Collecting log data is an important part of network and system management, but more data isn’t always better. Excess data can overwhelm what you’re trying to accomplish, which is to detect errors or issues with your system. When you’re sorting through a mountain of logs, you can easily miss problems or fail to see major errors.
Having a centralized log management tool like Log Analyzer (which I provide an in-depth review of) delivers a way around this problem, as you can set it up to flag alerts for only the most important logs and issues. However, other noteworthy Windows event log tools, like Kiwi Syslog® Server and Graylog, may also be a good solution depending on your logging needs. I also share my thoughts on these programs below.
Why Is Centralized Log Management Important?
Windows Event Log Management Basics
How to Centralize Windows Log Management
Best Windows Log Management Tools
How to Choose a Windows Event Log Tool
Of course, you can still review your logs manually, but using a centralized system to highlight the critical information allows you to focus on the most important things, without getting swamped by data.
Why Is Centralized Log Management Important?
Each system and device on your network generates logs, which show all the events and transactions taking place. Basically, a log is a record of everything happening on the system. For Microsoft systems, these are called Windows event logs. For UNIX systems, they are called system logs or syslogs. The information you get from event logs is vital for several reasons. Since I focus my time supporting Windows machines, I wrote this guide with a focus on Windows event logs.
Windows Event Log Management Basics
Windows event log management is important for security, troubleshooting, and compliance. When you look at your logs, you can monitor and report on file access, network connections, unauthorized activity, error messages, and unusual network and system behavior.
But your systems produce tens of thousands of log entries every day. This volume of data is almost impossible to go through manually—and a significant portion of these entries will simply be showing successful, problem-free interactions and transactions.
For Windows systems, there are three types of event logs:
- System
- Application
- Security
The sheer volume of these logs can make it incredibly difficult to figure out what exactly is happening in your system. Each log also has a variable amount of data that can be displayed or captured, but you should be careful about setting it to gather the most detail possible, as this can end up overwhelming and crashing the entire system if the volume of logs is extremely high.
In addition, security events aren’t necessarily all stored in the “security” type logs; they can be in the system and application event logs as well. These are then broken down into text or binary logs, and many administrators elect to redirect all individual log files to the main syslog as a method of centralizing the process. If you’re trying to manually review all these log events, you’ll probably have a hard time discovering the ones with security or compliance issues, and as each day passes more data will accumulate, making it harder and harder to find problems. The cost of missing a problem can be huge and could end up taking your whole network down.
For example, some logs don’t look “unusual,” but the volume or pattern of the logs can indicate a problem. Finding this kind of issue is called anomaly detection, and it focuses on trying to detect, say, a high number of one type of log, even if the log data itself looks normal. A high number of logs within a short space of time could indicate someone is attempting a DDoS attack on your servers or is trying to gain information about (or gain access to) your database by pinging it repeatedly with different queries.
Without a centralized log management tool in place to monitor this, you might not even notice if the volume of logs is higher, as you’d be simply manually scanning for logs displaying an error.
How to Centralize Windows Log Management
If you can’t quickly pinpoint security and performance issues, you could be putting the business at risk of major financial, productivity, or reputation losses. For example, if a security problem arises and you don’t notice it, your business could end up with a data leak or theft of customer data, all because you missed some unusual network behavior. Alternatively, performance issues with your network could be slowing down your employees’ ability to work, and not quickly identifying logs showing a performance issue could mean this productivity loss continues for much longer than is necessary.
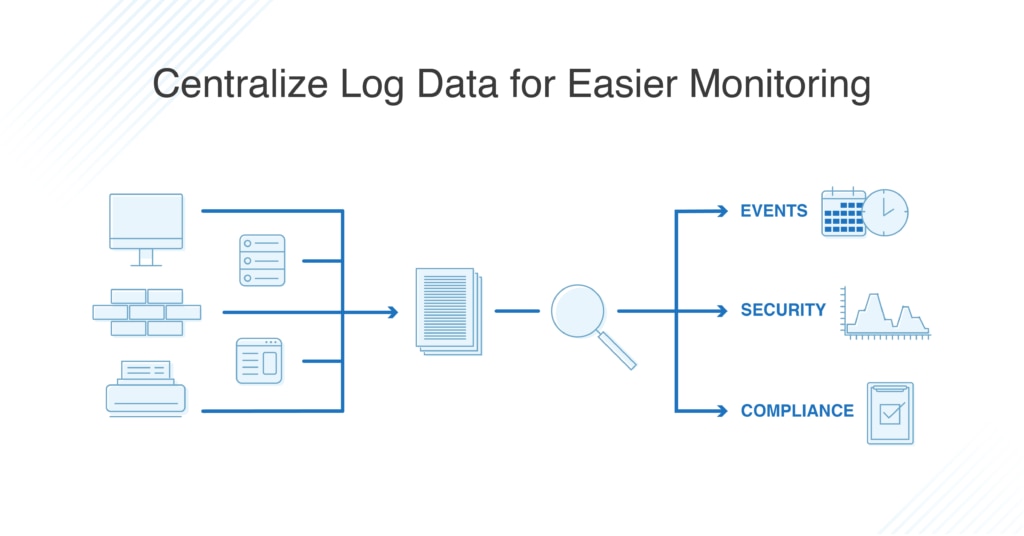
Instead of having all your log events spread across the system, with logs from each device recorded on that device alone, it’s important to centralize Windows event logs. Windows server centralized logging brings everything together and stores it in a central location. By using a centralized log server, Windows users increase the likelihood that the log events they’re looking at are reliable and representative of the key security or performance issues happening across the network.
In most cases, centralized log management is best done using a third-party application or software. With a very small network, manual log review is possible, but as soon as you have a high volume of logs to sort through, reviewing them manually exposes your network and business to huge amounts of risk.
Best Windows Log Management Tools
You can collect log events all you want, but the goal is to make use of them in the best and most effective way. Log management systems and tools collect all your logs and allow you to see security issues or performance problems, without all the noise. This means you can more quickly pinpoint and deal with any security issues or software problems.
Both paid and free log management tools provide varying degrees of analysis, so you can get better insights into your network behavior. In addition, many solutions include visualizations and graphs to help you understand what’s happening on your network and provide you with a clear picture of which log events indicate a risk to your systems.
Generally, you want to make sure the tool you choose:
- Can aggregate data
- Puts log events from different devices into the same format
- Alerts you to security problems or unusual events
- Comes with a set of predefined alerts
- Allows the administrator to set up their own events to trigger alerts
Whichever program you choose, make sure you configure it correctly to obtain the most important log event information. Your logging management solution should alert you when problems arise and should also be equipped to handle anomaly detection, enabling you to make informed decisions about how to protect and manage your network.
1. SolarWinds Log Analyzer
My favorite log management program is Log Analyzer, since it offers real-time log management, including syslog and SNMP trap data, and you can apply color-coded tags, so you can easily identify performance or security issues and sort or filter the logs.
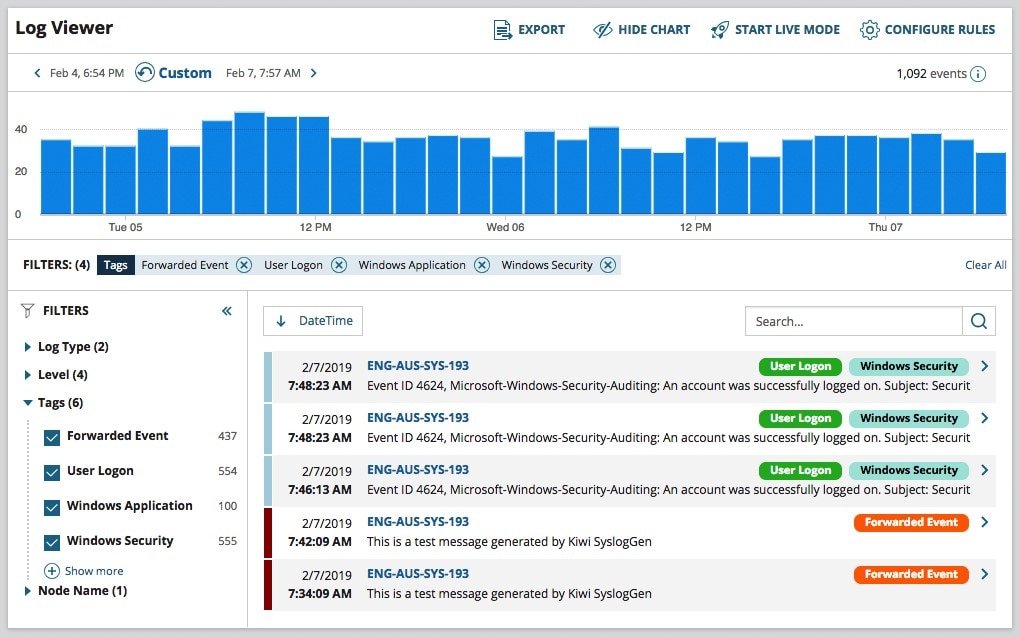
As a Windows system log analyzer, it works extremely well and integrates nicely with the Windows log system, including being able to identify if a Windows event contributed to a system slowdown or performance issue. These features enable you to quickly get to the root cause of an issue and avoid being overwhelmed by huge amounts of log data.
SolarWinds Log Analyzer also allows you to link in with security information and event management tools, so you can protect your business most efficiently. Importantly, it has great log retention capabilities: all data is exportable in CSV format, and you can keep a record of your log analysis and information for audit and security purposes. A free 30-day trial of Log Analyzer is available.
2. Kiwi Syslog Server
Kiwi Syslog Server is an affordable syslog messages and SNMP trap receiver solution with the ability to monitor Windows events. Using Log Forwarder for Windows (free tool), you can forward Windows event logs as syslog messages to Kiwi Syslog Server.
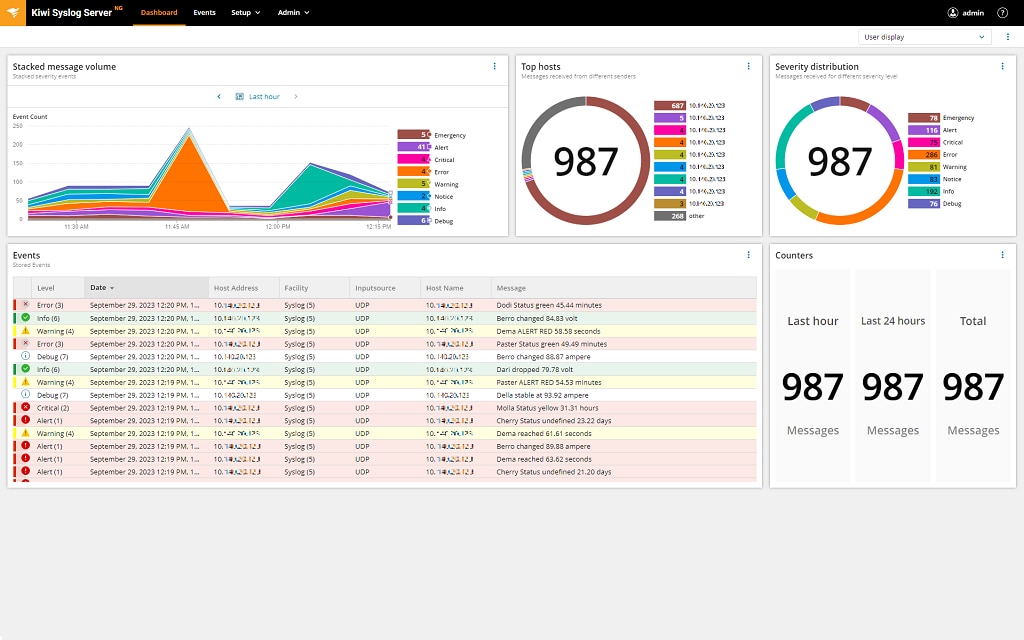
Once Kiwi Syslog Server receives the Windows events as syslog messages, you can apply the same log management actions to the Windows events as you would syslog messages.
These actions include:
- Triggering email notifications and reports
- Running scripts or external programs
- Logging to a file, Windows event log, or database
- Splitting written logs by device, IP, hostname, date, or other variables
- Forwarding syslog messages and SNMP traps to another host
Kiwi Syslog Server is designed to centralize and simplify log monitoring, receiving, processing, filtering, and managing syslog messages and SNMP traps from a single console across Windows devices, including routers, computers, firewalls, servers, and Linux/Unix hosts. Kiwi Syslog Server supports an unlimited number of sources and up to two million messages per hour on a single license. The tool can also automatically forward, store, and run an external program or API based on the syslog, SNMP traps, or Windows event log messages received.
When it comes to supporting security efforts, Kiwi Syslog Server can also schedule automated archival, cleanup, and logging syslog messages to disk, files, and ODBC-compliant databases to help you more easily demonstrate regulatory compliance.
In October 2023, SolarWinds released a new generation of Kiwi Syslog Server, bringing new UI including an interactive dashboard and significant performance and security improvements.
You can try Kiwi Syslog Server by downloading a free 14-day trial.
3. Graylog
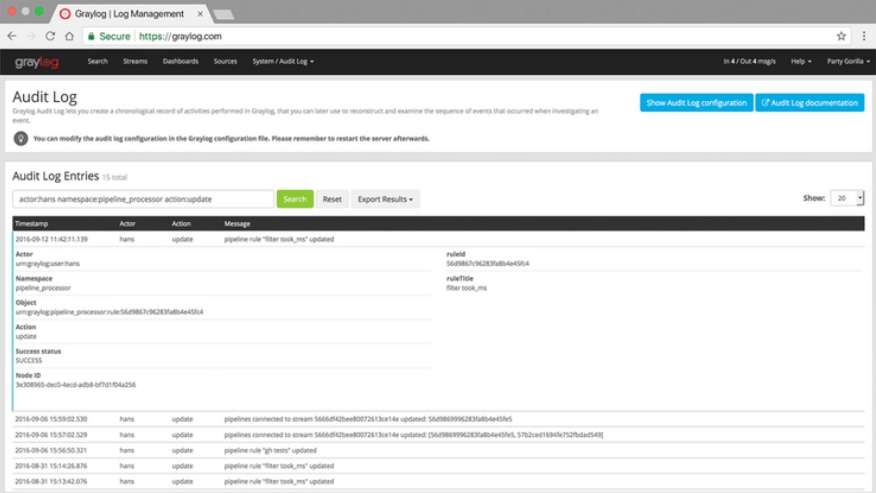
Another excellent tool is Graylog, a leading centralized logging management program for Windows. It has two versions: an open-source option and an enterprise-level solution. Both versions use simple and good-looking dashboards to help you see security issues and statuses with your applications.
How to Choose a Windows Event Log Tool
Whichever program you choose, make sure you configure it correctly to obtain the most important log event information. Your logging management solution should alert you when problems arise and should also be equipped to handle anomaly detection, enabling you to make informed decisions about how to protect and manage your network.


