted become more functional by offering advanced log analysis that provides greater knowledge about threats and vulnerabilities, enabling IT professionals to anticipate breaches before they occur.
Here are a few of the defining characteristics of an SIEM:
- Overview: An SIEM should provide a dashboard that offers an entire view of a network with additional access to log data
- Collation: Log information from across an organization should be stored in one central place alongside relevant contextual information
- Categorization: The log information collected within the SIEM should also be organized into easily referenced categories
- Connection: A good SIEM will use machine learning to compare event logs to scan for security threats
- Alerts: SIEMs should provide alerts via email, SMS, and SNMP if a security threat arises
- Priority: Alerts around potential security threats should be triggered in order of importance
- Reporting: To remain compliant, SIEMs should auto-generate reports based on stored log data
SIEM algorithms can identify even the most minor indicator of a threat. The algorithm’s attention to detail prevents minor breaches from snowballing into full-blown cyberattacks. Also, since these tools send out targeted alerts in response to detected threats, admins can respond much faster and even effectively stop attacks that are in progress.
Although SIEM is largely automated, it requires personnel to manage it and configure the system to meet your organization’s needs.
What Is Log Management?
While sometimes conflated with SIEM, log management simply refers to the processes by which the log data generated by an organization’s operating system is managed and stored. Log management tools collect myriad log data from many different sources and provide storage in a central location. By storing log data in this central location, IT professionals focused on security analysis can then analyze logs to detect potential threats. Log management tools can also provide detailed historical information around logs, allowing for the investigation of specific events and variables.
In addition to log data collection, data retention, log indexing, and reporting tools, one of the major assets of a log management system are it allows an organization to more quickly and easily search an extensive amount of log data. For organizations required to comply with laws and protocols such asHealth Insurance Portability and Accountability Act (HIPAA) or Payment Card Industry Data Security Standard (PCI-DSS) regulations, log management tools provide the benefit of embedded reports, which make the auditing process a bit less complicated.
Industry-leading log management tools focus on quickly collecting data from as many sources as possible, then providing IT professionals with the capabilities to search their data instantly while preserving a library of historical data. This data retention feature amounts to storing and categorizing millions of events per second, providing a complete picture of an organization’s data.
Similarities Between SIEM and Log Management
There are a few main similarities between SIEM and log management tools. For starters, they both use logs. However, while log management tools are focused primarily on logs, logs are only a part of the data included in SIEM systems. A second similarity is that both tools supply in-depth information about what is happening and keep detailed data records. Those records can then be used to find and address problems in real time, along with being used to investigate past problems in order to troubleshoot problems that could arise in the future.
Differences Between SIEM and Log Management
However, there are also many differences between SIEM and log management tools. While log management solutions are often less expensive than SIEM tools, log management also comes with a few disadvantages. One major issue from log management is the bottleneck that can sometimes occur when so much raw data is constantly collected and stored. Furthermore, log management does not always provide tools to automate the data. Because of this lack of automation, technicians are still responsible for manually keeping track of log data to deflect security threats. So, when compared to SIEM, log management generally requires significantly more time and effort.
But, while SIEM provides insights from a much wider range of data sources than log management, SIEM systems primarily focus on security. And though log management sometimes lacks the capabilities for preventing bottlenecks, log management tools can be useful for offering real-time insights that fall outside the spectrum of security and threat mitigation.
Benefits of Using Both Log Management and SIEMs Together
While SIEM and log management tools each have plenty of benefits on their own, using them in conjunction with one another is ideal. When used together, organizations benefit from the ability to record data, troubleshoot, and address security threats while monitoring for other issues that could potentially become problems.
Both tools can make productive use of log data independently. SIEMs curate, analyze and filter that data, and log management offers access to that data to categorize and filter that data through search functionalities. But, though SIEMs can help identify threats, log management can be a faster route to identifying threats, since these tools offer more robust insights into historical information, more easily examined through search capabilities.
And just as SIEMs can help address compliance issues with audit reports, log management offers a budget-conscious means of storing data over longer periods. So, while SIEMs can help to navigate threats using more complex datasets, log management tools can provide quicker alerts to real-time threats.
Used in conjunction with one another, SIEMs and log management tools can be used to provide a comprehensive analysis of systems using detailed libraries of data.
Examples of Tools for SIEM and Log Management
Kiwi Syslog for Log Management (Free Trial)
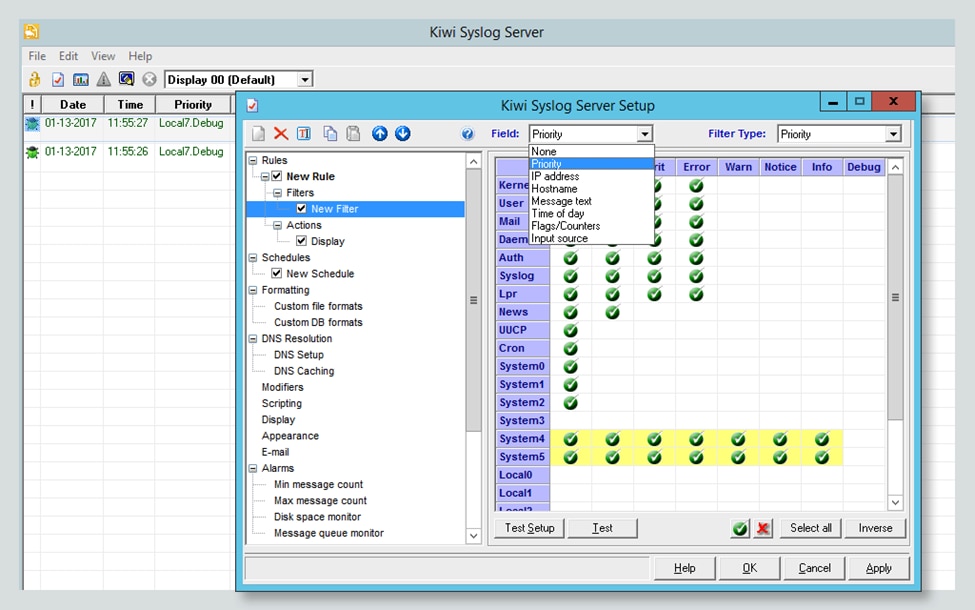
Kiwi Syslog® for Log Management from SolarWinds offers an excellent starting point for organizations looking for detailed log management and storage. Kiwi Syslog allows organizations to filter logs based on custom criteria and at-a-glance monitoring from its web console. Additionally, Kiwi Syslog enables admins to trigger alerts based on log messages and react to logs with automated responses. In addition, Kiwi Syslog provides industry-leading log storage, compression, and archival and retention reporting.
SolarWinds Security Event Manager for SIEM (Free Trial)
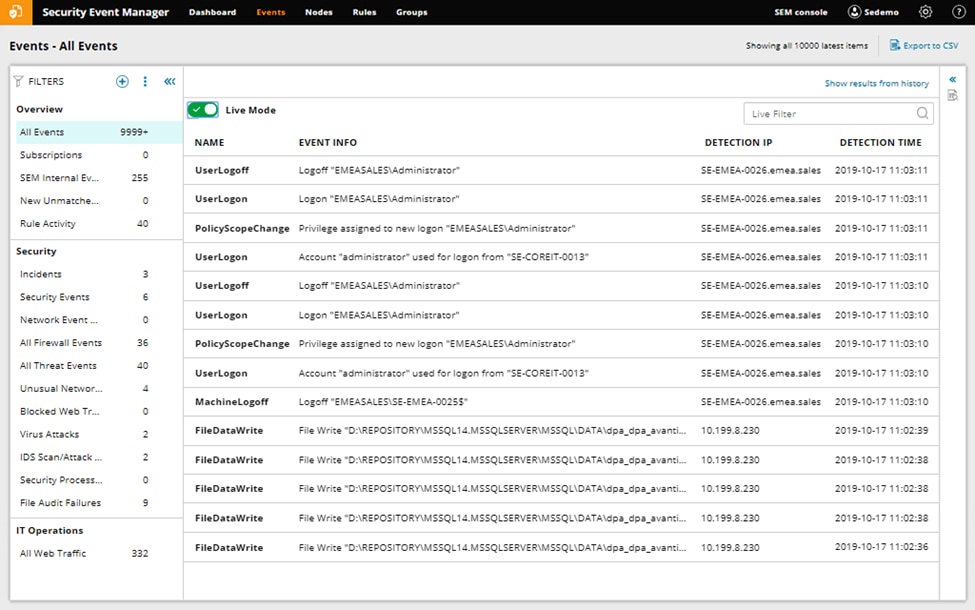
For organizations looking for top-of-the-line log management and SIEM capabilities, SolarWinds® Security Event Manager comes with hundreds of pre-built connectors that gather logs from various sources, quickly parsing their data before putting it into a common readable format. These features create a central location for teams to easily investigate potential threats, prepare for audits, and store logs.
Security Event Manager also includes features to quickly and easily narrow in on the logs that are necessary for security and compliance, such as visualizations, out-of-the-box filters, and simple, responsive text-based searching for both live and historical events. Scheduled search allows teams to save, load, and schedule their most commonly used searches. SolarWinds provides in-depth the differences between SolarWinds Security Event Manager and Kiwi Syslog Server.
Datadog for Log Collection and Management
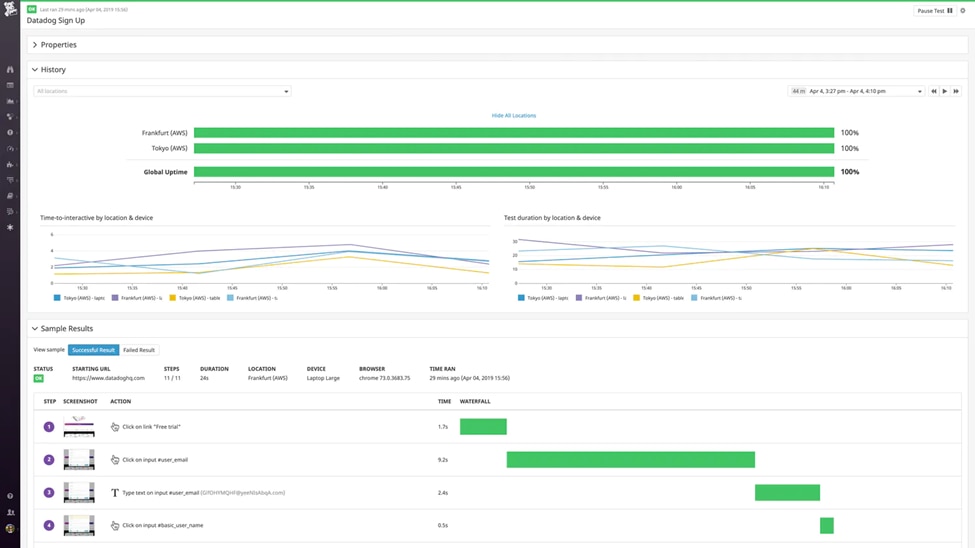
Built to service organizations of any size, from small to enterprise, Datadog® offers pre-built support and log processing templates. Offering budget-friendly log management options, Datadog helps organizations automatically detect unexpected outliers, anomalies, and errors without requiring admins to read every log file.
ManageEngine for Event Log Analysis
For organizations needing support for the Windows® event log format, ManageEngine® EventLog Analyzer helps to automatically collect, parse and analyze event logs from every Windows device connected to a network. These logs can come from any Windows source, whether a workstation, firewall, server, or hypervisor. EventLog Analyzer also allows admins to source from native log collection mechanisms or use the tool’s built-in log collecting agent, offering a complete view of networks customized to an organization’s needs.
Getting Started with SIEM or Log Management
According to the guide above, consider whether SIEM or log management capabilities would best fit your needs. Then get started with a free trial of one of the above tools, such as a 14-day free trial of Kiwi Syslog Server or a 30-day trial of SolarWinds® Security Event Manager. With a chance to try the tools, you may be able to figure out better whether SIEM or log management fits your organization’s needs.
