Using the Windows event log collector service (or an alternative third-party log collection solution) is a crucial aspect of system and network management. This guide will help you understand what the Windows Event Collector is, how the Windows event log collector service works, and how to collect Windows event logs with the Windows Event Collector.
It’s worth noting, however, data collection should have some limitations. An unnecessary surplus of data can easily overwhelm your logs, making error detection and event log analysis unnecessarily challenging. A log management solution like SolarWinds® Log Analyzer or a security information and event management (SIEM) solution like SolarWinds Security Event Manager (SEM) can help you optimize and centralize your log collection and management activities to prevent you from getting overwhelmed with data. A 30-day free trial of Log Analyzer is available here, and you can access a 30-day free trial of SEM here.
- What Is the Windows Event Collector?
- What Is a Windows Event Log?
- Information Types Stored by Windows Event Logs
- Using the Event Viewer
- How to Collect Windows Event Logs
- Centralized Log Management
- Getting Started With Windows Event Log Collecting
What Is the Windows Event Collector?
The Windows Event Collector service is responsible for managing continuous event subscriptions sourced from remote locations that support the Web Services-Management protocol. This includes event sources using the Intelligent Platform Management Interface (IPMI), hardware, and event logs. The Windows event log collector stores events that have been forwarded in a localized event log. If disabled or stopped, the service can no longer create event subscriptions, and forwarded events can’t be accepted.
Event collection enables administrators to retrieve events from a remote device and store the events in a fully centralized location. Events are stored on the collector computer’s local event logs. The event’s destination log path is a key subscription property. Event data is saved to the collector device’s event log, and any additional information related to event forwarding is added directly to the relevant event.
The Windows event log collector service requires manual startup, but it comes preinstalled. In the Windows Event Collector default configuration, it uses the NetworkService account to log in. The Windows Event Collector service is reliant upon two system components: a Windows event log and HTTP.
What Is a Windows Event Log?
To fully understand how to collect event logs from Windows, you first need to know what a Windows event log is and how it functions. A Windows event log provides an in-depth record of security, application, and system notifications stored by the operating system (OS). Administrators can use a Windows event log to diagnose potential system issues and anticipate future problems.
The operating system and application utilize these Windows event logs to account for important software and hardware activities, enabling the administrator to troubleshoot operating system problems. The Windows OS tracks and monitors specific events stored in its event log files, like security management, application installations, system setup processes, and any errors or issues.
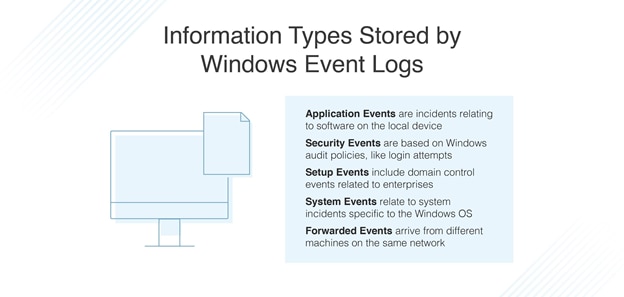
Information Types Stored by Windows Event Logs
The information types stored by Windows event logs cover five different event types/areas: security, application, setup, forwarded, and system events. These event logs are stored in the following folder: C:\WINDOWS\system32\config\. Here’s a brief breakdown of each of these event types.
Application Events
These events are incidents relating to software installed on a local device. For example, if an application like Microsoft Word experiences an error, the Windows event log generates an entry detailing this issue. The log entry will usually include the name of the application and why the application crashed, if known.
Security Events
A security event will store data based on audit policies for the Windows system. Typical security events might include resource access and login attempts. For instance, the security event log might store a new record when a user attempts to log in to a computer and the device tries to verify credentials.
Setup Events
This event type includes enterprise-centric events related to domain control—for example, log location following disk configuration.
System Events
A system event relates to Windows-specific system incidents, like device driver status.
Forwarded Events
Forwarded events, as their name suggests, arrive from different machines using the same network. This happens when the administrator wants to take advantage of a computer collecting multiple logs.
Using the Event Viewer
Windows also includes the Windows Event Viewer, where you can view Windows event logs. To access the Windows Event Viewer, click on the “Start” button, then select the search field and type “Event Viewer.” You can then choose and inspect the log you’re looking for. Windows will categorize events based on their level of severity. From least severe to most severe, the levels are as follows: information, warning, error, and critical.
Most logs are made up of information-based events. This means the log is purely informational, as the event took place without issue or incident. An example of a system-based information event is Event 42, Kernel-Power. This indicates the system is going into sleep mode.
An event with a warning level is always based on a specific event, such as insufficient storage space. These warning notifications can alert you to potential problems requiring immediate attention. As an example of a system-based warning, Event 51, Disk, refers to a machine drive error regarding paging.
If an event has an error level of severity, this means the device has failed in some way. Event 5719, NETLOGON, for example, is a system-based error designed to alert users when a device can’t configure a sufficiently secure session to the domain controller.
A critical event should be taken particularly seriously, as it can indicate a major issue. Event ID 41, Kernel-Power, for instance, is a critical system event occurring when a computer reboots but the shutdown isn’t clean.
How to Collect Windows Event Logs
To collect event logs from Windows, follow these steps:
- Click “Start,” then “Run,” then “eventvwr.msc.” This will open the Event Viewer
- Next, go to “Windows Logs,” then “Application, Security, and System”
- Filter the current log by dates
- Click “Save All Event As…”
- Save the logs
Centralized Log Management
The Windows Event Collector service is a useful tool, but there are other third-party solutions capable of helping your business make the most of their event logs and manage them appropriately.
SolarWinds Log Analyzer
SolarWinds Log Analyzer is an enterprise-grade tool built to help you consolidate, inspect, and alert on your critical Windows event log files and data.
With Log Analyzer, you can monitor Windows event log data in real time. This tool helps you reduce log “noise” and allows you to focus your attention on the most important log data. To save time and reduce the need for manual intervention, Log Analyzer lets you search logs and leverage out-of-the-box filters and tags to refine your log data and quickly identify issues.
This intuitive and powerful log management and monitoring tool is scalable, easy to use, and uses the SolarWinds Orion® Platform. This means it can be integrated with other SolarWinds products to provide a unified view of your IT infrastructure and associated logs.
A 30-day free trial of Log Analyzer is available for download.
SolarWinds Security Event Manager
If you’re looking for a more comprehensive centralized log management and monitoring solution to help you leverage your Windows event logs, SolarWinds Security Event Manager is another viable option. This is a SIEM solution with a more extensive range of features, including centralized log collection and normalization, integrated compliance reporting capabilities, automated threat detection and response, and built-in file integrity monitoring.
With 24/7 monitoring for suspicious activity and real-time responsiveness, SEM delivers a business-grade solution suitable for small and large companies alike. By combining log monitoring, management, and automated incident response, SEM allows users to achieve greater levels of insight into their infrastructure and logs. You can download a 30-day free trial of SolarWinds SEM here.
Getting Started With Windows Event Log Collecting
Understanding how Windows event log collecting works is just the start of making the most of your event logs and using them for troubleshooting purposes. With the right tools at your disposal, your company can start taking full advantage of its events logs, gaining invaluable insight and optimizing troubleshooting activities. SolarWinds Log Analyzer and SolarWinds SEM can help you easily and affordably realize these benefits. Access a free trial of Log Analyzer here and a free trial of SEM here.


