If you’re an admin, you’re likely already familiar with SolarWinds and its array of highly rated products suited for just about every aspect of IT management. But you might not be familiar with SolarWinds® Access Rights Manager (ARM). This software exists because it’s critical for you to manage and audit access rights across the system—the security and integrity of your data depends on it. In fact, before we get into the tool itself, let’s talk a bit more about why access rights management is critical for your organization.
Jump ahead to the main features:
SolarWinds Access Rights Manager Review
Active Directory Auditing and Permissions Management
Data Ownership and User Provisioning
Integration With Additional Tools
Free, 24/7 Support for 12 Months
Documentation and Reporting
Security Monitoring
What Is Access Rights Management?
Access rights management—also known as rights management—is all about authorizing users to work with certain resources in certain ways. Privileged access means users can do more with data, including editing or deleting it. Users with less privileged access to certain resources may only be able to view a folder or can’t see it at all. The purpose of defining controls in this way is to ensure what’s referred to as CIA: Confidentiality, Integrity, and Availability.
For admins, access rights management activities include the following:
- Permission Analysis: Admins need to be able to define which users have access to which data. For effective access rights management, you should view permission settings, track access paths, understand nested group permissions, and more.
- User Provisioning: Another key activity is user provisioning, which means creating and managing user accounts and groups. Admins must ensure current authorizations are correct, and if not, may need to reset passwords, deactivate accounts, modify Active Directory, or perform other similar tasks.
- Security Monitoring: Security monitoring is all about leveraging logs from across Active Directory, file servers, and other relevant tools. Admins can use those logs for reporting, alerting, and tracking key activities.
- Role and Process Optimization: For good access rights management, you need to be able to determine data owners throughout departments, so they can play a role in determining access. An efficient workflow doesn’t require one person to do everything—there should be a distributed approval process for access rights.
- Documentation and Reporting: The overall management process requires you to view and record critical information—which means you should be able to run configurable reports, share those reports with others, and have both current and historical visibility into access rights.
Why Is Access Rights Management Important?
Unsurprisingly, cybercrime is evolving, year-on-year, in an endless race against the development of new IT security technology. But not all cybercrime is committed by external bad actors. Sometimes, data breaches start on the inside—making effective access control critical for business security.
In large organizations, keeping sensitive data out of the hands of unauthorized (or malicious) personnel is critical to security. Companies may take every measure to ensure their personnel are trustworthy, but this is a difficult quality to verify. Even seemingly dependable and honest personnel could fall victim to ignorance of security policies or be tempted to sell confidential data to competitors.
Valuable data should be kept as protected as possible through the principle of least privilege—in other words, access rights should be set as restrictive as possible without limiting business function. Access rights management tools can help you certify your data is only accessible to individuals for whom access is a necessity. By minimizing access as much as possible, leaked data can be traced back to the source more easily, so you can identify the culpable party.
With concerns for security growing every day, there’s an increasing number and range of access rights management programs on the market, each with their own individual approach. This guide will mention some of the most popular and reputable access rights management tools but will focus on providing an in-depth review of SolarWinds Access Rights Manager.
SolarWinds Access Rights Manager Review
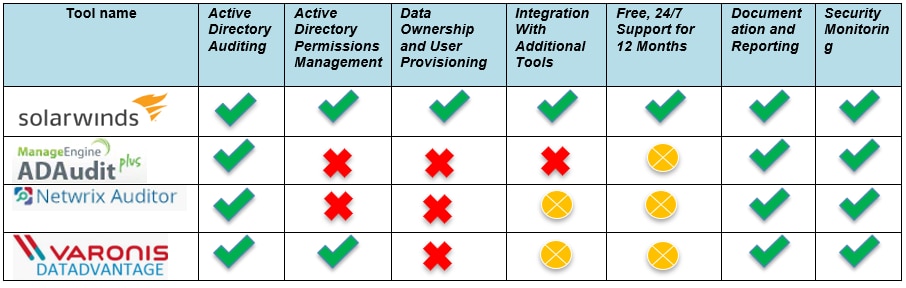
SolarWinds ARM is an access rights management tool offering users advanced capabilities in this area of IT security. ARM is for Active Directory-based networks and has been designed to make access managing, tracking, and monitoring processes easy, but nevertheless sophisticated. In this SolarWinds Access Rights Manager review, I’ll outline the best features of ARM, explaining why these features make it the best tool on the market for access rights management. I’ll also mention a few other access rights management programs, so you can get a sense of how ARM stacks up against some similarly ranked options, including Netwrix Auditor, ManageEngine ADAudit Plus, and Varonis DatAdvantage.
Active Directory Auditing and Permissions Management
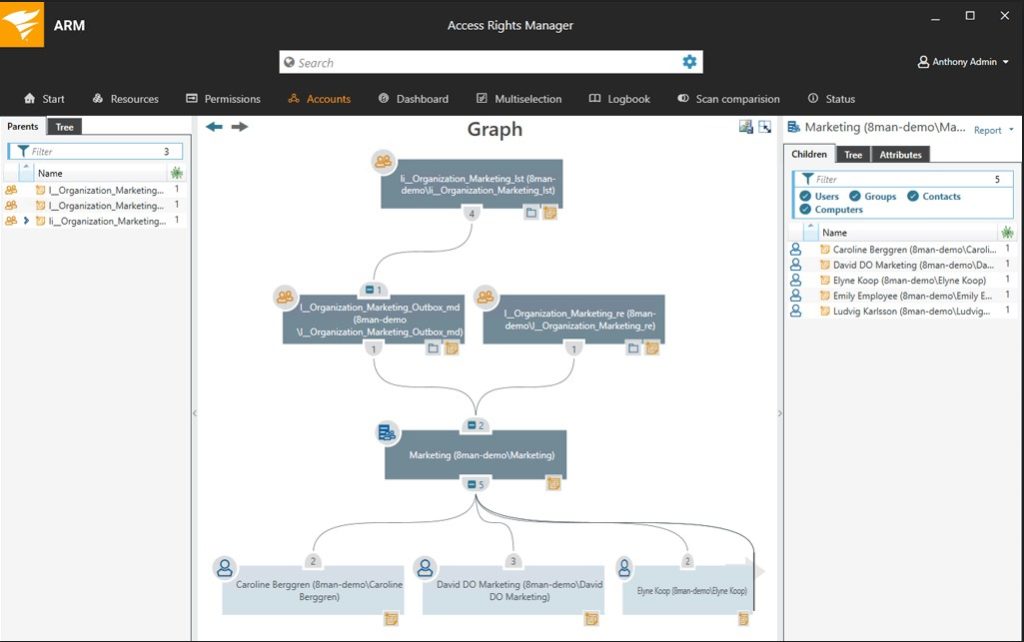
One of the things I like most about ARM is its Active Directory auditing and permissions management capabilities, which make it easy to analyze, audit, and monitor Active Directory and Group Policy. With it, you can view what changes have been made, who made those changes, and when they occurred. Plus, admins can create, delete, or edit permissions from one place. These Active Directory utilities include an impressive provisioning feature set, which lets you easily manage groups, permissions, users, and more.
ManageEngine ADAudit Plus: Though the standard edition of ManageEngine ADAudit Plus features Active Directory auditing functionalities, it doesn’t offer Active Directory permissions management.
Netwrix Auditor: This program provides monitoring utilities for Active Directory Permissions but falls short of ARM by not providing management functionalities.
Varonis DatAdvantage: This program provides monitoring and alerting functionalities for Active Directory, along with some management features.
Data Ownership and User Provisioning
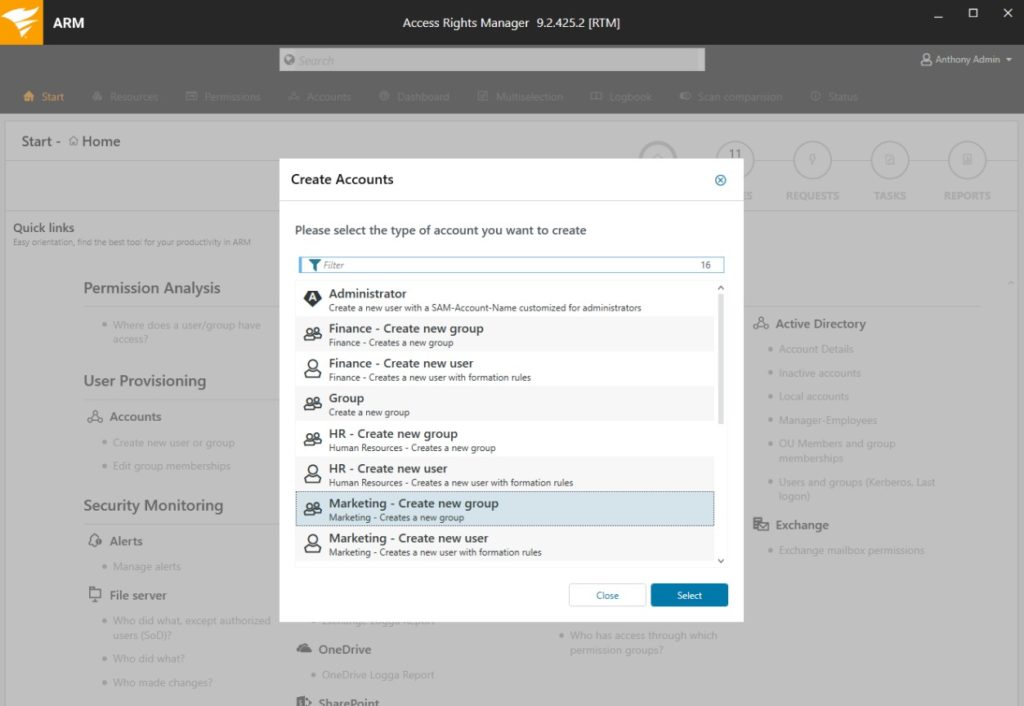
In ARM, a data owner is a person or position in an organization who knows which personnel require access to which resources and data. Ideally, a data owner is a department or division head with knowledge of who should have access to what resources in more detail than the administrator. With ARM, it’s possible to create organizational categories like folders or groups and assign them to data owners. Plus, admins can allow data owners to assign access rights by offering a self-service permissions portal. Instead of guessing on permissions levels or fielding access requests, admins can let data owners decide and can create a multi-level approval process.
ManageEngine ADAudit Plus: ADAudit Plus doesn’t offer users the ability to assign owners and doesn’t allow for permissions requests.
Netwrix Auditor: Netwrix Auditor doesn’t provide this functionality.
Varonis DatAdvantage: This program doesn’t let users assign data owners to organizational categories and doesn’t allow for permission requests.
Integration With Additional Tools
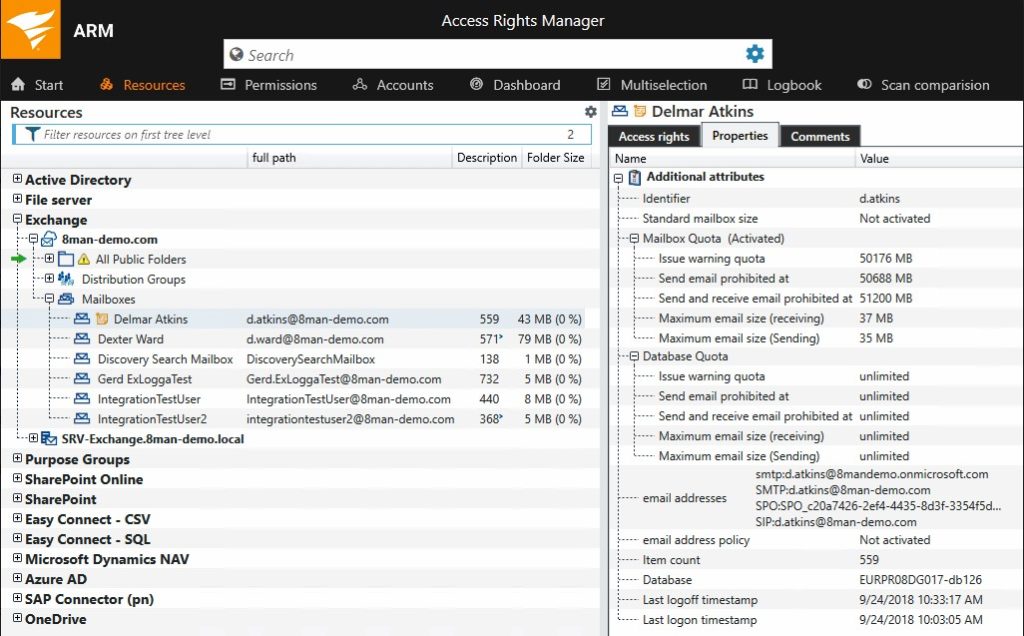
Access Rights Manager is all about integration for comprehensive access control. This goes beyond Active Directory alone—ARM can also help you monitor and manage Microsoft Azure AD, Microsoft SharePoint, Microsoft Exchange, and OneDrive. You can also audit and configure Windows file servers, NetApp filers, and EMC file share activity and permissions. With integrated management, it’s also possible to change file server permissions directly from ARM. Note: ARM also supports SAP R/3, allowing users to find authorization paths and use multiple authorizations.
ManageEngine ADAudit Plus: This tool is only for Active Directory and file server monitoring (and doesn’t allow you to manage file server permissions directly).
Netwrix Auditor: Doesn’t support SAP R/3, but includes monitoring (not managing) of Active Directory, Microsoft Exchange, file servers, and OneDrive.
Varonis DatAdvantage: A separate paid add-on lets you integrate with SharePoint, file servers, Exchange, and OneDrive. Doesn’t support SAP R/3.
Free, 24/7 Support for 12 Months
Surprisingly, one of the most noteworthy ARM features is its comprehensive and generous support offering. With SolarWinds, you can expect free, 24/7 telephone support. This is accompanied by upgrades for 12 months following the purchase of a license. In my view, as far as new software goes, having constant access to support can be invaluable.
ManageEngine ADAudit Plus: With ADAudit Plus, support is offered but only between Monday and Friday. This is on a 24-hour basis and the first year of the support license is free of charge.
Netwrix Auditor: Netwrix has some interesting support features, with a community of over 4,000 users on their forum. In terms of telephone support, they’re accessible 24 hours a day, Monday to Friday.
Varonis DatAdvantage: For 24/7 support with Varonis, you should expect to pay for their premium service, which also includes software updates.
Documentation and Reporting
If you’re looking specifically for the ability to report on access rights in your organization, ARM is a great solution. It takes typically a few clicks to create highly customizable reports or schedule reports to run at needed times. The reports are designed to be easy to understand and suitable both for internal stakeholders and external auditors. Because ARM documents changes across Active Directory, file servers, and your other integrated programs, you can rest assured you’ll have the insight you need to understand who has access where and what activities have occurred.
ManageEngine ADAudit Plus: This program focuses on Active Directory and server files, but allows you to create custom reports, including from archived data.
Netwrix Auditor: This program provides Active Directory out-of-the-box reports to help you meet compliance standards like HIPAA and SOX.
Varonis DatAdvantage: This platform offers typical reporting abilities—on trends, permissions, active and stale data, and changes within integrated programs.
Security Monitoring
To ensure security in how your organization handles access rights, you must be able to monitor all current access activity and view logs of past changes. This calls for data protection logging capabilities like those found in SolarWinds ARM. With ARM’s comprehensive log monitoring, you can trace changes across all integrated programs and if someone makes insecure changes to mailboxes, calendars, or contacts, you can quickly see the information. You can also send those logs to additional SIEM software. ARM offers helpful alerts for user accounts and groups, so you can dig into security issues more quickly.
ManageEngine ADAudit Plus: This program allows you to track object changes in real time and receive email alerts for security issues.
Netwrix Auditor: This software provides security alerts focused on individual users and threat patterns.
Varonis DatAdvantage: This tool includes some threat intelligence features to reduce false positive alerting.
Final Rating on SolarWinds Access Rights Manager
With insider attacks, malicious or accidentally, on IT security becoming increasingly common, having an effective access rights management system can be the difference between bank-breaking data breaches and a sense of security. Choosing between the available options isn’t easy, but SolarWinds ARM takes the lead as an access rights management solution.
The free, 24/7 support is an especially attractive feature, meaning when you’re getting used to the program and all its functionalities, you have access to constant support. With all the previously listed features in mind, I’d say SolarWinds ARM tops the ranks as the best access rights manager available today. For all these features, SolarWinds Access Rights Manager pricing stays competitive for business use. You can start with a fully featured 30-day trial to check it out for yourself.


